Results 561 to 570 of 582
Thread Information
Users Browsing this Thread
There are currently 1 users browsing this thread. (0 members and 1 guests)
-
04-22-2014, 04:42 AM #561Senior Member


- Join Date
- May 2007
- Location
- South West Florida (Behind friendly lines but still in Occupied Territory)
- Posts
- 117,696
Obama Administration Issues New Order To Keep Americans In The Dark On Government Spying
April 22, 2014 by Sam Rolley
 THINKSTOCK
THINKSTOCK
Government transparency advocates have denounced a new Barack Obama Administration directive that forbids U.S. intelligence workers from talking to members of the press without permission from superiors.
“IC employees … must obtain authorization for contacts with the media” if sensitive topics are on the table and “must also report … unplanned or unintentional contact with the media on covered matters,” the directive says.
The directive stems from suggestions made by National Intelligence Director James Clapper last month in an effort “to mitigate risks of unauthorized disclosures of intelligence-related matters” like the Edward Snowden leaks that sparked public outrage.
The rule does not distinguish between classified and unclassified government matters but encourages “appropriate” interaction with media.
According to the Project on Government Secrecy’s Steven Aftergood, this puts U.S. intelligence workers in danger of being penalized under an overly broad directive.
He wrote in a recent blog post:The new Directive creates an anomalous situation in which routine interactions that are permissible between an intelligence employee and an ordinary member of the public are now to be prohibited if that member of the public qualifies as “media.”The consequences are hefty for U.S. intelligence workers who run afoul of the directive, ranging from revocation of security clearance and job termination to jail time.
So under most circumstances, an intelligence community employee is at liberty to discuss unclassified “intelligence-related information” with his or her next-door neighbor. But if the neighbor happened to be a member of the media, then the contact would be prohibited altogether without prior authorization.
Meanwhile, the Directive defines membership in “the media” expansively. It is not necessary to be a credentialed reporter for an established news organization. It is sufficient to be “any person… engaged in the collection, production, or dissemination to the public of information in any form related to topics of national security….”
According to Aftergood, the directive is a boldfaced government effort to ensure that the only news Americans get about the Nation’s surveillance and intelligence efforts has been pre-approved by top officials.
“[T]here is no particular reason to think that routine interactions between intelligence agency employees and reporters — especially on unclassified matters — pose any kind of threat to national security, or that limiting them will offer any benefit,” he wrote. “However, the new policy is likely to be effective in reducing the quality, independence and critical content of intelligence-related information that is available to the press and the public.”
The directive is just the latest in a series of Obama Administration efforts to clamp down on the amount of information Americans can access about the government’s actions.
In 2011, on the heels of then Pfc. Bradley Manning’s military intelligence leaks to Wikileaks, the President created the Federal Insider Threat Program.
McClatchy described the program thusly last summer:President Barack Obama’s unprecedented initiative, known as the Insider Threat Program, is sweeping in its reach. It has received scant public attention even though it extends beyond the U.S. national security bureaucracies to most federal departments and agencies nationwide, including the Peace Corps, the Social Security Administration and the Education and Agriculture departments. It emphasizes leaks of classified material, but catchall definitions of “insider threat” give agencies latitude to pursue and penalize a range of other conduct.Though the latest directive expands Insider Threat, intelligence officials claim that Americans needn’t worry that the efforts will allow the Nation’s spy community to operate with zero oversight or accountability. The new rule declares that the intelligence community “has multiple avenues for its employees to report activities perceived to be unlawful.”
http://personalliberty.com/obama-adm...rnment-spying/Join our efforts to Secure America's Borders and End Illegal Immigration by Joining ALIPAC's E-Mail Alerts network (CLICK HERE)
-
04-22-2014, 04:43 AM #562Senior Member


