Results 391 to 400 of 582
Thread Information
Users Browsing this Thread
There are currently 1 users browsing this thread. (0 members and 1 guests)
-
10-06-2013, 06:19 PM #391AprilGuest
NSA and GCHQ target Tor network that protects anonymity of web users
• Top-secret documents detail repeated efforts to crack Tor
• US-funded tool relied upon by dissidents and activists
• Core security of network remains intact but NSA has some success attacking users' computers
• Bruce Schneier: the NSA's attacks must be made public
• Attacking Tor: the technical details
• 'Peeling back the layers with Egotistical Giraffe' – document
• 'Tor Stinks' presentation – full document
• Tor: 'The king of high-secure, low-latency anonymity'
 One technique developed by the agency targeted the Firefox web browser used with Tor, giving the agency full control over targets' computers. Photograph: Felix Clay
One technique developed by the agency targeted the Firefox web browser used with Tor, giving the agency full control over targets' computers. Photograph: Felix Clay
The National Security Agency has made repeated attempts to develop attacks against people using Tor, a popular tool designed to protect online anonymity, despite the fact the software is primarily funded and promoted by the US government itself.
Top-secret NSA documents, disclosed by whistleblower Edward Snowden, reveal that the agency's current successes against Tor rely on identifying users and then attacking vulnerable software on their computers. One technique developed by the agency targeted the Firefox web browser used with Tor, giving the agency full control over targets' computers, including access to files, all keystrokes and all online activity.
But the documents suggest that the fundamental security of the Tor service remains intact. One top-secret presentation, titled 'Tor Stinks', states: "We will never be able to de-anonymize all Tor users all the time." It continues: "With manual analysis we can de-anonymize a very small fraction of Tor users," and says the agency has had "no success de-anonymizing a user in response" to a specific request.
Another top-secret presentation calls Tor "the king of high-secure, low-latency internet anonymity".
Tor – which stands for The Onion Router – is an open-source public project that bounces its users' internet traffic through several other computers, which it calls "relays" or "nodes", to keep it anonymous and avoid online censorship tools.
It is relied upon by journalists, activists and campaigners in the US and Europe as well as in China, Iran and Syria, to maintain the privacy of their communications and avoid reprisals from government. To this end, it receives around 60% of its funding from the US government, primarily the State Department and the Department of Defense – which houses the NSA.
Despite Tor's importance to dissidents and human rights organizations, however, the NSA and its UK counterpart GCHQ have devoted considerable efforts to attacking the service, which law enforcement agencies say is also used by people engaged in terrorism, the trade of child abuse images, and online drug dealing.
Privacy and human rights groups have been concerned about the security of Tor following revelations in the Guardian, New York Times and ProPublica about widespread NSA efforts to undermine privacy and security software. A report by Brazilian newspaper Globo also contained hints that the agencies had capabilities against the network.
While it seems that the NSA has not compromised the core security of the Tor software or network, the documents detail proof-of-concept attacks, including several relying on the large-scale online surveillance systems maintained by the NSA and GCHQ through internet cable taps.
One such technique is based on trying to spot patterns in the signals entering and leaving the Tor network, to try to de-anonymise its users. The effort was based on a long-discussed theoretical weakness of the network: that if one agency controlled a large number of the "exits" from the Tor network, they could identify a large amount of the traffic passing through it.
The proof-of-concept attack demonstrated in the documents would rely on the NSA's cable-tapping operation, and the agency secretly operating computers, or 'nodes', in the Tor system. However, one presentation stated that the success of this technique was "negligible" because the NSA has "access to very few nodes" and that it is "difficult to combine meaningfully with passive Sigint".
While the documents confirm the NSA does indeed operate and collect traffic from some nodes in the Tor network, they contain no detail as to how many, and there are no indications that the proposed de-anonymization technique was ever implemented.
Other efforts mounted by the agencies include attempting to direct traffic toward NSA-operated servers, or attacking other software used by Tor users. One presentation, titled 'Tor: Overview of Existing Techniques', also refers to making efforts to "shape", or influence, the future development of Tor, in conjunction with GCHQ.
