Results 301 to 310 of 582
Thread Information
Users Browsing this Thread
There are currently 1 users browsing this thread. (0 members and 1 guests)
-
07-31-2013, 03:56 PM #301






July 31, 2013 | By Hanni Fakhoury
New Court Ruling Makes it Easier for Police to Track Your Cell Phone
A Fifth Circuit Court of Appeals ruling this week will make it easier for police to track your movements through your cell phone after the court decided police aren't required to obtain a search warrant to track you.
The case involved a 2010 law enforcement request to obtain 60 days of cell phone location records from two cell phone companies. The government wanted to identify which cell phone towers a particular phone number had connected to in order to place a suspect at the scene of a crime, and submitted a request under the Stored Communication Act ("SCA") for access. The magistrate judge denied the request, understanding that records revealing your daily movements could show where you worship, what your medical conditions might be, and what political issues might interest you, not to mention who your friends and family are. It therefore rightfully ordered the government to apply for a search warrant supported by probable cause before accessing this sensitive data.
Naturally unhappy with the magistrate's conclusion, the government appealed first to the district court, which agreed with the magistrate, and then to the Fifth Circuit. Since there was no opposing party (the suspect wasn't informed of the surveillance and no criminal case was filed) we stepped in with the ACLU and other organizations, filing an amicus brief and participating at oral argument (WMA), urging the court to uphold the lower court opinions and rule a search warrant is needed in order to access cell tracking data since the data reveals extensive information about where a person goes and who they associate with.
In a misguided 2-1 decision, the Fifth Circuit reversed the privacy-protective lower court opinions and instead ruled the government did not need a search warrant to access historical cell site records. That's because the court focused not on what the data revealed -- a person's location over an extended period of time -- but rather on who owned and generated that data: the cell phone providers. Since these records were owned and created by the phone providers, the user has no expectation of privacy in them and thus no search warrant was needed to access that data. The court did not address whether people have a reasonable expectation of privacy in their movements and made clear its decision only concerned obtaining historical cell site records when a user makes or ends a phone call. In a compelling dissenting opinion, Judge Dennis noted that the constitutional issues were tricky ones and given the Supreme Court's reluctance to weigh in on the interplay between the Fourth Amendment and new technologies, the SCA should and could be interpreted to require a search warrant before police can access location data from a cell phone provider.
Throughout the majority opinion is the misguided belief that a user understands and voluntarily chooses to reveal their location to the cell phone provider and ultimately the government through the user's own free will. The court believed that your location is voluntarily turned over when the "user makes a choice to get a phone, to select a particular service provider, and to make a call." But common sense and experience calls this premise into question. Just last week the New Jersey Supreme Court ruled that police needed to get a warrant to track a person through their cell phone under under its state constitution. It noted a cell phone is "an indispensable part of modern life" and that "people buy cell phones to communicate with others, to use the Internet" but "no one buys a cell phone to share detailed information about their whereabouts with the police." While a cell phone user may naturally understand that they've given their location to the provider for a discrete and limited purpose -- to connect their phone call -- that is not the same as giving the government a detailed map of their movements. The New Jersey Supreme Court stated the "obvious" issue clearly: "cell phones are not meant to serve as tracking devices to locate their owners wherever they may be."
More generally the "third party doctrine" -- the idea you have no expectation of privacy in information turned over to third parties -- is dangerously eroding our Fourth Amendment protection at a time when cell phone companies and Internet service providers are stockpiling extensive personal information about all of us. Last year, Justice Sotomayor of the U.S. Supreme Court sounded the alarm in her concurring opinion in United States v. Jones writing the doctrine was "ill suited to the digital age, in which people reveal a great deal of information about themselves to third parties in the course of carrying out mundane tasks." But courts have been reluctant to follow Justice Sotomayor's cue in reexamining the doctrine. Its been up to state courts and legislatures to proactively protect people's location privacy while federal courts are reluctant to act, relying on the third party doctrine to reject a search warrant requirement for the data.
As more challenges to the constitutionality of cell site collection make their way through the federal courts, we hope judges will understand the only way to ensure our constitutional rights are protected is to find that the sensitive location information revealed by cell tracking deserves Fourth Amendment protection notwithstanding the fact the records are created and stored by cell phone providers.
Privacy
Cell Tracking
Locational Privacy“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
-
07-31-2013, 03:59 PM #302
July 31, 2013 Huge Global Coalition Stands Against Unchecked Surveillance
https://www.eff.org/press/releases/h...d-surveillance
100+ Organizations Sign Thirteen Principles to Protect Human Rights
San Francisco - More than 100 organizations from across the globe – including Privacy International, Access, and the Electronic Frontier Foundation (EFF) – are taking a stand against unchecked communications surveillance, calling for the governments around the world to follow international human rights law and curtail pervasive spying.
The coalition of groups have all signed the International Principles on the Application of Human Rights to Communication Surveillance – 13 basic principles that spell out how existing human rights law applies to modern digital surveillance. Written in response to the increasing number of government surveillance standards that focus on law enforcement and "national security" priorities instead of citizens' rights, the principles include advice on how surveillance laws should respect the law, due process, and include public oversight and transparency. Current debates over government surveillance are often limited by outmoded definitions of content versus metadata, or stored data versus data in transit. The principles released today concentrate on the core issue: how human rights protect all information that reveals private information about an individual's communications.
"It's time to restore human rights to their place at the very heart of the surveillance debate," said EFF International Director Danny O'Brien. "Widespread government spying on communications interferes with citizens' ability to enjoy a private life, and to freely express themselves – basic rights we all have. But the mass metadata collected in the U.S. surveillance program, for example, makes it extraordinarily easy for the government to track what groups we associate with and why we might contact them. These principles announced today represent a global consensus that modern surveillance has gone too far and must be restrained."
The organizations signing the principles come from more than 40 different countries. The principles will be used to advocate for a change in how present laws are interpreted, and new laws are crafted.
"International human rights law binds every country across the globe to a basic respect for freedom of expression and personal privacy," said EFF International Rights Director Katitza Rodriguez. "The pervasiveness of surveillance makes standing up for our digital rights more important than ever. And we need those rights to survive in a digital world, where any state can spy on us all, in more detail than ever before. We know that surveillance laws need to be transparent and proportionate, with judicial oversight, and that surveillance should only be used when absolutely necessary. Everything we've heard about the NSA programs indicate that they fall far outside these international human rights principles."
