Results 21 to 30 of 49
Thread Information
Users Browsing this Thread
There are currently 1 users browsing this thread. (0 members and 1 guests)
-
07-13-2013, 03:35 PM #21
Hardening Ubuntu Linux
http://www.insanitybit.com/2012/12/1...-ubuntu-linux/
December 17, 2012 by insanitybit
Im going to keep some tips here for users looking to improve their security, when I update it Ill tweet about it, so feel free to follow me @insanitybit. This is aimed at desktop users but naturally lots of it can apply to a Linux server. Some of this will be simple, trivial, and some of this will be quite a bit more difficult. Im focusing specifically on Ubuntu but other distros will have similar features (replace Apparmor with SELinux). I will try to make this as comprehensive as possible, though Im specifically avoiding items like Fail2Ban as its not really useful for users. You can consider this an extension of my definitive guides The Definitive Guide For Securing Linux Ubuntu.
A lot of users believe that a distro such as Ubuntu will be so much more secure than Windows, purely through virtue of obscurity. As Linux popularity continues to grow youll see attackers begin to take notice. Just because attackers dont care to hack Linux desktop systems does not by any means imply they arent capable of it, or ready to when it seems profitable.
Thankfully, Linux is really easy to secure. Despite some problems there are a lot of powerful projects that give users the power to secure themselves against many threats.
Securing Your Browser
First Id like to start by linking to my guides for locking down Chrome and Firefox As a user your most exploitable area is your browser, its constantly taking in untrusted content, often over an insecure connection. I personally love Chromes Linux sandbox, but Firefox with NoScript is very powerful as well I leave it to you to decide between the two based on your needs.
Enabling Ubuntus Firewall
Ubuntu comes with a firewall utility called UFW, but it isnt enabled by default. The reason is that, by default, Ubuntu doesnt have any open ports open (except for system services that are typically necessary for the average user). So is a Firewall strictly necessary? Well, if youre behind a NAT router not so much, any open ports will expose you to local attacks, but youre hidden from the internet. Still, if youre looking to secure your system you can simply run this command:ufw enableAnd it should prevent inbound access. You can create complex rules via iptables to restrict or relax your rules. You can also check out GUFW for a graphic interface to UFW. GUFW makes everything very easy to use.
ufw default deny incoming
You can use UFW/GUFW to create outbound rules for applications. Due to the amount that applications within a user ID can interfere with one another I do not feel that an outbound firewall is worthwhile for security, and it can be quite a bit of a pain. If youre serious about setting up an outbound firewall I suggest you make strict use of user separation and apparmor, though even then the benefits are questionable (there is a reason programs like Comodo on Windows bundle their firewall components with strict HIPS software).
See this guide for further information on setting up firewalls. Courtesy of a very smart guy, Dangertux.
Run a Program As A Separate User
While the simplest way to restrict a program is AppArmor (see below) you can also make use of the native user/group Linux permissions in order to run an application as a different user. Ive written a guide with Pidgin as the example. Separated programs will have less access to one another and theyll live in a different user directory, with access only to that directory.
By separating a program to a new user we can also write more powerful firewall rules, as the program wont be able to bypass an outbound rule as trivially.
For a risky program that doesnt need to access other programs this may be a very viable option. For example, I run Xchat, which hasnt been updated in about two years. For a program like this throwing as much security as possible at it isnt a bad idea, since it doesnt get patches, doesnt use modern security techniques, and is internet facing.
Restricting DMESG
By default unprivileged users can read a lot of your systems logs. These logs can contain critical information for an attacker hoping to exploit your system further.
This is useful for debugging, but youre not likely to have to do that. Running this command will prevent access by unprivileged users:echo kernel.dmesg_restrict = 1 >> /etc/sysctl.confThis feature is also included in the Grsecurity patch.
Removing Attack Surface
One of the first steps to harden any operating system should always be disabling unnecessary programs/ services. Desktop operating systems dont come default secure they come default compatible and that means meeting the needs of every person, generically. So while John may use his network printer Jane may not, but Janes system still comes with all of the attack surface necessary for network printing.
The network printing service is cupsd. It comes, by default, in an Apparmor profile, so its not like you should be incredibly worried about being exploited. And if youre behind NAT youre only exposed to local attacks. But, if youre like me, you dont print over a network and you have no need for this service. Are you likely to be attacked over it? Maybe, maybe not, but its not needed. So go ahead and remove that service.
You can check for programs listening on your system with the following command:netstat -tulnpLook up any services and carefully consider the benefit/ necessity of them. If you dont need them or want them, remove them.
Another tip is to use checksec.sh. Run the following command: (You must first set the file as executable)./checksec.sh proc-allIt will provide you with a list of running services along with information about their security whether they use NX, stack canaries, and if theyve been compiled as Position Independent Executables (PIE). This may help you make a more informed decision about removing a service.
Mount /tmp With noexec,nodev,nosuid
Many programs require read/write access to /tmp but, for the most part, no programs actually need to be able to execute from there. Mounting this area with the noexec, nodev, nosuid can provide some level of security. Rather than creating a new partition for /tmp I find its just easier to use RAM (it expands as needed and doesnt require partitioning , one benefit being a (potential) performance increase, though I wouldnt bet on it.
Copy the following into your /etc/fstab file.tmpfs /tmp tmpfs mode=1777,nosuid,nodev,noexec 0 0If you want to create a new partition for /tmp you can find a guide online for that. Its kinda a pain. The downside to running it in RAM is, obviously, you lose some RAM. If you want to limit the amount of RAM it can use (tmpfs expands as needed) you can change the line to (for 512M):tmpfs /tmp tmpfs size=512M,mode=1777,nosuid,nodev,noexec 0 0I recommend that if you follow the above you make use of AppArmor to improve the level of security this adds. If you use /tmp in RAM one benefit is that, in your AppArmor profiles, you should be able to remove map rules for some programs that map /tmp for performance reasons.
AppArmor
AppArmor is the Linux Security Module of choice for Ubuntu. It implements Mandatory Access Control on a per-process basis. Its very simple to learn how to use AppArmor and Ive written a guide. In the guide I provide tips for creating strong AppArmor profiles and avoiding potential pitfalls.
A program like Pidgin has a lot of access to your system. It runs as the same user as many other programs on your system and therefor is granted a fair amount of control over them. It can read many areas of the system that it doesnt need to read, it can write to quite a few too. AppArmor restricts it to only the resources it needs, making both remote and local privilege exploits more difficult to pull off.
Ive written a few very strict AppArmor profiles myself that youre welcome to use as a starting point. [Xchat][Pulseaudio] [Java]
32bit users will have to adjust as needed, though it should be as simple as replacing the x86_64 with i386 (Ill add variables for this at some point so you wont have to).
Every internet facing program deserves an AppArmor profiles. Its the simplest way to implement least privilege on a per application basis.
PaX and Grsecurity
PaX and Grsecurity are patches for the Linux kernel (the Grsecurity patch contains both, dont just use PaX). PaX and Grsecurity have been at the forefront of security for more than a decade, bringing some of the most important security mitigation techniques to systems today, such as Address Space Layout Randomization (ASLR). ASLR is a great example of a mitigation technique that doesnt have a great implementation in typical vanilla systems. The ASLR in your average distro, like Ubuntu, introduces far less entropy into the system, which degrades its use. The ASLR is also missing critical features, such as brute force deterrence, among others. PaX and Grsecurity bring these features and many many others to Linux. No operating system has as complete ASLR as PaX and, really, nothing else compares.
Not all of these features are compatible for desktop users, or even necessary, but a number of them will work on an Ubuntu desktop. You can see my guide for patching and compiling a Grsecurity Linux kernel, with notes about compatibility issues for desktop users.
