Results 1 to 3 of 3
Thread Information
Users Browsing this Thread
There are currently 1 users browsing this thread. (0 members and 1 guests)
-
09-19-2015, 07:10 AM #1
Tracking a Bluetooth Skimmer Gang in Mexico
Don't use the ATMs if you go to Mexico!
Tracking a Bluetooth Skimmer Gang in Mexico
-Sept. 9, 12:30 p.m. CT, Yucatan Peninsula, Mexico: Halfway down the southbound four-lane highway from Cancun to the ancient ruins in Tulum, traffic inexplicably slowed to a halt. There was some sort of checkpoint ahead by the Mexican Federal Police. I began to wonder whether it was a good idea to have brought along the ATM skimmer instead of leaving it in the hotel safe. If the cops searched my stuff, how could I explain having ultra-sophisticated Bluetooth ATM skimmer components in my backpack?
The above paragraph is an excerpt that I pulled from the body of Part II in this series of articles and video essays stemming from a recent four-day trip to Mexico. During that trip, I found at least 19 different ATMs that all apparently had been hacked from the inside and retrofitted with tiny, sophisticated devices that store and transmit stolen card data and PINs wirelessly.
In June 2015, I heard from a source at an ATM firm who wanted advice and help in reaching out to the right people about what he described as an ongoing ATM fraud campaign of unprecedented sophistication, organization and breadth. Given my focus on ATM skimming technology and innovations, I was immediately interested.
My source asked to have his name and that of his employer omitted from the story because he fears potential reprisals from the alleged organized criminal perpetrators of this scam. According to my source, several of his employer’s ATM installation and maintenance technicians in the Cancun area reported recently being approached by men with Eastern European accents, asking each tech if he would be interested in making more than 100 times his monthly salary just for providing direct, physical access to the inside of a single ATM that the technician served.
One of my source’s co-workers was later found to have accepted the bribes, which apparently had only grown larger and more aggressive after technicians in charge of specific, very busy ATMs declined an initial offer.
My source said his company fired the rogue employee who’d taken the bait, but that the employee’s actions had still been useful because experts were now able to examine the skimming technology first-hand. The company tested the hardware by installing it into ATMs that were not in service. When they turned the devices on, they discovered each component was beaconing out the same Bluetooth signal: “Free2Move.”
Turns out, Free2Move is the default name for a bluetooth beacon in a component made by a legitimate wireless communications company of the same name. I also located a sales thread in a dubious looking site that specializes in offering this technology in mini form for ATM PIN pads and card readers for $550 per component (although the site claims it won’t sell the products to scammers).
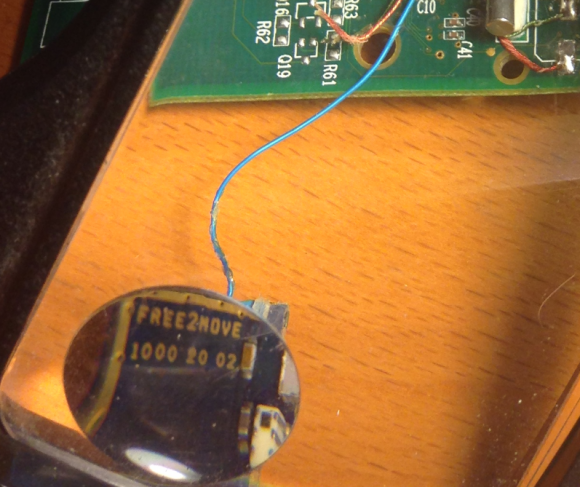
The Bluetooth circuit boards allegedly supplied by the Eastern Europeans who bribed my source’s technician were made to be discretely wired directly onto the electronic ATM circuit boards which independently serve the machine’s debit card reader and PIN pad.
Each of the bluetooth circuit boards are tiny — wafer thin and about 1 cm wide by 2 cm long. Each also comes with its own data storage device. Stolen card data can be retrieved from the bluetooth components wirelessly: The thief merely needs to be within a few meters of the compromised ATM to pull stolen card data and PINs off the devices, providing he has the secret key needed to access that bluetooth wireless connection.
Even if you knew the initial PIN code to connect to the Bluetooth wireless component on the ATM —the stolen data that is sent by the bluetooth components is encrypted. Decrypting that data requires a private key that ostensibly only the owners of this crimeware possess.