For the International Principles on the Application of Human Rights to Communications Surveillance:
https://necessaryandproportionate.org/
For more on how the principles were developed:
https://www.eff.org/deeplinks/2013/0...r-human-rights
Contacts:
Danny O'Brien
International Outreach Coordinator
Electronic Frontier Foundation
danny@eff.org
For Spanish-language interviews:
Katitza Rodriguez
International Rights Director
Electronic Frontier Foundation
katitza@eff.org
Related Issues
j“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
-
07-31-2013, 04:51 PM #303
XKeyscore: NSA tool collects 'nearly everything a user does on the internet'
• XKeyscore gives 'widest-reaching' collection of online data
• NSA analysts require no prior authorization for searches
• Sweeps up emails, social media activity and browsing history
• NSA's XKeyscore program – read one of the presentations
- Glenn Greenwald
- theguardian.com, Wednesday 31 July 2013 08.56 EDT
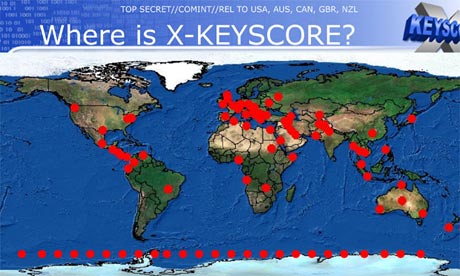 One presentation claims the XKeyscore program covers 'nearly everything a typical user does on the internet'
One presentation claims the XKeyscore program covers 'nearly everything a typical user does on the internet'
A top secret National Security Agency program allows analysts to search with no prior authorization through vast databases containing emails, online chats and the browsing histories of millions of individuals, according to documents provided by whistleblower Edward Snowden.
The NSA boasts in training materials that the program, called XKeyscore, is its "widest-reaching" system for developing intelligence from the internet.
The latest revelations will add to the intense public and congressional debate around the extent of NSA surveillance programs. They come as senior intelligence officials testify to the Senate judiciary committee on Wednesday, releasing classified documents in response to the Guardian's earlier stories on bulk collection of phone records and Fisa surveillance court oversight.
The files shed light on one of Snowden's most controversial statements, made in his first video interview published by the Guardian on June 10.
"I, sitting at my desk," said Snowden, could "wiretap anyone, from you or your accountant, to a federal judge or even the president, if I had a personal email".
US officials vehemently denied this specific claim. Mike Rogers, the Republican chairman of the House intelligence committee, said of Snowden's assertion: "He's lying. It's impossible for him to do what he was saying he could do."
But training materials for XKeyscore detail how analysts can use it and other systems to mine enormous agency databases by filling in a simple on-screen form giving only a broad justification for the search. The request is not reviewed by a court or any NSA personnel before it is processed.
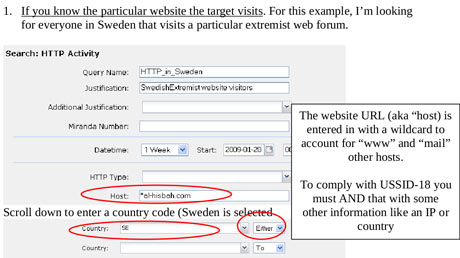
XKeyscore, the documents boast, is the NSA's "widest reaching" system developing intelligence from computer networks – what the agency calls Digital Network Intelligence (DNI). One presentation claims the program covers "nearly everything a typical user does on the internet", including the content of emails, websites visited and searches, as well as their metadata.
Analysts can also use XKeyscore and other NSA systems to obtain ongoing "real-time" interception of an individual's internet activity.
Under US law, the NSA is required to obtain an individualized Fisa warrant only if the target of their surveillance is a 'US person', though no such warrant is required for intercepting the communications of Americans with foreign targets. But XKeyscore provides the technological capability, if not the legal authority, to target even US persons for extensive electronic surveillance without a warrant provided that some identifying information, such as their email or IP address, is known to the analyst.
One training slide illustrates the digital activity constantly being collected by XKeyscore and the analyst's ability to query the databases at any time.
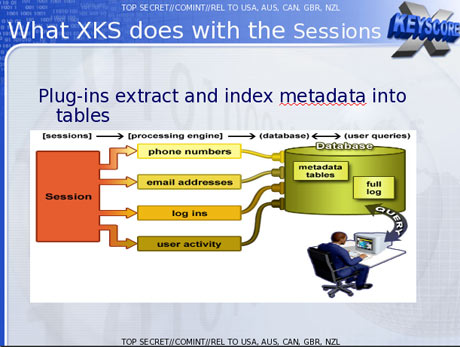 The purpose of XKeyscore is to allow analysts to search the metadata as well as the content of emails and other internet activity, such as browser history, even when there is no known email account (a "selector" in NSA parlance) associated with the individual being targeted.
The purpose of XKeyscore is to allow analysts to search the metadata as well as the content of emails and other internet activity, such as browser history, even when there is no known email account (a "selector" in NSA parlance) associated with the individual being targeted.
Analysts can also search by name, telephone number, IP address, keywords, the language in which the internet activity was conducted or the type of browser used.
One document notes that this is because "strong selection [search by email address] itself gives us only a very limited capability" because "a large amount of time spent on the web is performing actions that are anonymous."
The NSA documents assert that by 2008, 300 terrorists had been captured using intelligence from XKeyscore.
Analysts are warned that searching the full database for content will yield too many results to sift through. Instead they are advised to use the metadata also stored in the databases to narrow down what to review.
A slide entitled "plug-ins" in a December 2012 document describes the various fields of information that can be searched. It includes "every email address seen in a session by both username and domain", "every phone number seen in a session (eg address book entries or signature block)" and user activity – "the webmail and chat activity to include username, buddylist, machine specific cookies etc".
Email monitoring
In a second Guardian interview in June, Snowden elaborated on his statement about being able to read any individual's email if he had their email address. He said the claim was based in part on the email search capabilities of XKeyscore, which Snowden says he was authorized to use while working as a Booz Allen contractor for the NSA.
One top-secret document describes how the program "searches within bodies of emails, webpages and documents", including the "To, From, CC, BCC lines" and the 'Contact Us' pages on websites".