- Join Date
- May 2007
- Location
- South West Florida (Behind friendly lines but still in Occupied Territory)
- Posts
- 117,696
Even Liberals Booed Pelosi Off Stage As She Defended Obama
Posted on 22 April, 2014 by clyde
House Minority Leader Nancy Pelosi (D-CA) was booed off stage last week—by liberals.
Pelosi defended President Obama’s position on the NSA’s surveillance programs, and suggested that leaker Edward Snowden broke the law by whistleblowing. The congresswoman’s defense of spying was not well received.
“People on the far right are saying ‘Oh, this is the fourth term of President Bush,’” Pelosi said. “Absolutely, positively not so.”
Pelosi then advocated for a greater cooperation between security and privacy agencies.
But the audience did not care for her rhetoric. Several audience members were removed from the room after objecting to Pelosi’s speech.
“It’s not balance. It’s not constitutional! No secret laws!” yelled Marc Perkel. He was immediately carried out by security personnel.
The audience then came to the defense of Perkel. “That’s what a police state looks like right there,” they yelled.
But the tone became even more heated as Pelosi began to defend the Obama administration’s handling of the Edward Snowden scandal.
SEE ALSO: Michelle Obama Acts Foolishly on Stage at White House
“I look forward to working with all of you,” Pelosi said over hecklers. “Now that the public knows more, it gives us an opportunity for some of the things we’ve been advocating for a while.”
Pelosi’s speech met little applause. Will she continue to experience little support this year?
http://americanoverlook.com/even-liberals-booed-pelosi-off-stage-as-she-defended-obama/15468?utm_source=gopthedailydose
http://gopthedailydose.com/2014/04/2...efended-obama/Join our efforts to Secure America's Borders and End Illegal Immigration by Joining ALIPAC's E-Mail Alerts network (CLICK HERE)
-
04-24-2014, 09:00 AM #563AprilGuest
Snowden Asks Putin on Live TV If He Spies on Russians

Edward Snowden, displayed on television screens, asks a question to Russian President Vladimir Putin during a nationally televised question-and-answer session, in Moscow, on April 17, 2014. Image: Pavel Golovkin/Associated Press
 By Lorenzo Franceschi-BicchieraiApr 17, 2014
By Lorenzo Franceschi-BicchieraiApr 17, 2014
In what could be best described as a bizarre PR stunt, Edward Snowden made a surprise appearance on live TV to ask Russian President Vladimir Putin whether he spies on his citizens.
Snowden, who has received asylum in Russia, appeared during Putin's annual call-in show on Russian TV on Thursday, during which Putin answered questions from the public. It's unclear whether Snowden's appearance was staged, but his question gave Putin a chance to poke at his favorite target: the United States.
See also: The World According to Vladimir Putin
"Does Russia store, intercept, or analyze, in any way, the communications of millions of individuals, and do you believe that simply increasing the effectiveness of intelligence or law enforcement investigations can justify a place in societies rather than subjects under surveillance?" Snowden asked Putin (see the full exchange in the video embedded below).
"Mr. Snowden, you are a former agent, a spy. I used to work for the intelligence service, we are going to talk one professional language," Putin said, according to a translation by state-run TV channel Russia Today. "We don't have as much money as they have in the States and we don't have these technical devices that they have in the States. Our special services, thank God, are strictly controlled by society and the law and regulated by the law." Russia clearly has means to "respond" to terrorists and criminals who use technology, Putin added, but doesn't have "uncontrollable efforts like [in America]."
Mr. Snowden, you are a former agent, a spy.
What Putin didn't say, however, is that Russia actually boasts one of the most sophisticated surveillance systems in the world, described by some as "PRISM on steroids." This system, known as SORM, practically gives the Federal Security Service (FSB) direct access to Internet servers and telecommunications providers, allowing the government to eavesdrop on all online and phone communications that go through their networks.
Even though the FSB must get warrants before accessing any data or communications, they don't have to show them to anyone, as Andrei Soldatov, an independent journalist who has written extensively about Russia's surveillance powers, told Mashable in January.
"From the beginning, [SORM] was more totalitarian, more invasive, more flexible, and in some ways even more effective than the Western approach," Soldatov said previously.
http://mashable.com/2014/04/17/snowd...-surveillance/
-
04-24-2014, 09:05 AM #564AprilGuest
NSA Finally Reveals How PRISM Works, But It's Nothing New

A sign outside the National Security Administration (NSA) campus in Fort Meade, Md. on June 6, 2013. Image: Patrick Semansky/Associated Press
 By Lorenzo Franceschi-Bicchierai1 day ago
By Lorenzo Franceschi-Bicchierai1 day ago
The NSA has finally decided to tell the world how the Internet surveillance program PRISM works, though it's been almost a year since its existence was revealed by one of the very first Edward Snowden leaks.
On Tuesday, the spy agency released a report on Section 702 of the Foreign Intelligence Surveillance Act (FISA), which is the legal justification for PRISM. The document explains how the NSA collects Internet data but, perhaps unsurprisingly, it reveals almost nothing new.
However, even though it doesn't go into many technical details, it appears to confirm that the program pretty much works the way two security researchers theorized back in June.
See also: This Is How the NSA Is Trying to Win Over the Media
Ashkan Soltani, a security and privacy researcher, along with another researcher, nicknamed semipr0, drew up an infographic based on the information leaked by Snowden, as well as news reports.
In their model, PRISM is a system with which the NSA requests data from tech companies, through the FBI. The tech companies then send the requested information to the spy agency via different technical means.