These are not your ordinary skimming devices. Most skimmers are detectable because they are designed to be affixed to the outside of the ATMs. But with direct, internal access to carefully targeted cash machines, the devices could sit for months or even years inside of compromised ATMs before being detected (depending in part on how quickly and smartly the thieves used or sold the stolen card numbers and PINs).
Not long after figuring out the scheme used by this skimmer, my source instructed his contacts in Cancun and the surrounding area to survey various ATMs in the region to see if any of these machines were emitting a Bluetooth signal called “Free2Move.” Sure enough, the area was blanketed with cash machines spitting out Free2Move signals.
Going to the cops would be useless at best, and potentially dangerous; Mexico’s police force is notoriously corrupt, and for all my source knew the skimmer scammers were paying for their own protection from the police.
Rather, he said he wanted to figure out a way to spot compromised ATMs where those systems were deployed across Mexico (but mainly in the areas popular with tourists from Europe and The United States).
When my source said he knew where I could obtain one of these skimmers in Mexico firsthand, I volunteered to scour the tourist areas in and around Cancun to look for ATMs spitting out the Free2Move bluetooth signal.
I’d worked especially hard the previous two months: So much so that July and August were record traffic months for KrebsOnSecurity, with several big breach stories bringing more than a million new readers to the site. It was time to schedule a quasi-vacation, and this was the perfect excuse. I had a huge pile of frequent flier miles burning a hole in my pocket, and I wasted no time in using those miles to book a hotel and flight to Cancun.
CANCUN
There are countless luxury hotels and resorts in Cancun, but it turned out that the very hotel I picked — the Marriott CasaMagna Hotel — had an ATM in its lobby that was beaconing the Free2Move signal! I had only just arrived and had potentially discovered my first compromised ATM.
However, I noticed with disappointment that for some reason all of my Apple devices — an iPhone 5, a late-model iPad, and my Macbook Pro — had trouble reliably detecting and holding the Free2Move signals from one of the two ATMs situated in the hotel lobby.
I decided that I needed a more reliable (and disposable) phone, so I hopped in the rental car for a quick jaunt down the road to the local TelCel store (TelCel is Mexico’s dominant mobile provider and a company owned by the world’s second-richest man — Carlos Slim). After perusing their phones, I selected a Huawei Android phone because — at around USD $117 — it was among the cheapest smartphones available in the store. Also, the phone came with plenty of call minutes and a semi-decent data allowance, so I could now avoid monstrous voice and data roaming charges for using my iPhone in Mexico.
Nearby the TelCel store was Plaza Caracol — a mall adjacent to a huge tourist nightlife area that is boisterous and full of Americans and Brits on holiday. The car parked in the mall’s garage, I pulled out my new Huawei phone and turned on its bluetooth scanning application. The first ATM I found — a machine managed by ATM giant Cardtronics — quickly showed it was beaconing two Free2Move signals.
Returning to the Marriott hotel, I found that the two Free2Move bluetooth signals showed up consistently and reliably on my new phone’s screen after about 5 seconds of searching for nearby bluetooth connections. The compromised ATM in the hotel also was a Cardtronics system.
At this point, I went to the front desk, introduced myself and asked to speak to the person in charge of security at the CasaMagna. Before long, I was speaking with no fewer than six employees from the hotel, all of us seated around a small coffee table overlooking the crystal-blue ocean and the pool. I explained the situation and everyone seemed to be very concerned, serious, asking smart questions and nodding their heads.
A man who introduced himself as the hotel’s loss prevention manager disclosed that Marriott had recently received complaints from a number of guests at the hotel who saw fraud on their debit cards shortly after using their ATM cards at the hotel’s machine. The loss prevention guy said the company responsible for the ATM — Cardtronics — had already sent someone out to review the integrity of the machine, but that this technician could not find anything wrong.
[SIDE NOTE: That technician may have only inspected the exterior of the machine before giving it a clean bill of health. Another explanation is that the technician that was sent to find skimming devices didn’t report their presence because he was the one who installed them in the first place!]
That same day, I phoned Giovanni Locandro, senior vice president of North American business development at Cardtronics. He told me the company conducts periodic “sweeps” in Mexico to look for skimming devices on its machines and that it was in the process of doing one at the moment down there, although he didn’t acknowledge whether he was familiar with the exact scheme I was describing.