To search for emails, an analyst using XKS enters the individual's email address into a simple online search form, along with the "justification" for the search and the time period for which the emails are sought.
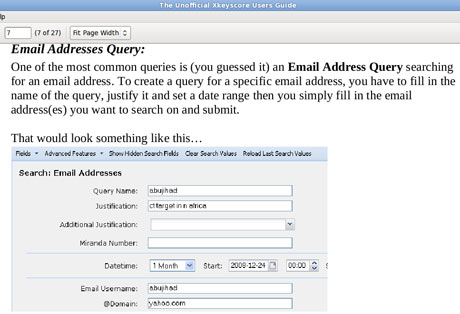
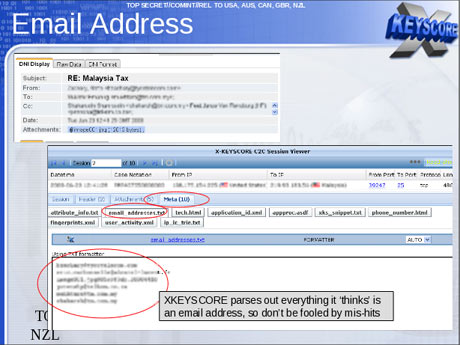 The analyst then selects which of those returned emails they want to read by opening them in NSA reading software.
The analyst then selects which of those returned emails they want to read by opening them in NSA reading software.
The system is similar to the way in which NSA analysts generally can intercept the communications of anyone they select, including, as one NSA document put it, "communications that transit the United States and communications that terminate in the United States".
One document, a top secret 2010 guide describing the training received by NSA analysts for general surveillance under the Fisa Amendments Act of 2008, explains that analysts can begin surveillance on anyone by clicking a few simple pull-down menus designed to provide both legal and targeting justifications. Once options on the pull-down menus are selected, their target is marked for electronic surveillance and the analyst is able to review the content of their communications:
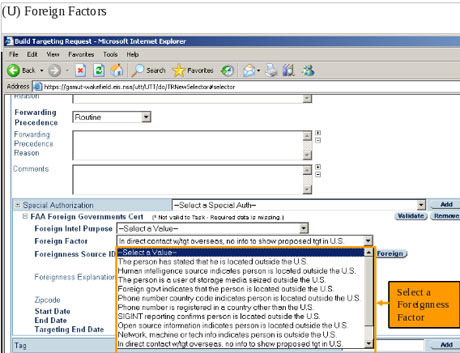 Chats, browsing history and other internet activity
Chats, browsing history and other internet activity
Beyond emails, the XKeyscore system allows analysts to monitor a virtually unlimited array of other internet activities, including those within social media.
An NSA tool called DNI Presenter, used to read the content of stored emails, also enables an analyst using XKeyscore to read the content of Facebook chats or private messages.
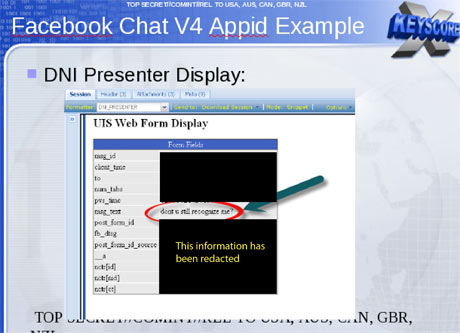 An analyst can monitor such Facebook chats by entering the Facebook user name and a date range into a simple search screen.
An analyst can monitor such Facebook chats by entering the Facebook user name and a date range into a simple search screen.
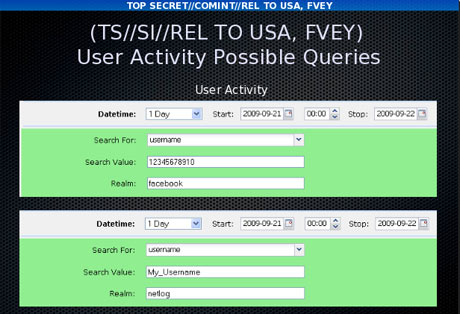 Analysts can search for internet browsing activities using a wide range of information, including search terms entered by the user or the websites viewed.
Analysts can search for internet browsing activities using a wide range of information, including search terms entered by the user or the websites viewed.
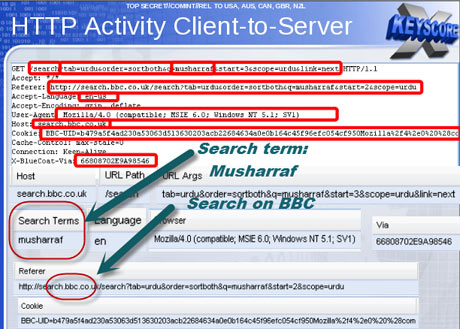 As one slide indicates, the ability to search HTTP activity by keyword permits the analyst access to what the NSA calls "nearly everything a typical user does on the internet".
As one slide indicates, the ability to search HTTP activity by keyword permits the analyst access to what the NSA calls "nearly everything a typical user does on the internet".
 The XKeyscore program also allows an analyst to learn the IP addresses of every person who visits any website the analyst specifies.
The XKeyscore program also allows an analyst to learn the IP addresses of every person who visits any website the analyst specifies.
 The quantity of communications accessible through programs such as XKeyscore is staggeringly large. One NSA report from 2007 estimated that there were 850bn "call events" collected and stored in the NSA databases, and close to 150bn internet records. Each day, the document says, 1-2bn records were added.
The quantity of communications accessible through programs such as XKeyscore is staggeringly large. One NSA report from 2007 estimated that there were 850bn "call events" collected and stored in the NSA databases, and close to 150bn internet records. Each day, the document says, 1-2bn records were added.
William Binney, a former NSA mathematician, said last year that the agency had "assembled on the order of 20tn transactions about US citizens with other US citizens", an estimate, he said, that "only was involving phone calls and emails". A 2010 Washington Post article reported that "every day, collection systems at the [NSA] intercept and store 1.7bn emails, phone calls and other type of communications."