In the newly released document, dated April 16, the NSA's Office of Civil Liberties and Privacy confirms that its collection of Internet data happens always with "the knowledge of the service providers." And the document clarifies that the NSA doesn't have direct access to the companies' servers, as the first reports of PRISM wrongly indicated. Tech companies have repeatedly denied their knowledge of PRISM since it was uncovered.
This collection can happen two ways.
The first one is via the PRISM program, which legally compels service providers (in this case presumably Google, Facebook, Yahoo and others) to turn over to the NSA the communications to and from a target, which the NSA refers to as "selector." The second way is by compelling service providers (in this case ISPs like AT&T) to "lawfully intercept" (read: "tap") Internet traffic going through their networks. This process has usually been referred to as "upstream" collection.
http://mashable.com/2014/04/22/nsa-prism-report/
-
04-27-2014, 12:18 PM #565AprilGuest
-
05-07-2014, 06:24 PM #566Senior Member


- Join Date
- May 2007
- Location
- South West Florida (Behind friendly lines but still in Occupied Territory)
- Posts
- 117,696
NSA to Control the Stock Market
Spy agency can easily manipulate the market through latest surveillance hub
Kit Daniels
Infowars.com
May 7, 2014
An upcoming surveillance hub monitoring all investment transactions in real-time will allow the National Security Agency unparalleled ability to manipulate the stock market.
Through the use of the Financial Industry Regulatory Authority (FINRA)’s latest database, which keeps investor data in the same centralized location, the NSA could easily capture private, financial data on targeted investors and even influence the stock market as a whole.
And it appears that the dragnet database, called the Comprehensive Automated Risk Data System (CARDS), was designed with such vulnerabilities in mind.
“I can’t think of any other reason that someone would invest so much time and so much effort into trying to monitor every brokerage account in the United States in real time,” Porter Stansberry, the founder of the Stansberry & Associates Investment Research Conference, said on the Alex Jones Show. “That is an enormous technical challenge.”
He also added that even knowing something as simple as how many individual investors own certain securities could be very, very valuable to select interests.
And other revelations in the past reveal that the NSA is more than willing to monitor and manipulate financial transactions.
Last December, the White House report on the activities of the NSA suggested that the spy agency was already hacking into financial institutions and altering the amounts held in bank accounts.
“Governments should not use their offensive cyber capabilities to change the amounts held in financial accounts or otherwise manipulate the financial systems,” the report recommended.
Trevor Timm, a former analyst at the Electronic Frontier Foundation, asked if the recommendation implied that the NSA was already doing just that.
And a few month earlier, in September, German news outlet Der Spiegel reported that the spy agency was also tracking the global flow of money.
Under the “Follow the Money” program, the NSA collects credit card and other financial transactions into its own financial databank, called “Tracfin,” which contains nearly 200 million records if not more.
“Further NSA documents from 2010 show that the NSA also targets the transactions of customers of large credit card companies like VISA for surveillance,” the article continued. “NSA analysts at an internal conference that year described in detail how they had apparently successfully searched through the U.S. company’s complex transaction network for tapping possibilities.”
And the upcoming CARDS database, which a law professor suggested is as tempting of a target as the American fleet at Pearl Harbor, would grant the NSA almost unlimited possibilities to influence the stock market.
Alex Jones will make a rare public appearance as a featured speaker at the upcoming Stansberry & Associates Investment Research Conference in Dallas, Texas on Saturday, May 31. For more information and tickets, please visit alexjonesdallas.com.
This article was posted: Wednesday, May 7, 2014 at 3:33 pm
Related Articles
- Is the NSA manipulating the stock market?
- IPO market is casualty of stock market pullback
- Last decade was the worst ever in the stock market
- IRS to Expand Financial Surveillance With Crackdown On Offshore Accounts
- Blow 12% of your income in the stock market
http://www.infowars.com/nsa-to-contr...-stock-market/
Join our efforts to Secure America's Borders and End Illegal Immigration by Joining ALIPAC's E-Mail Alerts network (CLICK HERE)
-
05-09-2014, 08:23 PM #567Senior Member