Many of these security features directly relate to desktop security. Many applications and services use chroot to run programs in a separate environment. Chroot is incapable of restricting programs that can run as root, multiple bypasses are possible. Chrome is one such program, along with many other services (like avahi-daemon), so using the chroot hardening features of Grsecurity will provide a considerably more secure environment.
PaX and Grsecurity can be implemented with very little performance overhead, and very few stability issues if configured properly. If youre really looking to secure your Linux system and youre willing to take the time to compile it you should give it a try.
Learn how to compile your own Grsecurity Linux kernel here.
Patching
None of the above will make up for a system that is out of date and unpatched. If youre using an older kernel and userland applications an attacker will be able to chain together enough exploits to bypass any restrictions/ measures youve taken, no matter how powerful. Make sure to stay up to date for all applications.
You can push patch time further by hardening the system time to develop an exploit for a hardened system is longer. This does not mean you can postpone indefinitely, it just buys you time to test patches and improve your patch management.
Something To Keep In Mind
This all works best in conjunction. Grsecurity and PaX are honestly the best security software there is, in my opinion, but they cant make up for a completely insecure userland. If youre running programs that opt out or dont make use of modern technology theres only so much they can do. Its very unfortunate but, even on 64bit, Ubuntu ships with a lot of services not using Position Independent Executable code at this point its necessary to harden the programs in other ways.
And the same goes both ways. If youre not using Grsecurity and PaX then your kernel is less secure, meaning that even if you harden a userland application with apparmor an attacker will have a much easier time exploiting the kernel and escaping the profile.
If youre annoyed about your distro coming with insecure settings email them about it. You can reach Canonical:
http://www.canonical.com/about-canonical/contactyou have suggestions for canonical.com or ubuntu.com, please email us atwebmaster@canonical.com or webmaster@ubuntu.com.And if you have any suggestions for this guide please let me know in a comment. Ill happily include any relevant information.
Follow me @insanitybit for updates and more articles like this.
This also works for Linux Mint users.............ReciprocityIn questions of power let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution. Thomas Jefferson
-
07-13-2013, 07:13 PM #22
'NSA-Proof' Web Surfing?
http://video.foxbusiness.com/v/25387...cmp=fbfeaturesIn questions of power let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution. Thomas Jefferson
-
07-14-2013, 02:46 PM #23
The Hut Where the Internet Began
The Hut Where the Internet Began
When Douglas Engelbart read a Vannevar Bush essay on a Philippine island in the aftermath of World War II, he found the conceptual space to imagine what would become our Internet.
Alexis C. MadrigalJul 7 2013, 11:18 PM ET
1
inShare
 Let's start at the end point: what you're doing right now. You are pulling information from a network onto a screen, enhancing your embodied experience with a communication web filled with people and machines. You do this by pointing and clicking, tapping a few commands, organizing your thoughts into symbols that can be read and improved by your various correspondents.
Let's start at the end point: what you're doing right now. You are pulling information from a network onto a screen, enhancing your embodied experience with a communication web filled with people and machines. You do this by pointing and clicking, tapping a few commands, organizing your thoughts into symbols that can be read and improved by your various correspondents.
There was a beginning to all this, long before it became technically possible.
Well, actually, there were many beginnings.
But one -- maybe the most important one -- traces back to Douglas Engelbart, who died last week, and his encounter with a 1945 article published here at The Atlantic, "As We May Think," by Vannevar Bush, an icon of mid-century science.
The essay is most famous for its description of a hypothetical information-retrieval system, the Memex, a kind of mechanical Evernote, in which a person's every "book, record, or communication" was microfilmed and cataloged.
"It is an enlarged intimate supplement to his memory," Bush wrote. "It consists of a desk, and while it can presumably be operated from a distance, it is primarily the piece of furniture at which he works. On the top are slanting translucent screens, on which material can be projected for convenient reading. There is a keyboard, and sets of buttons and levers. Otherwise it looks like an ordinary desk."
Bush did not describe the screens, keyboard, buttons, and levers as a "user interface" because the concept did not exist. Neither did semiconductors or almost any other piece of the world's computing and networking infrastructure except a handful of military computers and some automatic telephone switches (the latter were, in fact, one of Bush's favorite examples).
A crucial component of the Memex was that it helped the brain's natural "associative indexing," so "any item may be caused at will to select immediately and automatically another." The Memex storehouse was made usable by the "trails" that the user (another word that did not have this meaning at the time) cut through all the information, paths that could later be refollowed or passed onto a friend.
("There is a new profession of trail blazers, those who find delight in the task of establishing useful trails through the enormous mass of the common record," Bush predicted. Consider for a moment that these processes -- at scale -- are exactly what makes Google a good search engine or Reddit a good social news site.)
Bush's essay was a groundbreaking ceremony for the information age. In Bush's own terms, the complexity of the world and its problems required a better system, lest our memories and minds become overwhelmed by all there was to know. And this was not merely a personal, lifestyle problem. The worst war the world had ever known was finally coming to a close, and to a man like Bush, it had begun because of a lack of human wisdom. This is how his essay ends:
The applications of science have built man a well-supplied house, and are teaching him to live healthily therein. They have enabled him to throw masses of people against one another with cruel weapons. They may yet allow him truly to encompass the great record and to grow in the wisdom of race experience. He may perish in conflict before he learns to wield that record for his true good. Yet, in the application of science to the needs and desires of man, it would seem to be a singularly unfortunate stage at which to terminate the process, or to lose hope as to the outcome.What Bush knew when he wrote these words in the months leading up to July 1945 was that the most cruel weapon had been invented: American atomic bombs would not fall on Japan for two more months, but Bush had been intimately involved in their creation and certainly knew their use was a possibility. With that knowledge in his pocket, his answer to the prospective (and then real) horrors of science-enabled nuclear war -- odd as it may seem -- was to imagine a contraption to aid human knowledge acquisition.
For Bush, humans were racing against themselves: understand the complex world or face extinction through war. Those were the stakes at the outset of the information age.
Bush's article went far and wide, and if I can brag for our magazine a little, is considered one of the most influential magazine articles ever published about technology, and perhaps in any field. It even landed inside LIFE Magazine in a condensed format in September of 1945.
 The Memex as imagined by a LIFE illustrator.
The Memex as imagined by a LIFE illustrator.
Millions of copies of the September 10 issue were printed and distributed around the world. LIFE had established itself as the preeminent photo chronicler of World War II and the Red Cross habitually kept reading materials like it around for soldiers. And so it was that a copy of that issue, containing most of Bush's article -- including the whole Memex section and conclusion quoted here -- made its way to a Red Cross library on the (even now, still remote) island of Leyte in the Philippines.
Meanwhile, young Doug Engelbart, a radar technician in the Navy who never saw combat (the war ended as his boat pulled out of the San Francisco Bay), was on his way to the Philippines, too. He was transferred to Leyte, the island, and though the record is not precisely clear on this point, perhaps to the little village called Leyte, too, at the end of a long inlet. It was here that, in the words of John Markoff, Engelbart "stumbled across a Red Cross reading library in a native hut set on stilts, complete with thatched roof and plentiful bamboo." Five years ago, a visitor to Leyte snapped this photograph of the the town of Leyte.