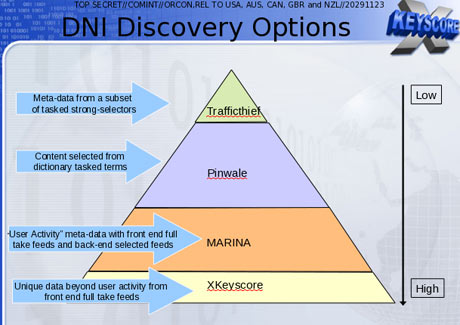
The XKeyscore system is continuously collecting so much internet data that it can be stored only for short periods of time. Content remains on the system for only three to five days, while metadata is stored for 30 days. One document explains: "At some sites, the amount of data we receive per day (20+ terabytes) can only be stored for as little as 24 hours."
To solve this problem, the NSA has created a multi-tiered system that allows analysts to store "interesting" content in other databases, such as one named Pinwale which can store material for up to five years.
It is the databases of XKeyscore, one document shows, that now contain the greatest amount of communications data collected by the NSA.
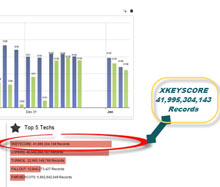
 In 2012, there were at least 41 billion total records collected and stored in XKeyscore for a single 30-day period.
In 2012, there were at least 41 billion total records collected and stored in XKeyscore for a single 30-day period.
 Legal v technical restrictions
Legal v technical restrictions
While the Fisa Amendments Act of 2008 requires an individualized warrant for the targeting of US persons, NSA analysts are permitted to intercept the communications of such individuals without a warrant if they are in contact with one of the NSA's foreign targets.
The ACLU's deputy legal director, Jameel Jaffer, told the Guardian last month that national security officials expressly said that a primary purpose of the new law was to enable them to collect large amounts of Americans' communications without individualized warrants.
"The government doesn't need to 'target' Americans in order to collect huge volumes of their communications," said Jaffer. "The government inevitably sweeps up the communications of many Americans" when targeting foreign nationals for surveillance.
An example is provided by one XKeyscore document showing an NSA target in Tehran communicating with people in Frankfurt, Amsterdam and New York.
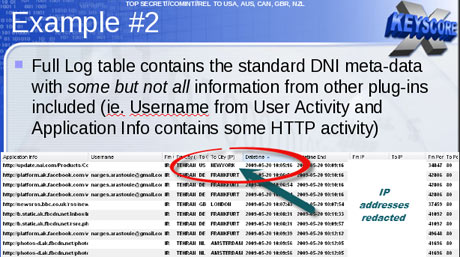 In recent years, the NSA has attempted to segregate exclusively domestic US communications in separate databases. But even NSA documents acknowledge that such efforts are imperfect, as even purely domestic communications can travel on foreign systems, and NSA tools are sometimes unable to identify the national origins of communications.
In recent years, the NSA has attempted to segregate exclusively domestic US communications in separate databases. But even NSA documents acknowledge that such efforts are imperfect, as even purely domestic communications can travel on foreign systems, and NSA tools are sometimes unable to identify the national origins of communications.
Moreover, all communications between Americans and someone on foreign soil are included in the same databases as foreign-to-foreign communications, making them readily searchable without warrants.
Some searches conducted by NSA analysts are periodically reviewed by their supervisors within the NSA. "It's very rare to be questioned on our searches," Snowden told the Guardian in June, "and even when we are, it's usually along the lines of: 'let's bulk up the justification'."
In a letter this week to senator Ron Wyden, director of national intelligence James Clapper acknowledged that NSA analysts have exceeded even legal limits as interpreted by the NSA in domestic surveillance.
Acknowledging what he called "a number of compliance problems", Clapper attributed them to "human error" or "highly sophisticated technology issues" rather than "bad faith".
However, Wyden said on the Senate floor on Tuesday: "These violations are more serious than those stated by the intelligence community, and are troubling."
In a statement to the Guardian, the NSA said: "NSA's activities are focused and specifically deployed against – and only against – legitimate foreign intelligence targets in response to requirements that our leaders need for information necessary to protect our nation and its interests.
"XKeyscore is used as a part of NSA's lawful foreign signals intelligence collection system.
"Allegations of widespread, unchecked analyst access to NSA collection data are simply not true. Access to XKeyscore, as well as all of NSA's analytic tools, is limited to only those personnel who require access for their assigned tasks … In addition, there are multiple technical, manual and supervisory checks and balances within the system to prevent deliberate misuse from occurring."
"Every search by an NSA analyst is fully auditable, to ensure that they are proper and within the law.
"These types of programs allow us to collect the information that enables us to perform our missions successfully – to defend the nation and to protect US and allied troops abroad."
Article history
World news
- The NSA files ·
- Surveillance ·
- NSA ·
- United States ·
- Privacy ·
- US politics ·
- US Congress
Technology
Series
More from Glenn Greenwald on security and liberty on
World news
- The NSA files ·
- Surveillance ·
- NSA ·
- United States ·
- Privacy ·
- US politics ·
- US Congress
Technology
More news
-
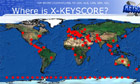
XKeyscore presentation from 2008 – read in full
Training materials for the NSA's XKeyscore program detail how analysts can use it and other systems to mine enormous agency databases and develop intelligence from the internet -
US senators rail against intelligence disclosures over NSA practices
“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
-
07-31-2013, 05:51 PM #304
US senators rail against intelligence disclosures over NSA practices
Officials say bulk phone records collection was not 'the most important tool' – contradicting previous statements to Congress
• Follow live updates from the Senate committee hearing
- Spencer Ackerman and Paul Lewis in Washington
- theguardian.com, Wednesday 31 July 2013 12.50 EDT
 NSA deputy director John C Inglis testifies during a hearing before the Senate judiciary committee. Photograph: Alex Wong/Getty Images
NSA deputy director John C Inglis testifies during a hearing before the Senate judiciary committee. Photograph: Alex Wong/Getty Images
The bipartisan leaders of a powerful Senate committee questioned the truthfulness of the US intelligence community in a heated Wednesday morning hearing as officials conceded that their controversial bulk phone records collection of millions of Americans was not "the most important tool" – contradicting statements they previously gave to Congress.
Two senators said they now planned to introduce new legislation before the August recess that would significantly transform the transparency and oversight of the bulk surveillance program. The chairman of the committee has already advocated for ending the bulk phone records collection and plans his own legislative push to shut it down.
Just before the hearing began, the US director of national intelligence declassified and released documents shedding more light on how the bulk surveillance occurs. Senator Al Franken, a Minnesota Democrat, denounced the move as "ad hoc transparency."