- Join Date
- May 2007
- Location
- South West Florida (Behind friendly lines but still in Occupied Territory)
- Posts
- 117,696
US accuses Israel of ‘alarming, even terrifying’ levels of spying

As Obama aides refer darkly to ‘red lines’ rarely crossed before in decades of mutual eavesdropping, Rupert Cornwell investigates a diplomatic bust-up that reveals how even the closest relationships between allies have unspoken limits
Rupert Cornwell
Washington
Thursday 08 May 2014
Friends do not spy on friends. That illusion about America’s attitude to its allies was conclusively debunked by Edward Snowden’s revelations about America’s National Security Agency and its British partner in global electronic eavesdropping, GCHQ. But by every account, the US is being repaid in kind by one of its closest international friends – Israel.
Israel has been trying to steal secrets from the US, its principal protector and benefactor, but also occasional rival, ever since the inception of the Jewish state in 1948, and even before. But according to the latest issue of Newsweek, quoting Obama administration officials, these activities have “crossed red lines” rarely encountered in the past.
In the words of one Congressional aide, with access to classified briefings in January on the subject, Israel’s behaviour was “very sobering…?alarming…?even terrifying”. Israel, it would appear, is after everything it can lay its hands on: not just diplomatic and policy documents, but industrial and military technology. The means include Israeli trade missions to the US, joint ventures between Israeli and American companies and, presumably, spying by Israeli intelligence agencies.
“Everyone does it,” is a common reaction to such claims of ungentlemanly conduct. But by these accounts, in the case of America no one does it like Israel – not even allies with intelligence services as skilled as those of France, Germany, even the UK.
The latest charges surfaced as Susan Rice, Mr Obama’s national security adviser, was on a visit to Jerusalem to discuss the Middle East peace process, Iran and other regional issues. They have drawn predictable, outraged denials from Israeli spokesmen. “A malicious fabrication aimed at harming relations,” declared Avigdor Lieberman, the Foreign Minister, adding that “we do not engage in espionage in the US, neither directly nor indirectly”. Off the record, other officials mutter darkly about anti-Semitism.
http://www.independent.co.uk/news/wo...g-9341264.htmlJoin our efforts to Secure America's Borders and End Illegal Immigration by Joining ALIPAC's E-Mail Alerts network (CLICK HERE)
-
05-15-2014, 10:12 PM #568Senior Member


- Join Date
- May 2007
- Location
- South West Florida (Behind friendly lines but still in Occupied Territory)
- Posts
- 117,696
WikiLeaks: About 80 Companies Cooperating With NSA; Intel, IBM, Microsoft Included
Posted on May 15, 2014 by Pushpa Mishra
As if the Snowden revelations were not enough, we have yet another startling claim by WikiLeaks stating that nearly a hundred corporations colluded with NSA in its surveillance programs.
The tweet from WikiLeaks says,“80 corporations have been bribed or coopted by NSA including Intel, CISCO, IBM, Oracle, Microsoft, AT&T, Qualcom”The WikiLeaks have got hold of some NSA documents that has names of the corporations that collaborated with the intelligence agencies to snoop on digital data.
 Image credit: PBS
Image credit: PBS
The obtained slides state about 80 ‘Major Global Corporations’ are supporting BOTH missions; however, there is no clear indication as to what ‘both missions’ stand for.
Taking a lead from the cue that the slide is labeled as COMINT, it can be safely inferred that ‘Both’ refer to communications between people.
Some of the listed companies include well-known global organizations, such as Telecommunications and Network Service Providers – AT&T, Verizon and Qwest (now part of Centurylink); Network Infrastructure – Cisco and HP; Hardware Platforms Desktops/Servers – HP, Intel, Qualcomm, IBM, EDS (now HP); Operating Systems – Microsoft; Applications Software – Oracle, EDS (now HP) and Microsoft; Security Hardware and Software – Cisco, Oracle, EDS (now HP); System Integrators – HP, IBM, Cisco and EDS (now HP)
This is the first time ever a documented list of company names engaged with NSA has been highlighted.
These companies had earlier refuted charges of working in collusion with the intelligence agencies when NSA’s PRISM activities were disclosed. Some of them even alleged being victimized or attacked by the government for refusing to cooperate with the intelligence agencies.
HackRead has many articles on companies–NSA association: refusal and charges.While the information made public by WikiLeaks only corroborates the common men’s suspicion about the NSA and corporations working together, it is bit intriguing that WikiLeaks has not made public the full list of organizations. WikiLeaks is notoriously famous for making documents public that shames the US government.
- See: IBM sued by its own shareholder for cooperating with the NSA
- A UK citizen has sued Microsoft for leaking Prism private data to the NSA
- We never share info with NSA, you can still use internet anonymously: Country Director of Google in Brazil
- Hacked Emails Show How Much Microsoft Charges FBI for Selling Your Personal Data
http://hackread.com/wikileaks-80-companies-helping-nsa/
Join our efforts to Secure America's Borders and End Illegal Immigration by Joining ALIPAC's E-Mail Alerts network (CLICK HERE)
-
05-24-2014, 02:41 PM #569AprilGuest
The Pentagon report on Snowden's 'grave' threat is gravely overblown
NSA defenders still won't tell the whole truth, but a newly revealed damage assessment offers a window into government damage control – not any actual damage done by Snowden
-