Another effort involves measuring the timings of messages going in and out of the network to try to identify users. A third attempts to degrade or disrupt the Tor service, forcing users to abandon the anonymity protection.
Such efforts to target or undermine Tor are likely to raise legal and policy concerns for the intelligence agencies.
Foremost among those concerns is whether the NSA has acted, deliberately or inadvertently, against internet users in the US when attacking Tor. One of the functions of the anonymity service is to hide the country of all of its users, meaning any attack could be hitting members of Tor's substantial US user base.
Several attacks result in implanting malicious code on the computer of Tor users who visit particular websites. The agencies say they are targeting terrorists or organized criminals visiting particular discussion boards, but these attacks could also hit journalists, researchers, or those who accidentally stumble upon a targeted site.
The efforts could also raise concerns in the State Department and other US government agencies that provide funding to increase Tor's security – as part of the Obama administration's internet freedom agenda to help citizens of repressive regimes – circumvent online restrictions.
Material published online for a discussion event held by the State Department, for example, described the importance of tools such as Tor.
"[T]he technologies of internet repression, monitoring and control continue to advance and spread as the tools that oppressive governments use to restrict internet access and to track citizen online activities grow more sophisticated. Sophisticated, secure, and scalable technologies are needed to continue to advance internet freedom."
The Broadcasting Board of Governors, a federal agency whose mission is to "inform, engage, and connect people around the world in support of freedom and democracy" through networks such as Voice of America, also supported Tor's development until October 2012 to ensure that people in countries such as Iran and China could access BBG content. Tor continues to receive federal funds through Radio Free Asia, which is funded by a federal grant from BBG.
The governments of both these countries have attempted to curtail Tor's use: China has tried on multiple occasions to block Tor entirely, while one of the motives behind Iranian efforts to create a "national internet" entirely under government control was to prevent circumvention of those controls.
The NSA's own documents acknowledge the service's wide use in countries where the internet is routinely surveilled or censored. One presentation notes that among uses of Tor for "general privacy" and "non-attribution", it can be used for "circumvention of nation state internet policies" – and is used by "dissidents" in "Iran, China, etc".
Yet GCHQ documents show a disparaging attitude towards Tor users. One presentation acknowledges Tor was "created by the US government" and is "now maintained by the Electronic Frontier Foundation (EFF)", a US freedom of expression group. In reality, Tor is maintained by an independent foundation, though has in the past received funding from the EFF.
The presentation continues by noting that "EFF will tell you there are many pseudo-legitimate uses for Tor", but says "we're interested as bad people use Tor". Another presentation remarks: "Very naughty people use Tor".
The technique developed by the NSA to attack Tor users through vulnerable software on their computers has the codename EgotisticalGiraffe, the documents show. It involves exploiting the Tor browser bundle, a collection of programs, designed to make it easy for people to install and use the software. Among these is a version of the Firefox web browser.
The trick, detailed in a top-secret presentation titled 'Peeling back the layers of Tor with EgotisticalGiraffe', identified website visitors who were using the protective software and only executed its attack – which took advantage of vulnerabilities in an older version of Firefox – against those people. Under this approach, the NSA does not attack the Tor system directly. Rather, targets are identified as Tor users and then the NSA attacks their browsers.
According to the documents provided by Snowden, the particular vulnerabilities used in this type of attack were inadvertently fixed by Mozilla Corporation in Firefox 17, released in November 2012 – a fix the NSA had not circumvented by January 2013 when the documents were written.
The older exploits would, however, still be usable against many Tor users who had not kept their software up to date.
A similar but less complex exploit against the Tor network was revealed by security researchers in July this year. Details of the exploit, including its purpose and which servers it passed on victims' details to, led to speculation it had been built by the FBI or another US agency.
At the time, the FBI refused to comment on whether it was behind the attack, but subsequently admitted in a hearing in an Irish court that it had operated the malware to target an alleged host of images of child abuse – though the attack did also hit numerous unconnected services on the Tor network.