Patrick Leahy, a Vermont Democrat and chairman of the Senate judiciary committee, said: "We need straightforward answers, and I'm concerned we're not getting them."
Leahy, joined by ranking Republican Chuck Grassley of Iowa, criticised director of national intelligence James Clapper for making untruthful statements to Congress in March about the bulk phone records collection on Americans, and NSA director Keith Alexander for overstating the usefulness of that collection for stopping terrorist attacks.
Grassley called Clapper's recent apology to senator Ron Wyden and the intelligence community "especially disturbing".
"Nothing can excuse this kind of behavior from a senior administration official," Grassley said. "Especially on a matter of such importance."
Clapper was not at the hearing. Instead, NSA deputy director John Inglis, deputy attorney general James Cole and FBI deputy director Sean Joyce strongly defended the bulk phone records collection. "We must have the dots to connect the dots," Joyce said.
Dianne Feinstein, a judiciary committee member who also chairs the Senate intelligence committee, defended the officials. "We would place the nation in jeopardy if we were to end these two programs," she said.
But Leahy pressed the intelligence and law enforcement officials to detail how many terrorist plots the bulk phone records collection on millions of Americans, first disclosed by the Guardian thanks to whistleblower Edward Snowden, had disrupted. "That's a very difficult question to answer," Inglis testified. "That's not how these programs work."
Yet two of the three documents declassified by Clapper on Wednesday claim the phone records database was critical to stopping terrorist attacks. The documents, four-page summaries of the bulk collection programmes provided to Congress in 2009 and 2011 before key votes on surveillance laws, state that the bulk phone records collection and a separate internet communications collection effort "significantly strengthen the intelligence community's early warning system for the detection of terrorists and discovery of plots against the homeland."
The NSA has previously claimed that 54 terrorist plots had been disrupted "over the lifetime" of the bulk phone records collection and the separate program collecting the internet habits and communications of people believed to be non-Americans. On Wednesday, Inglis said that at most one plot might have been disrupted by the bulk phone records collection alone. "There is an example that comes close to a 'but for' example," Inglis said.
"Each tool plays a different role," Joyce said. Discussing the phone records bulk collection, he said: "I'm not saying it's the most important tool."
Senators Wyden and Mark Udall, members of the intelligence committee, have repeatedly said that there is no evidence that the controversial bulk phone records collection has disrupted any terrorist plots. They criticized intelligence officials for conflating to Congress the value of the phone records database and the internet communications surveillance. Last week, the House of Representatives came within seven votes of defunding the program.
"We are open to re-evaluating this program in ways that creates greater public confidence and trust," Robert Litt, the top lawyer for the US intelligence community, testified.
Wyden and Udall argued Tuesday night on the Senate floor for ending the bulk phone records collection. They accused intelligence officials, including Clapper, of deceiving Congress about the extent of abuses of NSA's databases, which Clapper described as accidental.
Before the Wednesday hearing, the first in the Senate on the bulk NSA surveillance, Clapper declassified new documents about the programs. One of them was a heavily redacted April order from the Fisa court on the rules for NSA to handle the bulk phone records it collects, complementing the one published by the Guardian in June.
The order obliges the NSA to ensure that it has a "reasonable articulable suspicion" before making any query of the phone records database. Judges are not required to certify that the NSA has met that standard before each search.
The order also authorizes the NSA's "technical personnel" to query the database using terms that fall outside the definition of reasonable articulable suspicion, "but the results of any such queries will not be used for intelligence analysis purposes".
A footnote in the document specifies that "technical personnel responsible for NSA's corporate infrastructure and the transmission of BR metadata" may handle the phone records data without the "special training" in court-ordered restrictions undergone by NSA intelligence analysts. They do not require "reasonable articulable suspicion" to do so.
The order also authorises searches by automated means.
Two senators said they would introduce legislation as early as Thursday that would change the transparency rules and the structure of Court oversight around the bulk surveillance.
Franken said he would introduce a bill forcing the NSA to disclose how many Americans have had their data collected, and how many Americans' data the NSA has analysed once placed in its databases. Last year, the NSA denied it had any way of estimating that number, and told Wyden that providing it would violate Americans' privacy.
Documents published by the Guardian that Snowden provided, however, revealed an NSA analytic tool called Boundless Informant that displays the country of origin of collected communications.
Senator Richard Blumenthal, a Connecticut Democrat, said he would also submit a second bill on Thursday to significantly reform the Fisa court process, including the introduction of security-cleared special advocates, to challenge the position of the administration.
He said the Fisa court needed to become more adversarial. "I think the current design of the Fisa courts is stacked against the protection of our civil liberties and can be improved and enhanced, without sacrificing either speed or security."“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
-
07-31-2013, 08:45 PM #305AprilGuest
Edward Snowden's father says FBI asked him to fly to Moscow
Lon Snowden says his son will be 'treated horribly' if he returns to US and in his place he would stay in Russia
- James Meikle and agencies
- The Guardian, Wednesday 31 July 2013 07.21 EDT
 Edward Snowden's father, Lon Snowden, who said he was not going to be an 'emotional tool' for the FBI. Photograph: Peter Kramer/AP
Edward Snowden's father, Lon Snowden, who said he was not going to be an 'emotional tool' for the FBI. Photograph: Peter Kramer/AP
The father of the whistleblower Edward Snowden has said the FBI tried to persuade him to fly to Moscow so that he could encourage his son to return to the United States.
"I said: 'I want to be able to speak with my son … Can you set up communications?' and it was 'Well, we are not sure,'" Lon Snowden told the Washington Post. "I said: 'Wait a minute, folks, I'm not going to sit on the tarmac to be an emotional tool for you.'"
Snowden's father, who is retired from the US Coast Guard, also said he preferred Edward to remain in Russia, where he is stuck in the transit zone of Moscow's Sheremetyevo airport while Russia considers his request for temporary asylum.
"If he comes back to the United States, he is going to be treated horribly. He is going to be thrown into a hole. He is not going to be allowed to speak." The 52-year-old said he had been as "surprised as the rest of America" when his son, who worked for a contractor, was revealed as the source of the leaks about surveillance by the National Security Agency to the Guardian. "As a father it pains me what he did," Snowden said. "I wish my son could simply have sat in Hawaii and taken the big paycheck, lived with his beautiful girlfriend and enjoyed paradise. But as an American citizen, I am absolutely thankful for what he did."