“We are doing another sweep as we speak down there,” Locandro said. “We do random sweeps, especially in tourist areas to check for those devices. But we haven’t heard of any cards being cloned. Any devices we receive we take those to our internal security folks, and then we contact the authorities.”
I couldn’t dissuade these young ladies and many others from using the compromised machine on my second evening at the hotel.I showed the hotel folks the bluetooth beacons emanating from the ATMs in the lobby, and showed them how to conduct the same scans on their phones. Everyone roundly agreed that the technician had to be called again. But there were two ATMs in the lobby — one dispensing Mexican Pesos and another dispensing only dollars. How to know which ATM is compromised, they asked? Unplug them one by one, I replied, and you’ll see very quickly which cash machine is hacked because the bluetooth beacon would shut off.
Despite more head nods and a round of verbal agreement from the hotel staff that this was a good idea, to my surprise nobody at the hotel bothered to touch the machine for two more days. I watched countless people withdraw money from the hacked ATM; some of those I warned while in the lobby were appreciative and seemed to grasp that perhaps it was best to wait for another ATM; others were less receptive and continued with their transactions.
The next morning — after verifying that the hotel’s ATM was still compromised and trying in vain to hail the security folks again at the hotel — I headed out in the rental car. I was eager to visit some of the other more popular tourist destinations about an hour to the south of Cancun, including Playa del Carmen, Tulum and Cozumel. I wanted to see how many of those towns were hacked by this same skimming crew.
I was about to learn that the true scope of this scam was far larger than I’d imagined.
If you haven’t already done so, please check out Part II and Part III of this investigative series:
Tracking Bluetooth Skimmers in Mexico, Part II
Who’s Behind Bluetooth Skimming in Mexico?
http://krebsonsecurity.com/2015/09/t...ang-in-mexico/
-
09-19-2015, 07:16 AM #2
Tracking Bluetooth Skimmers in Mexico, Part II
I spent four days last week in Mexico, tracking the damage wrought by an organized crime ring that is bribing ATM technicians to place Bluetooth skimmers inside of cash machines in and around the tourist areas of Cancun. Today’s piece chronicles the work of this gang in coastal regions farther south, following a trail of hacked ATMs from Playa Del Camen down to the ancient Mayan ruins in Tulum.
As I noted in yesterday’s story, the skimmers that this gang is placing in hacked ATMs consist of two Bluetooth components: One connected to the card reader inside each machine, and another attached to the PIN pad. Both components beacon out a Bluetooth signal called “Free2Move.” The thieves can retrieve the purloined card and PIN data just by strolling up to the hacked ATM with a smartphone, entering a secret passcode, and downloading all of the collected information.
Having found two hacked ATMs in Cancun — including one in the lobby of my hotel (theMarriott CasaMagna) — I decided to check out other tourist destinations in the region. On the way to Tulum, I dropped in at the Barcelo, a huge, all-inclusive resort. The security guards at the front gate at the resort initially prevented me from entering the complex because I didn’t have reservations.
After 10 minutes of Googling on my phone and a call to the front desk, the guards seemed satisfied that I was interested in buying a day pass to the hotel’s various facilities. The gate lifted and I was let in. Five minutes later, the very first ATM I stopped at was found to be emanating the telltale Free2Move Bluetooth signals indicating a compromise.
No sooner had I finished documenting that hacked ATM than a security guard rode up on a motorcycle and asked if I was having trouble finding the day-pass desk. I replied that I’d be headed that way shortly.
The Barcelo security guard followed me closely as I returned to my rented Jetta and drove to a different building in the complex. Multiple security guards were beginning to shadow me at a respectful distance. I decided it was best to at least demonstrate that I had an intention of buying a day pass.
The Barcelo reception desk said the price would be USD $80 per person. Feigning shock over the hefty price tag, I declared loudly that I had to hit the hotel’s ATM to withdraw more cash in order to pay such exorbitant prices. That ATM also was beaconing the Free2Move Bluetooth signal, but the ATM itself returned errors stating that it was temporarily offline and unable to dispense cash.
That outage turned out to be the perfect excuse to visit a third ATM in the complex, as I again loudly explained to the security guy following a few paces behind. By this point, a much more stern and beefy guard began following me around on foot, his walkie-talkie buzzing periodically as I crossed the hotel campus. The third and final ATM I checked also was compromised. While I was sure there were more ATMs I hadn’t checked in other areas of the resort, I decided not to press my luck, and hopped back in the Jetta and resumed my journey to Tulum.