Roger Dingledine, the president of the Tor project, said the NSA's efforts serve as a reminder that using Tor on its own is not sufficient to guarantee anonymity against intelligence agencies – but showed it was also a great aid in combating mass surveillance.
"The good news is that they went for a browser exploit, meaning there's no indication they can break the Tor protocol or do traffic analysis on the Tor network," Dingledine said. "Infecting the laptop, phone, or desktop is still the easiest way to learn about the human behind the keyboard.
http://www.theguardian.com/world/201...ork-encryption
-
10-09-2013, 02:57 AM #392Senior Member


- Join Date
- May 2007
- Location
- South West Florida (Behind friendly lines but still in Occupied Territory)
- Posts
- 117,088
EFF Provides An In-Depth Look At How The NSA Deploys Malware
October 8, 2013 by Electronic Frontier Foundation
This article, written by staff technologist Dan Auerbach, was originally published by the Electronic Frontier Foundation on Oct. 8.
We’ve long suspected that the NSA, the world’s premiere spy agency, was pretty good at breaking into computers. But now, thanks to an article by security expert Bruce Schneier—who is working with the Guardian to go through the Snowden documents—we have a much more detailed view of how the NSA uses exploits in order to infect the computers of targeted users. The template for attacking people with malware used by the NSA is in widespread use by criminals and fraudsters, as well as foreign intelligence agencies, so it’s important to understand and defend against this threat to avoid being a victim to the plethora of attackers out there.
How Does Malware Work Exactly?
Deploying malware over the web generally involves two steps. First, as an attacker, you have to get your victim to visit a website under your control. Second, you have to get software—known as malware—installed on the victim’s computer in order to gain control of that machine. This formula isn’t universal, but is often how web-based malware attacks proceed.
In order to accomplish the first step of getting a user to visit a site under your control, an attacker might email the victim text that contains a link to the website in question, in a so-called phishing attack. The NSA reportedly uses phishing attacks sometimes, but we’ve learned that this step usually proceeds via a so-called “man-in-the-middle” attack.1 The NSA controls a set of servers codenamed “Quantum” that sit on the Internet backbone, and these servers are used to redirect targets away from their intended destinations to still other NSA-controlled servers that are responsible for the injection of malware. So, for example, if a targeted user visits “yahoo.com”, the target’s browser will display the ordinary Yahoo! landing page but will actually be communicating with a server controlled by the NSA. This malicious version of Yahoo!’s website will tell the victim’s browser to make a request in a background to another server controlled by the NSA which is used to deploy malware.
Once a victim visits a malicious website, how does the attacker actually infect the computer? Perhaps the most straightforward method is to trick the user into downloading and running software. A cleverly designed pop-up advertisement may convince a user to download and install the attacker’s malware, for example.
But this method does not always work, and relies on a user taking action to download and run software. Instead, attackers can exploit software vulnerabilities in the browser that the victim is using in order to gain access to her computer. When a victim’s browser loads a website, the software has to perform tasks like parsing text given to it by the server, and will often load browser plugins like Flash that run code given to it by the server, in addition to executing Javascript code given to it by the server. But browser software—which is becoming increasingly complex as the web gains more functionality—doesn’t work perfectly. Like all software, it has bugs, and sometimes those bugs are exploitable security vulnerabilities that allow an attacker to gain access to a victim’s computer just because a particular website was visited. Once browser vendors discover vulnerabilities, they are generally patched, but sometimes a user has out of date software that is still vulnerable to known attack. Other times, the vulnerabilities are known only to the attacker and not to the browser vendor; these are called zero-day vulnerabilities.
The NSA has a set of servers on the public Internet with the code name “FoxAcid” used to deploy malware. Once their Quantum servers redirect targets to a specially crafted URL hosted on a FoxAcid server, software on that FoxAcid server selects from a toolkit of exploits in order to gain access to the user’s computer. Presumably this toolkit has both known public exploits that rely on a user’s software being out of date, as well as zero-day exploits which are generally saved for high value targets.2 The agency then reportedly uses this initial malware to install longer lasting malware.