In a hut like this -- and maybe even one of these huts specifically -- Engelbart opened up that issue of LIFE and read Bush's Atlantic article. The ideas in the story plowed new intellectual terrain for Engelbart, and the seeds that he planted and nurtured there over the next twenty years grew, with the help of millions of others, into the Internet you see today.
The Los Angeles Times obituary succinctly summed up his impact on the world: "Douglas Engelbart, whose work inspired generations of scientists, demonstrated in the 1960s what could happen when computers talk to one another." Steve Wozniak went further, crediting Engelbart's 1960s research "for everything we have in the way computers work today." Yes, he invented the mouse, but he also laid out the concepts we'd need to understand the networked world.
So, in one tangible and real sense, the Internet we know now began in that hut across the world. As Bush made new thoughts possible for Engelbart, Engelbart made it possible for us to imagine the rest of it.
Engelbart wrote Bush a letter describing how profoundly he'd been affected by the latter's work. "I might add that this article of yours has probably influenced me quite basically. I remember finding it and avidly reading it in a Red Cross library on the edge of the jungle on Leyte, one of the Philippine Islands, in the fall of 1945," he wrote. "I rediscovered your article about three years ago, and was rather startled to realized how much I had aligned my sights along the vector you had described. I wouldn't be surprised at all if the reading of this article sixteen and a half years ago hadn't had a real influence on my thoughts and actions."
What's fascinating is that Engelbart adopted Bush's frame for the key problems and solutions of modern life. Bush worried that the world had gotten too big to understand, and so did Engelbart. "The complexity/urgency factor had transcended what humans can cope with," he recalled in a 1996 oral history interview. "I suddenly flashed that if you could do something to improve human capability with that, then you'd really contribute something basic."
The problem framed in this way helped Engelbart stay away from the artificial intelligence researchers like JCR Licklider. Instead, he developed a framework for helping human minds to come together to improve themselves. He did not think the machines could or should do the thinking for us. Markoff, a long-time chronicler of computing, sees Engelbart as one pole in a decades-long competition "between artificial intelligence and intelligence augmentation -- A.I. versus I.A." That's because Engelbart's view of computing development retained a privileged place for humans. His academic biographer Thierry Bardini summed up his importance like this:
Many still credit him only with technological innovations like the mouse, the outline processor, the electronic-mail system, or sometimes, the windowed user interface. These indeed are major innovations, and today they have become pervasive in the environments in which people work and play. But Douglas Engelbart never really gets credit for the larger contribution that he worked to create: an integrative and comprehensive framework that ties together the technological and social aspects of personal computing technology. Engelbart articulated a vision of the world in which these pervasive innovations are supposed to find their proper place. He and other innovators of this new technology defined its future on the basis of their own aspirations and ideologies. Those aspirations included nothing less than the development via the interface between computers and their users, of a new kind of person, one better equipped to deal with the increasing complexities of the modern world.A new kind of person. The words appear unseemly in a reactionary age that reifies the "real world," but consider the root of the desire for a new humanity: Tracing Engelbart back through Bush, we find the horror of World War II and the nuclear weapons that put nearly instant human extinction on the table for the first time in human history. Mere tinkering around the edges of humanity would not have seemed up to the task.
What emerged for Engelbart as a real answer to Bush's statement of the problem was the co-evolution of humans and technology. Knowing that machines could do some thing well, and humans others, Engelbart imagined creating interfaces that would allow both to continue improving. It is an optimistic and hopeful outlook, one that is less brittle than hoping Watson will cure disease or that humans are deracinated by our contact with the digital realm.
It seems to me that we may be sitting at a similar moment in history to the one that Bush considered. Through the first half of the 20th century, physics was generally lauded and assumed to produce societal goods. Then came the bomb, and the field had a lot of questions to answer about what its purpose was, and what its relationship should be to the military-industrial complex.
And, perhaps I'm reaching here, but networked computing technology has had a similar privileged spot in American life for at least 30 years. Networked computers democratized! Anyone could have a voice! They delivered information, increased the variety of human experience, allowed new capabilities, and helped the world become more open and connected. Computers and the Internet were forces for good in the world, which is why technology was so readily attached to complex, revolutionary processes like the Arab Spring, for example.
But a broad skepticism about technology has crept into (at least) American life. We find ourselves a part of a "war on terror" that is being perpetually, secretly fought across the very network that Engelbart sought to build. Every interaction we have with an Internet service generates a "business record" that can be seized by the NSA through a secretive process that does not require a warrant or an adversarial legal proceeding.
The disclosure of the NSA's surveillance program is not Hiroshima, but it does reveal the latent dark power of the Internet to record communication data at an unprecedented scale, data that can be used by a single nation to detriment of the rest. The narrative of the networked age will never be as simple as it once was.
If you're inclined to see the trails of information Bush imagined future scholars blazing as (meta)data to be hoovered up, if you're inclined to see PRISM as a societal Memex concentrated in the hands of the surveillance state, then perhaps, we're seeing the end of the era Bush's article heralded.
At the very least, those with the lofty goal of improving humanity are going to have to explain why they've chosen networked computing as their augmentation platform of choice, given the costs that we now know explicitly exist. The con side of the ledger can no longer be ignored.
Yet, it seems possible that we have not yet fulfilled the Engelbart's vision. Bush and Engelbart did have distinct visions. For Bush, scientific knowledge itself provided salvation, as if units of wisdom could be manufactured for the preservation of the human race. Engelbart's view was, befitting its time, more cybernetic: people and technology fed one into the other in a spiral of improvement. The Internet is still young, the web younger still. We do not know what form they will take. The current externalities -- now that they are known -- are a new feedback piping into the system, which means they can be accounted for in law or code or both. The co-evolution continues.
And I hope that someone, somewhere heard Engelbart died and found his extensive archive and found her mind aflame with new ideas for how humans, working together, can improve themselves. It's been a rough couple of years for technology, but to quote Bush, "It would seem to be a singularly unfortunate stage at which to terminate the process, or to lose hope as to the outcome."
http://www.theatlantic.com/technology/archive/2013/07/the-hut-where-the-internet-began/277551/?google_editors_picks=trueNO AMNESTY
Don't reward the criminal actions of millions of illegal aliens by giving them citizenship.
Sign in and post comments here.
Please support our fight against illegal immigration by joining ALIPAC's email alerts here https://eepurl.com/cktGTn
-
07-30-2013, 05:48 PM #24
HideIPVPN Review | What Makes HideIPVPN
Mobile Security | How is Smartphone
Best Europe VPN Service | List of Top 10 EU VPN Providers
http://www.bestvpnservice.com/blog/b...vpn-providers/
Mark 3 Comments March, 22, 2011 Best VPN, EU VPN, Europe IP
Rating: 1.0/5 (1 vote cast)
Last Updated
- March, 22, 2011
BestVPNService.com provides you with the best recommendation, developed using customer feedbacks as well as editorial reviews. Same is the case with our recommendation list for best eurpoean vpn service providers. We tested a list of more than 100 VPN providers against same rating criteria, and then rank best vpn providers with respect to their scores.
Let us quickly go through the advantages of using VPN connection in Europe: As you may know, it requires all the ISPs in EU to retain visitors data for approx 6 months, therefore it trashes the concept of anonymity. However, VPN makes your internet connection anonymous therefore, the ISPs cannot detect you. Secondly, you can unblock services like BBC iPlayer, Hulu, Hulu Plus, and other Geo-locked websites that are blocked in EU. Moreover, VPN will protect you against hackers and internet traffic sniffers at hotspots and public Wi-Fi connections, and the list goes on!
know, it requires all the ISPs in EU to retain visitors data for approx 6 months, therefore it trashes the concept of anonymity. However, VPN makes your internet connection anonymous therefore, the ISPs cannot detect you. Secondly, you can unblock services like BBC iPlayer, Hulu, Hulu Plus, and other Geo-locked websites that are blocked in EU. Moreover, VPN will protect you against hackers and internet traffic sniffers at hotspots and public Wi-Fi connections, and the list goes on!
Finally, our list of Best European VPN Service is as follows:
These VPN Providers are ranked in this TOP 10 List because of the number of servers they provide in Europe, quality of customer support, VPN features, protocols offered, experience in the European market and consumer reviews.Rank Provider Starting Price Visit 1 Hidemyass $11.52/month 
2 PureVPN $9.95/month 