TULUMHalfway down the southbound four-lane highway from Cancun to the ancient ruins in Tulum, traffic inexplicably slowed to a halt. There was some sort of checkpoint ahead by the Mexican Federal Police. I began to wonder whether it was a good idea to have brought along the ATM skimmer I’d received from a source instead of leaving it in the hotel safe. If the cops searched my stuff, how could I explain having ultra-sophisticated Bluetooth ATM skimmer components in my backpack?
 A sign across the street from the police department in Tulum.
A sign across the street from the police department in Tulum.
After several nervous minutes of creeping traffic, I was waved on through the checkpoint and immediately felt silly for having gotten so worked up about it. However, upon my arrival 20 minutes later in Tulum — a popular tourist destination due to its proximity to the Mayan ruins — I would have a much closer encounter with the police.
As I pulled into the area where tour buses normally drop off passengers by the hundreds each hour, a number of men stood waving pamphlets and offering “Cheap!” parking that was anything but (or at least I thought at the time). Each was trying to direct me to park the Volkswagen in one of several large, dusty lots.
“I’ll just be about five minutes,” I said, stupidly putting the vehicle in park on the main street right in front of the tourist lot. The attendants just shook their heads and began hailing other newcomers.
The Tulum visit yielded another three ATMs within a few hundred meters of each other that were all emanating the Free2Move signal. But unfortunately, that jaunt took more than five minutes: When I returned to the Volkswagen, I found a parking ticket on the windshield and the parking attendants smirking, gleefully shouting in Spanish that I should have listened to them and parked in their lot.
The ticket wasn’t for that much money. More concerning, the license plate had been removed from the front of the car. At first I thought someone had stolen it, but one of the locals explained that this was a common practice used by Mexican police to ensure people actually pay quickly and — more importantly for them — locally, for their parking and traffic fines (and then some). The removal of the plates from the rented vehicle necessitated a stop at the police station at the entrance to the ruins; 20 minutes and the equivalent of $200 later, I was back in possession of the car’s front plate and headed back toward Cancun.
PLAYA DEL CARMEN
My next stop was Playa Del Carmen, another tourist destination popular with Americans but quite a bit less rowdy than the Plaza Caracol nightclub area in Cancun. A lengthy and sweaty stroll down Playa del Carmen’s leafy 5th Avenue revealed five more compromised ATMs pulsing out the Free2Move bluetooth signals.
After a late and thankfully enormous lunch at a local Argentinian steakhouse, I was feeling refreshed enough to continue to the third leg of the journey. With twilight approaching and colorfully lit signs blazing to life along the main tourist boulevard, a steady breeze set in and mercifully tamed the otherwise sticky and oppressive heat. It was time to board the hourly ferry to Cozumel.
COZUMEL
This speedy cruiser takes riders on a 45-minute ride to Cozumel, an island whose surrounding deep green-blue clear water makes it an immensely popular spot for scuba divers and tourists alike. By this time, the fitness tracker on my arm tapped my wrist to report that I’d massively overachieved my daily fitness goal: I’d walked almost 13 miles at that point, and I hadn’t even strolled around Cozumel yet.
 A compromised ATM in Cozumel.
A compromised ATM in Cozumel.
Once off the ferry in Cozumel, I commenced about two more kilometers of walking the main commercial road adjacent to the ferry dock. I found four more apparently hacked ATMs that were blasting out the telltale bluetooth signals.
I was physically drained, but very happy with the results of my reconnaissance missions, and glad to have been able to see so many places on the coast in such a short time.
I arrived back at the CasaMagna Marriott after midnight, exhausted but also interested in stopping by the ATM to see if any action had been taken. To my astonishment, someone had finally unplugged the Cardtronics peso machine that was stealing card data and PINs from users. With the power to the hacked ATM unplugged, the Free2Move beacons were no longer transmitting.
Unfortunately, I had to catch a flight home the next morning. But as the taxi dropped me off in front of the airport, I decided to check all of the cash machines in the terminal. The first one I found just inside the check-in area was clean (at least it didn’t appear to be beaconing bluetooth signals). The second ATM, however — situated next to an escalator and a currency exchange shop but before the security screening checkpoint — was broadcasting the now familiar bluetooth signal.
 This woman raced ahead of me as I was filming this compromised ATM. She was successful dissuaded from using it.