Once an attacker has successfully infected a victim with malware, the attacker generally has full access to the user’s machines: she can record key strokes (which will reveal passwords and other sensitive information), turn on a web cam, or read any data on the victim’s computer.
What Can Users Do To Protect Themselves?
We hope that these revelations spur browser vendors to action, both to harden their systems against exploits, and to attempt to detect and block the malware URLs used by the FoxAcid servers.
In the meantime, users concerned about their security should practice good security hygiene. Always keep your software up to date—especially browser plugins like Flash that require manual updates. Make sure you can distinguish between legitimate updates and pop-up ads that masquerade as software updates. Never click a suspicious looking link in an email.
For users who want to go an extra step towards being more secure—and we think everyone should be in this camp—consider making plugins like Flash and Java “click-to-play” so that they are not executed on any given web page until you affirmatively click them. For Chromium and Chrome, this option is available in Settings => Show Advanced Settings => Privacy => Content Settings => Plug-ins. For Firefox, this functionality is available by installing a browser Add-On like “Click to Play per-element”. Plugins can also be uninstalled or turned off completely. Users should also use ad blocking software to stop unnecessary web requests to third party advertisers and web trackers, and our HTTPS Everywhere add-on in order to encrypt connections to websites with HTTPS as much as possible.
Finally, for users who are willing to notice some more pain when browsing the web, consider using an add-on like NotScripts (Chrome) or NoScript (Firefox) to limit the execution of scripts. This means you will have to click to allow scripts to run, and since Javascript is very prevalent, you will have to click a lot. For Firefox users, RequestPolicy is another useful add-on that stops third-party resources from loading on a page by default. Once again, as third-party resources are popular, this will disrupt ordinary browsing a fair amount. Finally, for the ultra paranoid, HTTP Nowhere will disable all HTTP traffic completely, forcing your browsing experience to be entirely encrypted, and making it so that only websites that offer an HTTPS connection are available to browse.
Conclusion
The NSA’s system for deploying malware isn’t particularly novel, but getting some insight into how it works should help users and browser and software vendors better defend against these types of attacks, making us all safer against criminals, foreign intelligence agencies, and a host of attackers. That’s why we think it’s critical that the NSA come clean about its capabilities and where the common security holes are—our online security depends on it.
1. The term “man-in-the-middle” is sometimes reserved for attacks on cryptographically secure connections, for example using a fraudulent SSL certificate. In this context, however, we mean it more generally to mean any attack where the attacker sits between the victim and the intended website.
2. According to the Guardian article, “the most valuable exploits are saved for the most important targets.”
Filed Under: Liberty News, Privacy, Staff Reports
http://personalliberty.com/2013/10/0...ploys-malware/Join our efforts to Secure America's Borders and End Illegal Immigration by Joining ALIPAC's E-Mail Alerts network (CLICK HERE)
-
10-09-2013, 11:25 PM #393AprilGuest
NSA reforms threatened by 'business-as-usual brigade', Ron Wyden warns
Oregon senator and vocal critic of NSA says senior intelligence officials will try to make sure any change is merely 'skin deep'

Ron Wyden told the Cato Institute: 'Privacy protections that don’t actually protect privacy are not worth the paper they're printed on.' Photograph: Win McNamee/Getty
The Democratic senator leading congressional efforts to rein in the National Security Agency warned on Wednesday that senior intelligence and administration officials will attempt to block any meaningful change while publicly speaking the language of reform.
Ron Wyden, a member of the Senate intelligence committee, told a conference on the NSA and privacy at the Cato Institute in Washington that the reform campaign was at a pivotal moment, with the Senate and the House of Representatives to examine new surveillance legislation over the next few weeks.
But, Wyden said, the American public should not be fooled by what he called the “business-as-usual brigade” – made up of intelligence officials, their supporters in Congress, thinktanks and the media.
They will “try mightily to fog up the surveillance debate and convince Congress and the public that the real problem here is not overly intrusive, constitutionally flawed domestic surveillance, but sensationalistic media reporting”, Wyden said. “Their endgame is ensuring that any surveillance reforms are only skin deep.”