3 Private Internet Access $6.45/month 

4 VPN4All $5.95/month 

5 StrongVPN $7/month 

6 IPVanish $10/month 

7 ibVPN $4.96/Month 

8 VPNArea $11.9/month 

9 ExpressVPN $12.95/Month 

10 Overplay VPN $9.95/month 

Visit Bestvpnservice.com, for the list of all VPN Providers.
If you like it, show us your love by following us at Twitter. Click here to follow.
You can also see here the all time Top 10 VPN Provider list.
Wish you a Happy and Private Internet Life !!
Mark
Mark is a Technology and VPN Expert. He is working as an author and asst. editor at Bestvpnservice.com. He is more into giving his views on current news and exploring new technologies in Internet Security arena. He has been enjoying writing not with the pen but with the keyboard at an average speed of 40 words per minute.
3 Responses to Best Europe VPN Service | List of Top 10 EU VPN Providers
-
Hulu VPN says:
May 19, 2011 at 6:13 am
Im watching Hulu daily with the use of VPN services like HideIpVPN, HideMyAss or StrongVPN. They are a little bit pricy but the quality is very good
Reply - Pingback: Freedur VPN Acquired by MocaVPN | Bestvpnservice.com's Blog
- Pingback: Best Dedicated Europe VPN | Bestvpnservice.com Blog
Leave a Reply
Your email address will not be published. Required fields are marked *
Name *
Email *
Website
Comment