This woman raced ahead of me as I was filming this compromised ATM. She was successful dissuaded from using it.
As I prepared to document the compromise on my GoPro camera, an apparently American woman raced ahead of me and beat me to the ATM. Before she could enter her PIN, I turned off the camera and explained who I was. The traveler replied that she was in a great hurry. I told her that the ATM she was about to use would soon cause her checking account to be hijacked and drained.
The woman looked at me in what seemed to be exasperation for a moment, before withdrawing her card from the machine and heading wordlessly across the airport lobby to the other ATM.
Packing my camera gear back into its case, I carefully peered around the backside of the ATM. I noticed it was plugged into the wall facing the escalator.
As I rode the escalator up to the security gates and gazed down over the handrail, I could no longer see the darkened screen of the ATM, but somehow neither was the power cord still attached to the wall. Pulling out my new Hauwei phone for the last time, I smiled as the Bluetooth scanner tried in vain to find any beacons.
In case you missed it, please see the first installment in this series: Tracking a Bluetooth Skimmer Gang in Mexico. Later this week, we’ll take a look at the shadowy organization that appears to be responsible for this crime spree.
http://krebsonsecurity.com/2015/09/t...exico-part-ii/
-
09-19-2015, 07:26 AM #3
17
SEP 15
Who’s Behind Bluetooth Skimming in Mexico?
In the previous two stories, I documented the damage wrought by an organized crime gang in Mexico that has been systematically bribing ATM technicians to install Bluetooth skimming components that allow thieves to steal card and PIN data wirelessly. What follows is a look at a mysterious new ATM company in Mexico that sources say may be tied to the skimming activity.
One ATM company operating in the Cancun area whose machines were apparently free from these skimming devices is a relatively new entity called Intacash. This company’s ATMs positively blanketed many of the areas I visited, particularly in the heavy tourist and commercial areas of downtown Cancun and Playa Del Carmen. For example, in a single city block on Boulevard Kukulcan in Zona Hotelera — probably the busiest tourist spot in Cancun — I counted no fewer than ten Intacash ATMs, most of which were all less than a couple hundred yards from each another.
The experts I spoke with said they were mystified by Intacash’s strategy of placing so many cash machines in the region. Even for areas like Zona Hotelera with plenty of continuous foot traffic, adding so many cash machines in such a small space produces diminishing returns.
Intacash ATMs positively blanket the most busy area of downtown Cancun and in very tight proximity to one another.
Two different ATM experts familiar with rates charged to place ATMs in the area and who asked to remain anonymous said there is no way Intacash could afford the rent required to place so many ATMs in such close proximity on public property and still turn a monthly profit. No way, that is, unless the company had a different profit motive in mind.
Intacash is a relative newcomer to the ATM scene in Mexico, bringing its first ATMs online there a little more than a year ago. It’s not at all clear who runs or owns Intacash, and there is precious little public information available about this company.
Intacash.com, registered in early 2014, consists of just four Web pages. There is no contact information for the firm on its site, which to this day has exactly zero sites linking in to it. From its inception, the site’s registration records have been hidden behind WHOIS privacy protection services. Intacash hosts its sites along with more than 6,000 other sites on a shared server at GoDaddy.com (for security and other reasons, financial institutions and service providers more typically spring for their own, dedicated servers).
Despite the presence of nearly 70 Intacash ATMs in Cancun, Playa Del Carmen, Tulum and other tourist areas in the Yucatan Peninsula, this company seems to have gone out of its way not to be noticed online. What’s more, a review of the text on Intacash.com suggests that much of the Web content on the site has been copied verbatim from other sites that preceded Intacash’s existence on the Internet.
Multiple emails sent to the contact addresses and forms on Intacash’s Web site went unreturned. Intacash’s sponsor bank in Mexico – Multiva — also did not respond to messages seeking comment.
THE INTACASH CONNECTION
Why was I so keen to learn more about Intacash? My source in the ATM industry who tipped me off about the Bluetooth skimming activity showcased in the first two stories here said his technicians began receiving bribes to let strangers install skimming components inside their machines around the same time that Intacash came online in Mexico. By early this year, all of my source’s ATM technicians had reported being approached by one of two guys who were trying to buy access to ATMs.
The employees who reported these incidents to my ATM industry source said the men had Eastern European accents.
Several of my source’s employees later identified the men who approached them after managing to locate their profile pages on Whatsapp, a popular mobile messaging service.