The Oregon senator is a part of a bipartisan Senate group who unveiled the first comprehensive surveillance reform bill two weeks ago. It would end the NSA’s bulk collection of phone records, first revealed by the Guardian in June, change the secret court that oversees the agency’s foreign intelligence programs and close the loophole that allows analysts to review Americans’ communications without a warrant.
Wyden said he expected a tough legislative battle against the “defenders of the status quo”, whose arguments, he said, had an “Alice in Wonderland flavour” that left the public with a distorted view of the NSA’s activities and the effectiveness of oversight.
"Privacy protections that don’t actually protect privacy are not worth the paper they're printed on,” he said. “And just because intelligence officials say that a particular program helps catch terrorists doesn’t make it true.”
He was also sceptical about the Obama administration’s professed commitment to greater transparency. “When it comes to greater transparency and openness, the executive branch has shown little interest in lasting reforms that would actually make the intelligence community more open and transparent, and executive branch officials will probably resist any attempts to mandate greater transparency,” he said.
Wyden was scathing about the government’s “trust us” argument on surveillance, which he said was undermined by the NSA’s own track record. “The rules have been broken, and the rules have been broken a lot,” he said.
As a result, Wyden said, it would be a mistake for Congress to enshrine these measures in law. As well as giving the domestic surveillance programs a stamp of approval, it would also pave the way for other types of private data – such as medical and firearms records – to be collected in bulk. “Codifying the bulk collection program into law and ushering in a new era of digital surveillance would normalize over-broad authorities that were once unthinkable in America,” he said.
The NSA’s programs were also undermining public trust in the major US technology companies that have been subject to surveillance orders, Wyden said. “If they start to lose ground to foreign competition it will put tens of thousands of high-paying jobs at serious risk. If a foreign enemy were doing this much damage to our economy, people would be out in the street with pitchforks.”
Another speaker at the Cato event, Michigan congressman Justin Amash, said the director of national intelligence James Clapper should face criminal charges for lying to Congress.
"Director Clapper very clearly lied to Congress," said Amash following his speech. "He should be prosecuted for lying."
Amash continued: “We can't have those kinds of actions in Congress and find them acceptable."
Clapper has come under heavy criticism for a March statement to the Senate intelligence committee that the NSA does "not wittingly" collect information on millions of Americans – a claim directly contradicted by whistleblower Edward Snowden's revelations about mass phone records collection by the NSA.
Railing against what he considered undue deference to the Obama administration and intelligence agencies, Amash lambasted his colleagues on the secret intelligence committees as "enemies of Congress".
"Time and again, the intelligence committees have not been the friends of Congress – they have been the enemies of Congress," Amash said, accusing the committee members of "covering up for the administration".
His fellow Michigan Republican, Mike Rogers – who has strongly defended the NSA's bulk surveillance and opposed Amash's July effort to defund it – chairs the House intelligence committee.
Amash described secretive closed-door briefings for legislators on secret surveillance programs as providing "no real information" to the members of Congress that have to vote on surveillance laws.
"There's no real information provided," Amash said. "You don't know what questions to ask. You have to just start spitting out random questions. Does the government have a moon base? Does the government have a talking bear? Does the government have a cyborg army?"
http://www.theguardian.com/world/201...orms-ron-wyden
-
10-10-2013, 06:26 AM #394Senior Member


- Join Date
- May 2007
- Location
- South West Florida (Behind friendly lines but still in Occupied Territory)
- Posts
- 117,088
Class Action Lawsuits Filed Against Obama/NSA For Violations of Constitution
Dear Patriot:
Thank you for your continued support of WND.com.
Please take a few moments to consider this message from a friend of WND, whom we believe is engaged in a worthy cause.
Thank you again, from the team at WND.com!
 We the People have recently learned that the President Barack Obama is using his National Security Agency to spy on us, by intercepting our private and confidential telephone messages, emails and internet postings to use against us. In this way it can obviously coerce and blackmail the American people to remain silent to his power grab, which is intended to transform our beloved nation into his dream of a socialist state.