Lon Snowden said that two days after Edward was revealed as the whistleblower, FBI agents had arrived at his home outside Allentown, Pennsylvania. He had spoken to them for four hours and shared emails he had exchanged with his son. Later the FBI asked him to fly to Moscow. FBI officials declined to comment on why negotiations about the idea foundered, the Post said.
As to why Lon Snowden had not flown to Moscow himself, he said: "Sure, I could get on a flight tomorrow to Russia. I'm not sure if I could get access to Edward." He said he had communicated with his son through intermediaries.
In an interview with the state-owned Rossiya 24 TV, the older Snowden, his words translated into Russian, said he had yet to decline the idea of travelling to Moscow at the FBI's request, but would first like to know what the agency wanted him to do. "If [Edward] wants to spend the rest of his life in Russia, I would agree. I am not against it. If I were in his place, I would stay in Russia, and I hope Russia will accept him."
He did not think his son would get a fair trial in the US. "I hope that he will return home and appear in court … But I don't expect that … a court would be fair. We cannot guarantee a fair court." He also thanked Vladimir Putin and his government for the "courage" they had shown in keeping his son safe. Lon Snowden also addressed his son, saying: "Your family is well and we love you. We hope you are healthy, we hope you are well, I hope to see you soon, but most of all I want you to be safe." He added: "I want you to find safe haven. I know the last 55 days have been very difficult."
Anatoly Kuchera, a Russian lawyer helping Edward Snowden, told the programme he thought the asylum request would be granted "in the coming days" and the US had not sent an official request for extradition. "Just saying 'hand him over' is absolutely dishonourable and incorrect," he said.
http://www.theguardian.com/world/201...her-fbi-moscow
- James Meikle and agencies
-
08-01-2013, 11:15 PM #306AprilGuest

Snowden granted one-year asylum in Russia
The Russian Federation granted former National Security Agency contractor Edward Snowden asylum for one year on Thursday, leaving more questions than answers about the future of a man who stoked the fires of the privacy debate in the U.S. and across the globe.
Snowden’s newly acquired refugee status — which expires July 31, 2014 — allowed him “to slip quietly out of Moscow’s Sheremetyevo airport after more than five weeks in limbo,” Reuters reports, adding to strained tensions between the Obama administration and the Kremlin.
Snowden, no longer needing to seek refuge in an airport, can now roam and work freely in Russia. He will be staying in a secret location.
According to WikiLeaks, he thanked the Russian government on Thursday, stating, “Over the past eight weeks we have seen the Obama administration show no respect for international or domestic law but in the end the law is winning.”
After coming to the realization that his son would not receive a fair trail in the U.S. under the Obama administration, Snowden’s father — Lon Snowden — decided that it was best for his son to stay in Russia “until an administration that respects the Constitution comes into office.”
Since Snowden first unveiled himself as the source behind the Guardian and the Washington Post’s recent stories about the West’s massive global electronic surveillance programs, his father has publicly advocated for his safe return and a fair trial.
Snowden is rumored to have reached out to a former group of former KGB officers during his stay at the airport, the Washington Free Beacon reported on July 24.
The group, Veterans of the Siloviki, had hoped to provide Snowden, a fellow colleague of the intelligence profession, with basic humanitarian assistance during his time in limbo.
His newly acquired refugee status was granted 29 days after he received a marriage proposal from the super-hot suspected Russian spy Anna Chapman on Twitter.
http://dailycaller.com/2013/08/01/sn...lum-in-russia/
-
08-02-2013, 07:31 PM #307
Pelosi faces liberal heat for NSA snooping support
http://www.washingtontimes.com/blog/...oping-support/
← return to Inside Politics
Comments (112)
Size: + / -
Print
By Stephen Dinan - The Washington Times
August 2, 2013, 09:55AM
 Enlarge Photo
Enlarge Photo
**FILE** House Minority Leader Nancy Pelosi addresses an audience in Boston during ... more >
Recent Entries
- Alaskans oppose Palin White House run: Poll
- Pelosi faces liberal heat for NSA snooping support
- OFA launches 'Truth Team' to tout Obamacare
- Reid unveils new Senate decorum: 'Have senators sit down and shut up'
- Conservatives say time is right to defund Obamacare
Liberal activists are planning a rally this weekend in House Minority Leader Nancy Pelosi’s home district to protest her vote last week to protect the National Security Agency’s phone records snooping program, saying the California Democrat has betrayed her principles.
“Pelosi has let down the large number of her constituents — whether they call themselves, liberal, progressive, conservative, libertarian or whatever — who are appalled by revelations of dragnet NSA surveillance and want it stopped,” said Norman Solomon, co-founder of RootsAction and one of the scheduled speakers.
The activists say they plan to rally and then march past Mrs. Pelosi’s district office. They’ll also hear speeches from famous whistleblowers such as Daniel Ellsberg, the government contractor who released the Pentagon Papers exposing the full scale of U.S. involvement in Vietnam during the war.
The rally is part of a nationwide push known as “1984 Day” — timed for Aug. 4, or 8/4 — designed to call attention to the NSA’s surveillance program, under which the government collects and stores for five years the records of all phone calls made in the U.S.
The government said it doesn’t look at the data unless it suspects someone of terrorism, but those assurances have not calmed critics in Congress.
Last week, opponents in the House tried to cancel the program by proposing an amendment to defund it. Mrs. Pelosi voted against that amendment, helping doom it to defeat on a 217-205 vote.
The activists organizing Sunday’s march say Mrs. Pelosi was responsible for the defeat because as her party’s leader, she rallied Democrats to oppose the amendment. Foreign Policy magazine reported that she had a bigger effect in swaying Democrats to back the program than even NSA chief Gen. Keith Alexander.
In the end, 83 Democrats joined 134 Republicans in protecting the program.
Democratic leaders, however, were split. Mrs. Pelosi and House Minority Whip Steny H. Hoyer voted to preserve the program, while Assistant Leader James E. Clyburn and Caucus Chairman Xavier Becerra voted to scrap it.
All of the chamber’s Republican leaders voted to protect the program.