“My partner was at a meeting with the operating manager of [a major hotel] in Cancun, doing his sales pitch,” my source recalled in a recent interview. “And the fellow at the hotel told my guy that just the day before he’d been approached by another ATM company, and that the guys were Eastern European.”
My source said that, when pressed, the hotel manager acknowledged that the other company was indeed Intacash. My source said his business partner happened to have bookmarked on his smartphone the Whatsapp profiles of the men who’d tried to bribe his technicians, and that he opened the profiles one by one and showed them to the hotel manager.
“My partner asked, ‘Just out of curiosity was it one of these guys?'” my source said. “The hotel manager said why, yes it was.”
ANALYSIS
Intacash may in fact be totally above-board. But beyond the above-mentioned circumstantial oddities, there are other clues that would suggest something is not quite right at Intacash.
For example, in my wanderings around Cancun and elsewhere in the region, I used a low-balance debit card to check out multiple Intacash ATMs — each of which offers customers the option to withdraw Mexican Pesos or U.S. Dollars. Curiously, every time I used one of these machines to make small Peso withdrawals, I received a paper receipt. Each time I took out dollars, I got no receipt (this behavior was the same across multiple Intacash machines).
In about one-third of the cases, after entering my PIN, the transactions were canceled without explanation (no receipt was issued in those failed transactions either). When I returned home and began researching this, it turns out I was not the only one who noticed this pattern.
Even more curious, Intacash ATMs charge nearly twice as much as virtually any other ATM company in the region for withdrawing funds — often 10 percent to 15 percent of the value of the withdrawal. I would imagine that a large percentage of consumers who put their cards and PINs into an Intacash ATM would cancel the transaction and look for another machine after seeing that withdrawing $100 would cost them $15.
I began to wonder whether it was possible that Intacash was a company essentially set up to capture card and PIN data?
Phony ATM companies are certainly not unheard of, even in the United States. Back in 1993, U.S. federal agents arrested two men in Connecticut suspected of stealing more than $100,000 by placing fake ATMs. In the Connecticut case, the fraudsters simply placed fake ATMs that were devoid of cash. That may sound like a clever scheme, but the lack of cash in those machines is what quickly tipped off investigators that something was fishy about the ATMs.
Well, hang on a moment, you say: Wouldn’t selling or otherwise exploiting ATM/debit cards all stolen from one ATM company’s machines quickly draw unwanted attention from the banks, Visa and MasterCard to that company? You bet: Anyone in charge of such a fraud operation would want to spread their card-cloning scam across as many ATMs as possible: The more ATMs and the more ATM companies involved, the harder it is to trace the source of the fraudulent transactions. And here we come full circle to the cash machines in and around Cancun that were compromised with internal Bluetooth skimmers.
In addition, the absence of receipts and the propensity for ATMs to randomly “cancel” transactions after users insert their cards and enter their PINs would make it easier for a large card cloning operation to hide much of their activity. For example, if the transaction is cancelled before it reaches the processing switch of the customer’s bank, there would be absolutely no record of the customer using the ATM, despite the card data and PIN being compromised
How much could a fake ATM operation with 70 ATMs pull in each month? Various ATM companies I spoke with in the process of reporting and writing this story said — depending on the location — a typical machine may need between 300-500 customers per month to become profitable.
If we take the low end of that, and assume that some customers (let’s say 30 percent for rounding purposes) will be repeat customers using the same card and PIN, that’s conservatively 200 cards per month per machine. Even if the average checking account tied to each ATM card had just $100 in it, that’s $20,000 per machine per month, or — again, very conservatively — about $1.5 million across all 70 machines per month.
THE KEY ROLE OF ATM TECHNICIANS
Several readers have asked why experts are so certain that ATM company installers — not random crooks — had to have been responsible for installing the Bluetooth card and PIN pad skimmers in the compromised devices I found in Mexico. The explanation has to do with the reality that modern ATMs are designed to protect the security and privacy of the user’s PIN once it is entered into the system, and more importantly to protect the integrity of the PIN pad itself.
If a random thief were to break into an ATM and attach electronic devices capable of intercepting PIN codes entered by customers, the ATM would simply cease to function properly after that. When ATM makers or banks wish to update software or hardware on their machines, they must subsequently input a special cryptographic key. That key — known as the “terminal master key,” is good for that machine and that machine only — and it comes directly from the manufacturer or the bank.