All Categories All Categories
Promotion
News
How To
VPN Reviews
 Free VPN For Android | Free Android VPN Apps | Free VPN Android App 3,103 view(s)
Free VPN For Android | Free Android VPN Apps | Free VPN Android App 3,103 view(s) Best Free VPN Service Top 10 Free VPN Services for 2013 2,388 view(s)
Best Free VPN Service Top 10 Free VPN Services for 2013 2,388 view(s) VPN Summer Promotions Enjoy Amazing VPN Discounts! 2,012 view(s)
VPN Summer Promotions Enjoy Amazing VPN Discounts! 2,012 view(s) VPN Setup on iPhone 4 & Older | Top 5 iPhone VPN 1,403 view(s)
VPN Setup on iPhone 4 & Older | Top 5 iPhone VPN 1,403 view(s) Best Free VPN for iPad 1,028 view(s)
Best Free VPN for iPad 1,028 view(s)
Average blog rating
4.4
800 votes cast for 491 posts
Subscribe
Company
Useful Links
- Top 10 List
- Reviews
- Coupons
- Compare
- Tips & Tricks
Follow BestVPNService
Our Network
Copyright Bestvpnservice.com, 2013 - Search, Find & Get The Best VPN Service.
In questions of power let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution. Thomas Jefferson
-
07-30-2013, 08:35 PM #25
Follow:RSSTwitter
University of Wales, Newport: Information Security and Privacy
Aim: To enhance individual privacy and security, using technology as a defender of civil rights

- Home
- What is the thesis about?
- Hacking
- BackTrack
- Brute Force Hacking
- DNS
- KALI
- Man in the Middle Attack
- METASPLOIT
- Mobile Security
- NMAP
- Password Tests
- Routers Port Forwarding
- WIFI
- Wireshark
- News
- Privacy Tools
- Mobile Apps
- Privacy Enhancing Tools (PET's)
- Privacy Tactic
- Search Engine
- Secure Delete
- VPN
- Windows 7 Privacy Tactics
- Security Tools
- Uncategorized
Tags iVPN, Privacy, Surveillance, VPN
Which is the safest VPN on the market? Who do I use for a VPN?
17/05/2013
The reasons that I chose IVPN
www.ivpn.net
1.OpenVPN
IVPN dont promote PPTP they will arm wrestle you onto OpenVPN, with their own installer. OpenVPN was designed to beat Russia and Chinese State surveillance, and is peer reviewed to ensure its safe.
2. Multiple PREMIUM Routes
They use multiple routes. So for the first 10 minutes I can connect to the UK, then for the next 10 minutes, connect via the Netherlands. Then I can get really serious and connect via 2 hops from the UK to the Netherlands and then back to the UK. If a court issued a court order, then theyd need to get court orders in both countries within 10 minutes just about impossible to achieve.
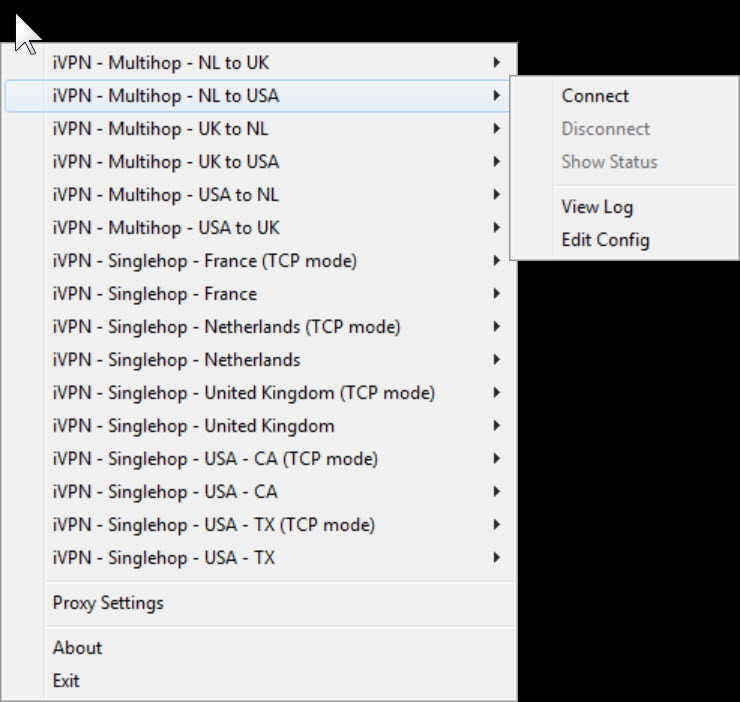
Filesharing may be allowed dependent on the route. Its not allowed on USA routes to protect you. No US lawyer can accuse you of filesharing, as the protocol is rejected. However filesharing is acceptable in many European Countries, so youre allowed to follow the law of the Exit Node.
3. Logs deleted every 10 minutes (not daily as with other VPN providers)
They dont have server logs. They use non persistent or temporary logs which are wiped every 10 minutes. Viola! Evidence gone. This, for me, was the game changer.
4. AES 256 Encryption
They use AES 256 encryption. Most VPNs offer AES 128 bit.
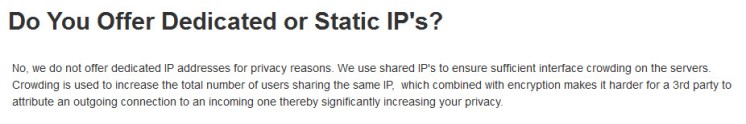
5. Shared IPs
They use Shared IPs. Dedicated IPs are very dangerous for tracking.
6. FAST VPN Speed
7. No Data Retention
They promise to relocate if any country demands data retention or that IVPN must start to keep server logs.
8. EFF Supporter
They are EFF supporters. They are privacy focused, rather than a VPN provider.
9. Setup Guides
Set up guides on how to install IVPN across a range of products. Your one account can be used on a wide range of devices and operating systems.
10. I dont tell you what to do, but I will tell you what I do.
IVPN
www.ivpn.net
Share this:
Like this:
From → Privacy Enhancing Tools (PET's), Privacy Tools, Privacy Tools, Security Tools, Uncategorized, VPN, VPN
6 Comments
-
Justin. permalink
LIked the article but you have not mentioned about different vpn protocols such as L2TP or SSTP. Hence SSTP is the most secure protocol I believe its a must to have if you are windows user. For all other os you may sure use L2TP or OpenVPN. Both Encryption level are the same.
I find followings are the safest vpn on the market supporting SSTP protocol:
- BoxPN : http://www.boxpn.com
- Strongvpn : http://www.strongvpn.com
- Purevpn : http://www.purevpn.com
But there is another case important for privacy which is no log keeping. Almost all vpn services are keeping our activities in log. So do you believe is this really privacy? I also made some research and following are the best vpn services which does NOT LOG any of clients activities:
- BoxPN : http://www.boxpn.com
- Airvpn : http://www.airvpn.com
* Pricing for above vpn services are also great comparing to others.
I hope this information also helps
Reply
-
uwnthesis permalink
Hi Justin,
I agree with your point regarding logs. Server log deletion is critical.
Some VPNs may say that theyre not keeping server logs but they call them something else like traffic logs or connection logs.
I would trust most VPNs have a way to diagnose connection errors and this is what we have to look for as the authorities will if a court order is served on the VPN.
Thats why I selected IVPN as they keep 10 minute connection logs, on the gateways, not the servers, and these logs are in transient memory.. ie RAM not hard drive or server. This transient memory is auto wiped every 10 minutes
So even if the authorities took a server theres nothing there.
I am happy that everyone starts to use VPNs, but decent VPNs not the PPTP nonsense used on Windows 7.
OpenVPN runs on Android, Linux and Windows so once youve learn the menus youre sorted on a cross platform system.
Right, now we tackle the issue of IPSEC/L2.
Ipsec was a committee agreed protocol which like anything decided by a committee is working to the lowest common denominator.
I cannot agree with recommending IPSEC as this is a lowest common denominator standard which ends up pleasing no-one.
So Id stick with OpenVPN:
The reasons are better explained here: - https://uwnthesis.wordpress.com/2012...nvpn-for-vpns/But thanks for your comment.
To anyone reading my advice is to buy into those those who delete your logs fastest which was the basis of my own decision to use IVPN.
Look for:
1. OpenVPN
2. Fast server log deletion (traffic or connection log deletions).
Do not use:
1. A VPN based in your own country (for legal reasons).
2. A VPN that hands over your data without a court order (gives you a chance to defend yourself).
3. A VPN that monitors your surfing and collects that data to sell to advertisers (eg logmein VPN go read the terms if you dont believe me ). A VPN that resells your data is a NO GO area.
Reply
-
Trackbacks & Pingbacks
- Dark Side of the Prism Firefox Add on How to install Dark Side of the Prism | University of Wales, Newport: Information Security and Privacy
- Startpage Email Become a BETA Tester for Startpage | University of Wales, Newport: Information Security and Privacy
- Surveillance revelations pushed people to look for more private ways of going online | University of Wales, Newport: Information Security and Privacy
- Post PRISM: Encrypted communications boom after NSA leaks | University of Wales, Newport: Information Security and Privacy
Leave a Reply
« EU Data Deletion Request Facebook response to the EU
Will giving the internet eyes and ears mean the end of privacy? Bruce Scheiner »
- Top Posts & Pages
- VPNBOOK - Free VPN - How to set up a VPN on Windows 7
- IMMUNICITY - Anti Censorship Tool - unblocks UK Government RESTRICTED sites - In Firefox Browser - for Windows, Linux and Mac OS
- VPNBOOK OpenVPN How to set up OpenVPN on Windows 7
- VPNBook - How to download the Port 53 Certificate (Needs Winzip)
- VPNBOOK - OpenVPN - How to automate your VPN login - user and password
- Paypal terminated my Account because use of a VPN is against their terms and conditions
- KALI - How to unzip files on Linux
- KALI - How to install Flash for Kali Linux - The Visual Guide
- Which is the safest VPN on the market? Who do I use for a VPN?
- How to install Gerix Wifi Cracker on Kali
- Follow Blog via Email
Enter your email address to follow this blog and receive notifications of new posts by email.
Join 65 other followers
- BackTrack Brute Force Hacking Encryption European Privacy Hacking KALI Man in the Middle Attack METASPLOIT Mobile Apps National Security News Password Tests Pervasive Computing Poll Privacy Breach Privacy Enhancing Tools (PET's) Privacy Tactic Privacy Tools Reflection Search Engine Secure Delete Security Tools Surveillance Uncategorized VPN WIFI
Blog at WordPress.com. | The Titan Theme.
Follow Follow University of Wales, Newport: Information Security and Privacy
Get every new post delivered to your Inbox.
Join 65 other followers
Powered by WordPress.comIn questions of power let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution. Thomas Jefferson
-
07-30-2013, 09:07 PM #26NO AMNESTY
Don't reward the criminal actions of millions of illegal aliens by giving them citizenship.
Sign in and post comments here.
Please support our fight against illegal immigration by joining ALIPAC's email alerts here https://eepurl.com/cktGTn
-
08-01-2013, 11:33 AM #27