In the wake of the vote, Mrs. Pelosi organized a letter signed by 153 fellow House Democrats demanding that President Obama try to work with Congress on changes to the program.
“Although some of us voted for and others against the amendment, we all agree that there are lingering questions and concerns” about the data-collection program, the lawmakers said in their letter.“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
-
08-03-2013, 11:43 AM #308Banned

- Join Date
- Jun 2013
- Posts
- 8,546
Good information!!
-
08-04-2013, 11:19 AM #309AprilGuest
Members of Congress denied access to basic information about NSA
Documents provided by two House members demonstrate how they are blocked from exercising any oversight over domestic surveillance
• Morgan Griffith's requests for NSA information
• Alan Grayson's requests for NSA information
Beta
-

- Glenn Greenwald
- theguardian.com, Sunday 4 August 2013 08.26 EDT
- Jump to comments (240)
- Glenn Greenwald
 Members of Congress are increasingly frustrated at their inability to obtain even basic information about the NSA and FISA court. Photograph: Alex Wong/Getty Images
Members of Congress are increasingly frustrated at their inability to obtain even basic information about the NSA and FISA court. Photograph: Alex Wong/Getty Images
Members of Congress have been repeatedly thwarted when attempting to learn basic information about the National Security Agency (NSA) and the secret FISA court which authorizes its activities, documents provided by two House members demonstrate.
From the beginning of the NSA controversy, the agency's defenders have insisted that Congress is aware of the disclosed programs and exercises robust supervision over them. "These programs are subject to congressional oversight and congressional reauthorization and congressional debate," President Obama said the day after the first story on NSA bulk collection of phone records was published in this space. "And if there are members of Congress who feel differently, then they should speak up."
But members of Congress, including those in Obama's party, have flatly denied knowing about them. On MSNBC on Wednesday night, Sen. Richard Blumenthal (D-Ct) was asked by host Chris Hayes: "How much are you learning about what the government that you are charged with overseeing and holding accountable is doing from the newspaper and how much of this do you know?" The Senator's reply:
The revelations about the magnitude, the scope and scale of these surveillances, the metadata and the invasive actions surveillance of social media Web sites were indeed revelations to me."But it is not merely that members of Congress are unaware of the very existence of these programs, let alone their capabilities. Beyond that, members who seek out basic information - including about NSA programs they are required to vote on and FISA court (FISC) rulings on the legality of those programs - find that they are unable to obtain it.
Two House members, GOP Rep. Morgan Griffith of Virginia and Democratic Rep. Alan Grayson of Florida, have provided the Guardian with numerous letters and emails documenting their persistent, and unsuccessful, efforts to learn about NSA programs and relevant FISA court rulings.
"If I can't get basic information about these programs, then I'm not able to do my job", Rep. Griffith told me. A practicing lawyer before being elected to Congress, he said that his job includes "making decisions about whether these programs should be funded, but also an oath to safeguard the Constitution and the Bill of Rights, which includes the Fourth Amendment."
Rep. Griffith requested information about the NSA from the House Intelligence Committee six weeks ago, on June 25. He asked for "access to the classified FISA court order(s) referenced on Meet the Press this past weekend": a reference to my raising with host David Gregory the still-secret 2011 86-page ruling from the FISA court that found substantial parts of NSA domestic spying to be in violation of the Fourth Amendment as well as governing surveillance statutes.
In that same June 25 letter, Rep. Griffith also requested the semi-annual FISC "reviews and critiques" of the NSA. He stated the rationale for his request: "I took an oath to uphold the United States Constitution, and I intend to do so."
Almost three weeks later, on July 12, Rep. Griffith requested additional information from the Intelligence Committee based on press accounts he had read about Yahoo's unsuccessful efforts in court to resist joining the NSA's PRISM program. He specifically wanted to review the arguments made by Yahoo and the DOJ, as well as the FISC's ruling requiring Yahoo to participate in PRISM.
On July 22, he wrote another letter to the Committee seeking information. This time, it was prompted by press reports that that the FISA court had renewed its order compelling Verizon to turn over all phone records to the NSA. Rep. Griffith requested access to that court ruling.
The Congressman received no response to any of his requests. With a House vote looming on whether to defund the NSA's bulk collection program - it was scheduled for July 25 - he felt he needed the information more urgently than ever. He recounted his thinking to me: "How can I responsibly vote on a program I know very little about?"
On July 23, he wrote another letter to the Committee, noting that it had been four weeks since his original request, and several weeks since his subsequent ones. To date, six weeks since he first asked, he still has received no response to any of his requests (the letters sent by Rep. Griffith can be seen here).
"I know many of my constituents will ask about this when I go home," he said, referring to the August recess when many members of Congress meet with those they represent. "Now that I won't get anything until at least September, what am I supposed to tell them? How can I talk about NSA actions I can't learn anything about except from press accounts?"
Congressman Grayson has had very similar experiences, except that he sometimes did receive responses to his requests: negative ones.
On June 19, Grayson wrote to the House Intelligence Committee requesting several documents relating to media accounts about the NSA. Included among them were FISA court opinions directing the collection of telephone records for Americans, as well as documents relating to the PRISM program.
But just over four weeks later, the Chairman of the Committee, GOP Rep. Mike Rogers, wrote to Grayson informing him that his requests had been denied by a Committee "voice vote".
In a follow-up email exchange, a staff member for Grayson wrote to the Chairman, advising him that Congressman Grayson had "discussed the committee's decision with Ranking Member [Dutch] Ruppersberger on the floor last night, and he told the Congressman that he was unaware of any committee action on this matter." Grayson wanted to know how a voice vote denying him access to these documents could have taken place without the knowledge of the ranking member on the Committee, and asked: "can you please share with us the recorded vote, Member-by-Member?" The reply from this Committee was as follows:
To date, neither Griffith nor Grayson has received any of the documents they requested. Correspondence between Grayson and the Committee - with names of staff members and email addresses redacted - can be read here.
Thanks for your inquiry. The full Committee attends Business Meetings. At our July 18, 2013 Business Meeting, there were seven Democrat Members and nine Republican Members in attendance. The transcript is classified."
Denial of access for members of Congress to basic information about the NSA and the FISC appears to be common. Justin Amash, the GOP representative who, along with Democratic Rep. John Conyers, co-sponsored the amendment to ban the NSA's bulk collection of Americans' phone records, told CNN on July 31: "I, as a member of Congress, can't get access to the court opinions. I have to beg for access, and I'm denied it if I - if I make that request."