One of the Bluetooth PIN pads pulled from a compromised ATM in Mexico. The two components on the left are legitimate parts of the machine. The fake PIN pad made to be slipped under the legit PIN pad on the machine is the orange bit, top right. The Bluetooth and data storage chips are in the middle. The antenna for the Bluetooth board can be seen trailing off the right side of the photo.
Some banks and ATM companies go a step further, requiring all such changes to be approved by two authorized personnel. This dual-authentication approach — the use of two keys, each assigned to different personnel who must approve physical and software changes to the ATM — is designed to short-circuit any attempts by rogue ATM installers to do what’s apparently been done in many Mexican ATMs. And it is likely that the victim ATMs documented in this series were not following this best practice.
Also, some readers have asked whether there was anything in particular about Mexico that made ATMs there more likely to be victimized by sophisticated ATM fraudsters who bribe their way into cash machines. I think the answer is yes and no. For one thing, the risks of doing this in the United States are far higher. It seems likely that anyone convicted of hacking cashing machines this way in the United States would be facing federal fraud charges and serious jail time here if convicted.
In Mexico, it seems unlikely such a person would ever even be prosecuted, let alone jailed for any length of time. Security experts I spoke with in Mexico said it is exceedingly easy to buy one’s way out of prosecution or jail in Mexico if one has the right amount of cash, and certainly an enterprise in charge of a skimming business or a fake ATM empire would indeed have plenty of that.
But in practice, this scheme could happen anywhere in the United States, and I would fully expect it to migrate north of the border soon (if it hasn’t already). There are no doubt plenty of ATMs that allow the swapping in of hardware without requiring two people to sign off on the change, and people here are obviously susceptible to bribes. It’s also worth noting that technicians here and abroad alike can be coerced into cooperating with thieves via non-financial means, such as extortion or threats to their personal safety and/or that of their families.
Finally, many readers have asked if any of the skimmed ATMs I found in Mexico were bank-owned and operated ATMs, or machines on the premises of bank properties. None of them were: All were free-standing cash machines owned and operated by private companies.
If you haven’t already seen them, please check out the first two stories in this series:
http://krebsonsecurity.com/2015/09/w...ing-in-mexico/
Similar Threads
-
MEXICO: News of another U.S. gun-tracking program stirs crit
By AirborneSapper7 in forum illegal immigration News Stories & ReportsReplies: 8Last Post: 10-10-2011, 08:57 AM -
The Serious Tracking of Americans Begins: gold coin tracking
By AirborneSapper7 in forum Other Topics News and IssuesReplies: 4Last Post: 07-18-2010, 08:43 PM -
World's largest skimmer arrives in Gulf
By JohnDoe2 in forum Other Topics News and IssuesReplies: 3Last Post: 07-01-2010, 04:58 PM -
US: No Central Tracking of Americans Murdered in Mexico
By zeezil in forum illegal immigration News Stories & ReportsReplies: 5Last Post: 06-15-2008, 05:08 PM -
Wake County Schools To Begin Tracking Gang Members
By Scubayons in forum illegal immigration News Stories & ReportsReplies: 0Last Post: 08-19-2005, 10:58 AM


 1Likes
1Likes LinkBack URL
LinkBack URL About LinkBacks
About LinkBacks







 Reply With Quote
Reply With Quote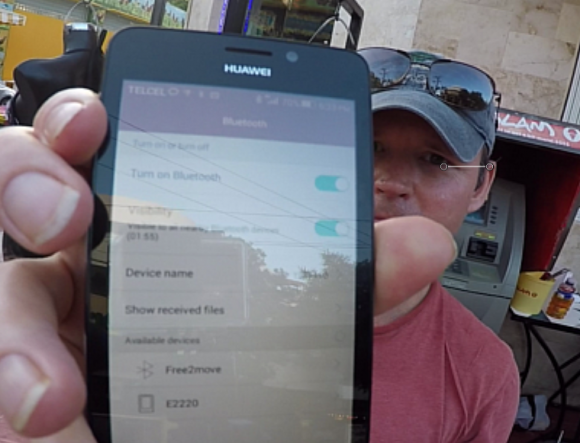




1,300 Migrants swarm NYC’s City Hall over false rumor of green...
04-25-2024, 07:27 AM in General Discussion