Security, simplified.
Open Source security for mobile devices.
Get started.


Need some privacy?
Secure your communication with our mobile applications. It's that simple.
Encrypted Communication And Storage
Our projects are focused on creating simple and easy to use tools for secure mobile communication and secure mobile storage.
Open Source Software
The source for all our projects is open, so that anyone can easily verify they work as advertised. They are licensed GPLv3 and will always be free.

Encrypted calls for Android
RedPhone provides end-to-end encryption for your calls, securing your conversations so that nobody can listen in.
- Use the default system dialer and contacts apps to make calls as you normally would.
- RedPhone will give you the opportunity to upgrade to encrypted calls whenever possible.
- RedPhone calls are encrypted end-to-end, but function just like you're used to.
- RedPhone uses your normal phone number to make and receive calls, so you don't need yet another identifier.
Install RedPhone Get RedPhone Source

Secure texts for Android
TextSecure encrypts your text messages over the air and on your phone. It's almost identical to the normal text messaging application, and is just as easy to use.
- A full replacment for the default text messaging application.
- All messages are encrypted locally, so if your phone is lost, your messages will be safe.
- Messages to other TextSecure users are encrypted over the air, protecting your communication in transit.
Install TextSecure Get TextSecure Source

Stay in touch, on Twitter. © 2013 WhisperSystems info@whispersystems.org
In questions of power let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution. Thomas Jefferson
-
08-02-2013, 12:49 PM #28
Far Out Tech
Ubuntu Edge Phone: A Crazy, Cool Idea That's Probably Ahead of Its Time
http://www.entrepreneur.com/article/227649