It is the Intelligence Committees of both the House and Senate that exercise primary oversight over the NSA. But as I noted last week, both Committees are, with the exception of a handful of members, notoriously beholden to the NSA and the intelligence community generally.
Its members typically receive much larger contributions from the defense and surveillance industries than non-Committee members. And the two Committee Chairs - Democrat Dianne Feinstein in the Senate and Republican Mike Rogers in the House - are two of the most steadfast NSA loyalists in Congress. The senior Democrat on the House Committee is ardent NSA defender Dutch Ruppersberger, whose district not only includes NSA headquarters in Fort Meade, but who is also himself the second-largest recipient of defense/intelligence industry cash.
Moreover, even when members of the Intelligence Committee learn of what they believe to be serious abuses by the NSA, they are barred by law from informing the public. Two Democratic Committee members in the Senate, Ron Wyden and Mark Udall, spent years warning Americans that they would be "stunned to learn" of the radical interpretations of secret law the Obama administration had adopted in the secret FISA court to vest themselves with extremist surveillance powers.
Yet the two Senators, prohibited by law from talking about it, concealed what they had discovered. It took Edward Snowden's whistleblowing for Americans to learn what those two Intelligence Committee members were so dramatically warning them about.
Finally, all members of Congress - not just those on the Intelligence Committees - are responsible for making choices about the NSA and for protecting the privacy rights and other Constitutional guarantees of Americans. "I did not take an oath to defer to the Intelligence Committee," Rep. Griffith told me. "My oath is to make informed decisions, and I can't do my job when I can't get even the most basic information about these programs."
In early July, Grayson had staffers distribute to House members several slides published by the Guardian about NSA programs as part of Grayson's efforts to trigger debate in Congress. But, according to one staff member, Grayson's office was quickly told by the House Intelligence Committee that those slides were still classified, despite having been published and discussed in the media, and directed Grayson to cease distribution or discussion of those materials in the House, warning that he could face sanctions if he continued.
It has been widely noted that the supremely rubber-stamping FISA court constitutes NSA "oversight" in name only, and that the Intelligence Committees are captured by the agency and constrained to act even if they were inclined to. Whatever else is true, members of Congress in general clearly know next to nothing about the NSA and the FISA court beyond what they read in the media, and those who try to rectify that are being actively blocked from finding out.
http://www.theguardian.com/commentis...-denied-access
-
-
08-05-2013, 08:14 PM #310
August 5, 2013 | By Micah Lee and David Grant
Google: Keep Android Users' Secure Network Passwords Secure
https://www.eff.org/deeplinks/2013/0...sswords-secure
If you have a recent Android phone or tablet, chances are you take advantage of a convenient feature to backup your application settings and wireless network passwords. This feature is enabled by default in Android 2.2 and later, and it can make switching to a new device or replacing a lost phone a quicker process. If you haven't examined all the settings for your phone, you might not know if this setting is enabled.
You might not even know who has access to your data.

When a Google user sets up a new Android device with Google Play and signs into her Google account, Android Backup Service automatically downloads any backed up settings and wireless network passwords from Google's servers. All that is required of the user to begin this process is her Google credentials.
This indicates that the data is stored either in plaintext, or encrypted using Google account credentials only. In the latter case, it would need to be decrypted before transit to the user's device. However, a statement from Google to Ars Technica indicates that the former might be the case:"Our optional 'Backup my data' feature makes it easier to switch to a new Android device by using your Google Account and password to restore some of your previous settings. This helps you avoid the hassle of setting up a new device from scratch. At any point, you can disable this feature, which will cause data to be erased. This data is encrypted in transit, accessible only when the user has an authenticated connection to Google and stored at Google data centers, which have strong protections against digital and physical attacks."This statement makes clear that the data is encrypted in transit, which is good. But it doesn't say that the data is encrypted at rest. If it's not, authorized Google employees could access it or make it available to government data requests. We hope that Google is storing this data in an encrypted form such that only the user can unlock it.
How sensitive is this data? Settings data is generally limited to the options you select when configuring your device. It may also include a list of software you have downloaded from the Google Play Store.
Your wireless network passwords might be considered very sensitive. While you personally might not be too worried about sharing the encryption key for your home network, your employer might feel differently. In either case, since the network administrator has made the decision to secure the network, any developer designing software to store the network password should respect that decision and assume that the password wasn't meant to be left lying around in plain sight or plaintext.
Fixing the flaw is more complicated than it might seem. Android is open source operating system developed by Google. Android Backup Service is a proprietary service offered by Google, which runs on Android. Anyone can write new code for Android, but only Google can change the Android Backup Service.
Google already has a great model for this kind of service in Chrome. Chrome's sync service allows a user to store all her settings on Google's servers, encrypted. By default, the data is encrypted with her Google credentials, but Chrome offers the additional option to encrypt this data with the user's own sync passphrase. This model would work very well for Android Backup Service.

Additionally, the open source Android OS itself could offer client side encryption as part of the backup code that Android Backup Service is built on. That way, third-party providers could more easily safeguard your data.
Cloud storage of personal data has become a ubiquitous part of the computing landscape, and of our daily lives. With frequent revelations of government, corporate, and entirely unauthorized abuse of that personal data, it's important to examine what we give to cloud providers, when, and how. The standard we'd like to see providers move toward is host-proof hosting, especially when backing up sensitive data. It might be reasonable to trust these companies at times in order to take advantage of the convenience their services offer, but trusting a service that mishandles one's data by failing to properly secure it is clearly a mistake.
Google says, "You should only give your WiFi password to people you trust." If Google has mapped our wireless networks and stored their passwords, they need to act fast to restore that trust.
To turn off settings and WiFI password backups, and delete Google's stored copies, go to Backup & Reset Settings and uncheck "Back up my data." “In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson


 27Likes
27Likes LinkBack URL
LinkBack URL About LinkBacks
About LinkBacks




 Reply With Quote
Reply With Quote


Giant Laken Riley Billboard Truck Circles Biden’s Speaking Venue...
04-23-2024, 09:52 PM in Americans Killed By illegal immigrants / illegals