- Julian Sanchez in Washington
 Edward Snowden, shown here in an image from an NBC News interview to be broadcast next week, copied documents classified as top secret, so they can be expected to cause exceptionally 'grave' damage, almost by definition. Photograph: NBC News
Edward Snowden, shown here in an image from an NBC News interview to be broadcast next week, copied documents classified as top secret, so they can be expected to cause exceptionally 'grave' damage, almost by definition. Photograph: NBC News
For months, defenders of America's spy agencies have been touting a classified Pentagon report as proof that Edward Snowden's unprecedented disclosures have grievously harmed intelligence operations and placed American lives at risk. But heavily redacted excerpts of that report, obtained by the Guardian under a Freedom of Information Act request and published on Thursday, suggest that those harms may be largely hypothetical – an attempt to scare spy-loving legislators with the phantoms of lost capability.
The first thing to note is that the Pentagon report does not concern the putative harm of disclosures about the National Security Agency programs that have been the focus of almost all Snowden-inspired stories published to date. Rather, the Defense Intelligence Agency's damage assessment deals only with the potential impact of "non-NSA Defense material" that the government believes Snowden may have obtained. Any harm resulting from the disclosure of NSA-related material – in other words, almost everything actually made public thus far – is not included in this assessment.
In fact, the unredacted portions of the report don't discuss published material at all. Instead, the Pentagon was assessing the significance of the information "compromised" by Snowden – all the documents they believe he copied, whether or not they ever see the light of day.
It certainly makes sense for the government to try to gauge the harm that could result if all that information was disclosed, but that's very different from saying harm has occurred. There is always the risk that a hostile government could somehow gain access to the Snowden cache, but the journalists with access to that trove say Snowden himself has insisted that they exercise discretion, publishing only material whose disclosure is in the public interest.
Even that estimate of possible harm, however, is almost certainly overblown. Astonishingly, the government still appears not to have any idea how much information Snowden copied. Intelligence officials estimate that he accessed some 1.7m documents, and are operating on the assumption that he took every document he had access to. Yet there's no reason to believe that assumption is true, and journalist Glenn Greenwald – one of the few with full access to the Snowden trove – has consistently described it as containing "tens of thousands" of documents, not millions.
The almost complete lack of details in the redacted report make it difficult to evaluate it with confidence, but the Pentagon's assessment that the compromised information "will have a GRAVE impact on U.S. national defense" may reflect little more than the government's own unrealistic definitions. After all, by executive order, documents are supposed to be classified as "top secret" only if they "reasonably could be expected to cause exceptionally grave damage to national security". Snowden obviously copied many documents classified as top secret – so they can be expected to cause exceptionally grave damage, by definition.
Except, of course, that's not automatically true. But don't take my word for it: just ask former Director of National Intelligence Dennis Blair, who in 2009 acknowledged that "there is a great deal of over-classification" in government. "Some of it, I think, is done for the wrong reasons, to try to hide things from the light of day," Blair explained. "Some of it is because in our system, there is no incentive not to do that, and there are penalties to do the reverse, in case you get something wrong and don't classify it."
In this, Blair echoed the findings of a formal intelligence community review, which concluded that terms like "grave damage" were not used in any clear or consistent way across the community. As a result, documents are routinely classified without any explanation of how or why their disclosure would be harmful. Current DNI James Clapper has even said that the government should have voluntarily revealed the most notorious program leaked by Snowden: the NSA's vast database of telephone records. Presumably Clapper was not suggesting that the government should have voluntarily inflicted grave harm on national security.
In short: the Pentagon damage report concludes that the "staggering" cache of documents that Snowden might have taken (most of which he probably didn't) could potentially cause grave harm if disclosed to a foreign power (which, as far as we know, they haven't been), and assumed that only genuinely super-sensitive information gets classified (which top intelligence officials concede isn't true).