BY Amy Gahran | August 1, 2013|
0 Comments |
 gadgetmodder.com
gadgetmodder.com
It seems like every other day we read about some far-out, new technology that makes us scratch our heads and say, "What the heck?" In this series, we'll take a look at all types of crazy new gadgets, apps and other technologies -- and the entrepreneurs dreaming them up.
OK, people. It's time to get your mobile geek on. The Ubuntu Edge is a crazy new project for smartphone fanatics.
Wouldn't it be great to have a powerful smartphone that isn't "locked" to any particular carrier, but that could function on any high-speed wireless network? And that could run all your favorite Android apps, but also run a desktop operating system so it could double as a fully functional computer -- just connect it to a monitor and keyboard?
Related
- This New Tool Basically Makes Star Trek Technology a Reality
- Lost Keys? No Problem. This Gadget Can Locate Virtually Anything
- Feel This: Disney Wants to Bring Virtual Objects Into the Real World. Sort Of.
- Forget Necklaces and Rings. This Gold Goes Inside Your Head
0 Comments Share your thoughts
If you think that sounds cool, then you're not alone. The nearly 17,000 people who so far have contributed nearly $8 million to the Ubuntu Edge crowdfunding campaign, which launched July 22, think so, too. Canonical, the company leading the development of the Ubuntu Linux open-source operating system, has set a goal to raise $32 million by Aug. 21. If they achieve this, then people who contributed at least $775 can expect to receive their phone by May of next year.
It's unknown at this point when or whether this phone would become available for general purchase, or how much it might cost.
A crowdfunded, open-technology mobile device like the Ubuntu Edge could be an important step in addressing some current challenges facing the mobile market. For instance, customization. Say you need a mobile phone with special capabilities, such as lots of computing power, a high-end microphone or video card, or the ability to interface with emerging technologies such as mesh networking or innovative mobile devices. Right now, you're out of luck. The mobile handset industry is geared almost entirely to manufacturing products for mass markets -- which constrains mobile innovation.
However, successful crowdfunding could help overcome the considerable financial challenges to bringing specialized mobile devices to market. This could give rise to a mobile hardware market as diverse as the mobile app market has become.
But here's the downside: It's unlikely the Ubuntu Edge will become a reality, just yet. Here are some of the major hurdles this particular project faces:In questions of power let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution. Thomas Jefferson
-
08-02-2013, 12:57 PM #29
MIT Technology Review

Home News & Analysis ▾
Build Your Own Internet with Mobile Mesh Networking
http://www.technologyreview.com/news...sh-networking/
Software can let smartphones, Wi-Fi routers, and other hardware link up without centralized Internet service.
- By Tom Simonite on July 9, 2013
Why It Matters
Centralized communication networks are vulnerable to disruption as well as government control and monitoring.
After an earthquake crippled Haiti in 2010, killing and injuring hundreds of thousands and destroying the country’s communication networks, Paul Gardner-Stephen found himself thinking about all the cell phones that had instantly become useless. With cell towers out of commission across the country, they would be unable to operate. “If the software on the phones was right,” he says, “they would keep working for at least localized communication, handset to handset.”
Gardner-Stephen, a research fellow at Flinders University in Adelaide, Australia, now leads a project that enables Android phones to do just that. Serval, as the project is called, offers an app that allows nearby phones to link up using their Wi-Fi connections, as long as they have been modified to disable the usual security restrictions. Voice calls, text messages, file transfers, and more can take place between devices with the Serval app installed. Devices don’t need to be in range of one another to communicate, as long as there are other devices running the app in between; data can hop between any phones with Serval installed.
This approach, known as mesh networking, is not a new idea (see “Automatic Networks”). But the combination of relatively cheap smartphones and Wi-Fi routers with the progress made by open-source projects such as Serval means that creating and operating such networks is now becoming possible without specialist knowledge.
“We’re trying to dramatically increase the usability and take this out of the geekosphere,” says Sascha Meinrath, the leader of a project called Commotion Wireless, which is developing several software packages that allow people to create mesh networks using low-cost Internet and networking hardware, primarily Wi-Fi routers. The Commotion project is run by the Open Technology Institute, an initiative of the New America Foundation, a nonpartisan think tank in Washington, DC.
Some communities in Washington, Brooklyn, and Detroit already have Wi-Fi-based mesh networks built on Commotion’s technology. The networks offer free Internet access by extending the reach of free connections offered by community centers; they also provide Web services and apps that function only within the local mesh.
After superstorm Sandy cut power to most of Red Hook, Brooklyn, the neighborhood’s mesh network demonstrated how the technology could help recovery after natural disasters. A FEMA-provided satellite Internet link was connected to one part of the Commotion-based network still operating, and a mesh-enabled Wi-Fi router was installed on the roof of an auto body shop that also still had power. That made it possible for many residents and the local aid distribution point to use the slow but badly needed satellite link.
News from the Middle East in recent years—and the U.S. in the past few weeks—has also raised awareness of the potential for mesh networks to create communication networks independent of government oversight. Voice calls and text messages made using phones on a Serval mesh network are strongly encrypted. Gardner-Stephen says that smartphones with Serval installed could enable, say, protesters to keep reaping the benefits of those devices even if cellular networks are shut off.
“You could have someone taking pictures and video at a protest and sharing them immediately to the mesh,” he says. “Even if that person’s phone is seized, the footage has already made it to 10 other phones in the area, and then to hundreds or thousands more.” If one of those people had access to a satellite link, the world would soon know what had happened, he says.
The Commotion project is also working on making its mesh software useful to people, such as political dissidents, for whom conventional connectivity isn’t safe, and the project has received federal grants to support that work. “The State Department and USAID are interested in protecting the free flow of information,” says Meinrath. “You could use a mesh to route around surveillance and censorship.”
To that end, the Commotion team is adapting an encrypted chat program called Cryptocat so it can be used to communicate securely across a local mesh network. Another adaptation aims at making it possible to route communications only through trusted devices on a mesh network, in case an adversary has joined and is collecting traffic. However, Commotion’s security features are far from complete, and the project prominently displays a warning label on its site to indicate its current limitations.
The range of Wi-Fi poses a technical challenge for mesh networks. Tests by the Serval project indicate that for two phones to communicate directly over a Wi-Fi mesh, they need to be within 100 meters of one another with a clear line of sight, or about a room away if they’re linking through buildings.
Serval is currently testing a device called a mesh extender that can help networks based on its technology reach farther. The device uses Wi-Fi to connect tens of nearby Serval devices to a long-range radio link. If extenders are mounted on the roof, links between several of them should be able to stretch kilometers, says Gardner-Stephen. A crowdfunding campaign to support development of a production version of his prototype will launch soon, and the New Zealand Red Cross is helping test the current design.
Most efforts to develop mesh networking are focused on Google’s Android operating system because Apple’s mobile devices are difficult to modify and relatively expensive. Android powers the majority of smartphones worldwide, dominating in the places where poor infrastructure makes mesh networking especially valuable.
However, some mesh proponents say Google is unnecessarily hampering their efforts because it does not support the device-to-device mode of Wi-Fi chips in its Android software (a complaint registered with Google as “Android bug #82”). That means before a device can become an active part of a mesh network, a user must bypass Android’s security controls, or “root” the device, by installing special software. Unrooted devices can use connectivity provided by a mesh network, but they can’t help expand its coverage.
Both the Commotion and Serval projects have tried to get Google to change the policy, to no avail. Gardner-Stephen says Google may believe that smartphone manufacturers and wireless carriers want it to resist. He adds that the company should consider the contribution it could make to disaster response by allowing—if not explicitly promoting—the creation of mesh networks. “Their policy is inhibiting this kind of humanitarian telecommunication,” he says.
13 comments. Share your thoughts »
New & Trending
- Motorola’s Moto X
- Graphics and Games Galore
- Sell Your Own Data
- Gigabit Copper Internet
- Google’s Chromecast Device
- Home Electricity Tracking
- The Wearable Paradox
In questions of power let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution. Thomas Jefferson
-
08-05-2013, 08:02 PM #30
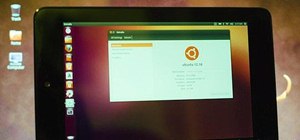
How to Install Ubuntu Linux on Your Google Nexus 7 Android Tablet
http://nexus7.wonderhowto.com/how-to...ablet-0140047/
Posted By
 Nelson Aguilar 6595 9 months ago
Nelson Aguilar 6595 9 months ago
Follow
 13 13 13
13 13 13
Kudos
There's over 20 million people out there who use Ubuntu as their main operating system, and the number is steadily increasing due to its thriving community.
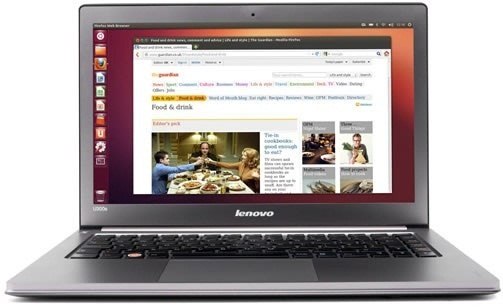
While it's easy enough to download Ubuntu on your PC, the process to get it on your mobile devices can be fairly more difficult. Thankfully, it's not the hard to get Ubuntu onto your Nexus 7 tablet, but first you'll need to unlock it.
How to Unlock Your Nexus 7's Bootloader
If you'd like to install Ubuntu Linux on your Nexus 7, you'll need the Micro-USB cable that came with your Nexus 7, as well as Ubuntu 12.04 LTS or later. For other Ubuntu versions, scroll down to the next section.
Warning: Unlocking the bootloader may void your warranty.
- Make sure you have the Android SDK installed on your system (for ADB and fastboot). You can find the package by searching for android-tools in the Ubuntu Software Center.
- Make sure you have USB Debugging enabled on your Nexus 7.
- Hold the volume down and power button together until you see the Android boot loader UI appear.
- Plug your Nexus 7 into your computer via the Micro-USB cable. Your device will then display the boot loader GUI.
- Verify that fastboot lists the device. In a terminal window, run:
$ sudo fastboot devices
1234567891234567 fastboot
- Start the unlock process:
sudo fastboot oem unlock
- When asked on your Nexus 7 to unlock the bootloader, select Yes.
- Then reboot:
sudo fastboot reboot-bootloader
When your Nexus 7 reboots back into fastboot mode, you should see LOCK STATE - UNLOCKED in small red text. You're not unlocked!
If you're having trouble having your computer talk to your Nexus 7, then you might need to enable permissions. You can find out how to do that here.
How to Install Ubuntu onto Your Unlocked Nexus 7
For this, you'll need the Ubuntu Nexus 7 Desktop Installer, which you can grab via a PPA:
sudo add-apt-repository ppa:ubuntu-nexus7/ubuntu-nexus7-installer
sudo apt-get update
sudo apt-get install ubuntu-nexus7-installer
Once it's installed, make sure your Nexus 7 is connected to your computer and ensure it is in fastboot mode. Make sure your Nexus 7 is the only device plugged in!
Now just find the installer on the dash (just search for "nexus") and open it. It will download the latest image automatically and flash it to your Nexus 7. After a couple of minutes, your device will reboot and finish the Ubuntu installation, which should take about 10-15 minutes.
For troubleshooting tips and info on how to return your Nexus 7 back to the stock Android system, visit the complete instructions by Canonical over on the Ubuntu Wiki.
Installing Earlier Versions of Ubuntu on Your Nexus 7
If you have any versions of Ubuntu below 12.0, don't fret, because the video below shows you how to install any older versions on your Nexus 7. You'll just have to unlock your device following the instructions above, then install the files manually.
You can also read the entire step-by-step process over on Nexus 7 Root.
Cover image by AndroidCentral
See Also
In questions of power let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution. Thomas Jefferson


 1Likes
1Likes LinkBack URL
LinkBack URL About LinkBacks
About LinkBacks




 Reply With Quote
Reply With Quote
 How to Install Ubuntu Linux on a Nexus One or HTC Evo phone
How to Install Ubuntu Linux on a Nexus One or HTC Evo phone  How to Install Ubuntu on your Samsung Galaxy Tab 10.1 Android tablet
How to Install Ubuntu on your Samsung Galaxy Tab 10.1 Android tablet  How to Find Only the Best Tablet-Specific Apps for Your Nexus 7
How to Find Only the Best Tablet-Specific Apps for Your Nexus 7 

The Food is No Good at All African Illegals at NYC City...
04-17-2024, 09:12 PM in illegal immigration News Stories & Reports