If this be treason, then the bar has fallen awfully low these days. But we can rest assured that Edward Snowden's critics will make the most of it all the same – anything to distract from the grave impact NSA has already had on global privacy.
http://www.theguardian.com/commentis...reat-overblown
-
-
05-24-2014, 02:43 PM #570AprilGuest
The NSA reform bill now shuts down a secret database. Will that fix anything?
A detailed look into the future of America's phone dragnet reveals a world without the nuclear bomb of the Snowden revelations. Unless, of course, the telecoms set it off
 A new provision to the USA Freedom Act would force the government to 'adopt minimization procedures that require the prompt destruction of all call detail records' handed off to the so-called 'corporate store'. Photograph: Chairman of the Joint Chiefs of Staff / Flickr via Creative Commons
A new provision to the USA Freedom Act would force the government to 'adopt minimization procedures that require the prompt destruction of all call detail records' handed off to the so-called 'corporate store'. Photograph: Chairman of the Joint Chiefs of Staff / Flickr via Creative Commons
A last-minute change to the National Security Agency reform bill making its way through Congress, as reported by the Guardian on Tuesday afternoon, may minimize one of the greatest dangers of the program. Or it may make things far worse!
At issue is the number of completely innocent Americans who will be subjected to the NSA’s scrutiny under the new, reformed phone dragnet, in which the telecoms retain the data but conduct queries for the NSA. Language added to the USA Freedom Act, which is scheduled for a House floor vote on Thursday, may limit how much of the data on those innocent Americans the NSA can actually keep – and for how long.
To understand the risk going forward, of course, it helps to understand how your phone calls get sucked up right now. But going forward, somebody’s going to have to make it very clear whether it will be the telecoms or the NSA removing numbers from the database. Otherwise you’re still going to be spied on for liking the same kind of pizza as a terrorist.
Inside the ‘corporate store’: how your calls are analyzed now
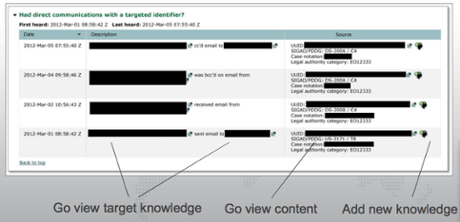 According to a newly released document obtained by Edward Snowden, the NSA matches newly collected metadata against existing collections to evaluate 'foreign intelligence purpose'. (via the Intercept) When defenders of the NSA try to make people less worried about its phone dragnet, which currently collects a significant portion of all the phone records in the US, they claim that its massive database isn’t subjected to the NSA’s most advanced computer analysis. “There is no data mining, there’s no powerful algorithms chugging through it, trying to imagine relationships,” former NSA Director Michael Hayden claimed at a debate the other week.
According to a newly released document obtained by Edward Snowden, the NSA matches newly collected metadata against existing collections to evaluate 'foreign intelligence purpose'. (via the Intercept) When defenders of the NSA try to make people less worried about its phone dragnet, which currently collects a significant portion of all the phone records in the US, they claim that its massive database isn’t subjected to the NSA’s most advanced computer analysis. “There is no data mining, there’s no powerful algorithms chugging through it, trying to imagine relationships,” former NSA Director Michael Hayden claimed at a debate the other week.
The defenders claim the NSA will never have a way to track your calls to your psychologist, or your secret girlfriend. But that’s only true if your calls don’t get sucked up in one of the queries the NSA runs on people suspected of ties to terrorism.
If they do get sucked up, your calls can be dumped into what is often called the “corporate store” – a database of all the phone dragnet query results, and the nuclear bomb hiding inside the Snowden revelations.
Once your records are in the corporate store, they become subject to what court documents describe as “the full range of [NSA's] analytic tradecraft”. That means the NSA can start checking to see who else you called, using algorithms to try to map out all your relationships – perhaps even tying your phone number to your email and social media identities and tracking those relationships, along with what you search and read online.
In addition, since 2011, the NSA has been permitted to use Americans’ phone numbers to search – and in some cases to access the content of – phone calls they’ve already collected. So, while the phone dragnet doesn’t currently include call content, it can provide a way for the NSA to access the content of your calls.
Worse still, there are few safeguards. While the NSA needs a “foreign intelligence purpose” to start looking at this collected phone numbers, they don’t need to have any basis for suspecting you have ties to terrorism. The NSA doesn’t have to audit these searches, either – they can apparently, under the current program, keep the data forever. That needs to change.
A method to the madness: why your calls get hoovered, too
 A watchdog report released in January recommended the NSA possess the same 'reasonable articulable suspicion' in the so-called 'corporate store'. (via Privacy and Civil Liberties Oversight Board) You may be thinking you have nothing to worry about. Because neither you nor your friends talk to terrorists, right?
A watchdog report released in January recommended the NSA possess the same 'reasonable articulable suspicion' in the so-called 'corporate store'. (via Privacy and Civil Liberties Oversight Board) You may be thinking you have nothing to worry about. Because neither you nor your friends talk to terrorists, right?
But it’s possible to get sucked up without talking to terrorists, via some other common number – a voice-mail dial-in, or a telemarketer, or a pizza place. A Stanford study conducted last year discovered that even among a group of 300 people with almost no mutual ties, over 17% were connected on the second so-called “hop” – or degrees of separation – through T-Mobile’s voice mailbox system, with other common numbers like Comcast and FedEx linking other people on a second hop. In a watchdog report issued earlier this year, the Privacy and Civil Liberties Oversight Board estimated that as many as 120m phone numbers a year may have gotten sucked into the NSA’s analytical maw.
So you may not talk to terrorists, but if you and a suspected terrorist both use FedEx, you still might have your most intimate relationships exposed to NSA’s analysis.
Right now, the NSA tries to minimize the number of innocent people whose call records get sucked up in queries by taking those voicemail and cable provider numbers out of the database … though local pizza joints may be harder to spot.
But it’s unclear what will happen if the phone dragnet reform passes Congress. Will AT&T and Verizon pull out all these numbers for the government? Because if they don’t, an even larger number of innocent Americans will get exposed to NSA’s intrusive analysis than under the current system.
A still-broken process: how will the NSA decide if you’re trouble?
As the Guardian is now reporting, new language in the USA Freedom Act may ensure that even if the NSA gets all these phone records of innocent Americans, they won’t be able to keep them. The bill that passed two committees of Congress and is barreling toward a vote only required the NSA to destroy data they received after five years – and even then, only if it wasn’t related to a terrorism investigation … which all the data, by definition, was, because it had been sucked up!
So the old language basically permitted the NSA to keep whatever it got for as long as it wanted.
The new language would “require the prompt destruction of all call detail records” turned over by the telecoms “that the Government determines are not foreign intelligence information.” At least in theory, this legislation would force the NSA to destroy data if it discovered that it had gotten your phone number because you like the same pizza as a suspected terrorist does.
But in the process, the language actually seems to expand the reasons the NSA can keep your data, beyond a tie to terrorism to include “foreign intelligence information”. If the NSA thinks you have interesting friends and relatives in China or Russia or anywhere else, it might keep your data. If it thinks you have ties to the drug trade, it might keep your data. If you work for an interesting foreign-owned company, it might keep the data.
Plus, what process is the NSA going to use to decide if your phone number – after all, it’s just a number, without a name – is “foreign intelligence information” or not? The NSA has to conduct some seriously intrusive analysis just to determine if your phone number amounts to foreign intelligence information!
So to learn enough about your phone number to decide to destroy it, the NSA probably has to do intrusive searches on your number.
Alas, even if Tuesday’s markup changes represent a breakthrough, Americans may be far too intertwined – both the terrorists and completely innocent pizza fans – to bake in true privacy without more oversight.
http://www.theguardian.com/commentis...store-analysis


 27Likes
27Likes LinkBack URL
LinkBack URL About LinkBacks
About LinkBacks




 Reply With Quote
Reply With Quote




Ukraine-Israel Bill Secretly Funds Biden's invasion!
04-24-2024, 12:01 PM in illegal immigration Announcements