We the People have recently learned that the President Barack Obama is using his National Security Agency to spy on us, by intercepting our private and confidential telephone messages, emails and internet postings to use against us. In this way it can obviously coerce and blackmail the American people to remain silent to his power grab, which is intended to transform our beloved nation into his dream of a socialist state.
I'm looking for millions of Americans to stand together and join with us in the class action lawsuits we have already filed in federal court in Washington, D.C. against the Obama adminisration, its corporate enablers and the judge who went along with their power grab, in order to take back our constitutionally protected rights of privacy, freedom of association and the right to be free from unreasonable searches and seizures of our most private personal communications and due process. Without millions of American citizens fighting for freedom, we fear that our great country will be totally destroyed if President Obama is allowed to continue spying on all of our telephone calls, email and internet postings. PLEASE READ THIS CAREFULLY AS OUR CLASS ACTION CASES HAVE ALREADY BEEN FILED AND ARE IN PROGRESS AND WE NEED YOU TO JOIN IN THE FIGHT TO PRESERVE OUR FREEDOMS BEFORE ALL IS LOST!
Please help us win this class action suit by donating here.
These class action lawsuits were filed because Barack Hussein Obama's National Security Agency (NSA) is looking through billions of our emails, phone records, and other personal and confidential information to coerce and blackmail the American people to remain silent to his tyranny and attempted dismantling of the foundations of our Republic.
This outrage is more than simply the latest scandal in Washington. It marks a critical turning point in our nation, and I am counting on you to support us in our efforts to regain our rights as American citizens; rights which our Founding Fathers and the American colonies fought and died for.
 This is an absolutely critical and defining moment. Already filed class action lawsuits against President Obama, his Attorney General Eric Holder, the NSA, Verizon, and other cell phone and internet provider companies like Facebook, Google, Yahoo, and AOL, will serve to unify all political and social persuasions in our great nation to wage a second American revolution, one that is peaceful and legal - but pursued with force. The time has come for We the People to rise up and reclaim control of our nation. The American people can use these class actions to 'man the barricades of freedom' against President Obama and his establishment government despots and their corporate enablers who seek to imprison them through coercive abuses o f their privacy and other constitutional rights. We must say 'no' to the Orwellian power grab. We must demand that our liberties be respected, before we are all made the prisoners of Obama and his comrades.
This is an absolutely critical and defining moment. Already filed class action lawsuits against President Obama, his Attorney General Eric Holder, the NSA, Verizon, and other cell phone and internet provider companies like Facebook, Google, Yahoo, and AOL, will serve to unify all political and social persuasions in our great nation to wage a second American revolution, one that is peaceful and legal - but pursued with force. The time has come for We the People to rise up and reclaim control of our nation. The American people can use these class actions to 'man the barricades of freedom' against President Obama and his establishment government despots and their corporate enablers who seek to imprison them through coercive abuses o f their privacy and other constitutional rights. We must say 'no' to the Orwellian power grab. We must demand that our liberties be respected, before we are all made the prisoners of Obama and his comrades.
Without your strong financial support, however, this could be the moment that Americans give up their God given rights to freedom, ran away from a fight and gave up our last bit of approval for a government-takeover of our lives. To keep us down and to prevent us from fighting back, Obama and his comrades are spying on all of us. They are obviously prepared to use confidential personal information to coerce and blackmail we, the American people, into submission in order that he can pursue his agenda to transform the nation into a socialist state. This simply cannot be permitted and we must not stand for this, but rather stand and fight together to prevent this. As our Founding Father Benjamin Franklin declared in the days leading up to the Declaration of Independence, either we must all hang together or separately we will be hanged.
The class action cases which we have filed are a way for us all to hang together to defeat Obama and his socialist comrades.
To view the class action complaints, join our just cause and make generous gift to our legal defense fund, go here. We the People are up against powerful forces and we must have the financial means to legally wage this battle; a second American revolution to reclaim and preserve our liberties. Let us all band together to wage a second American revolution, legally and in the courts, to preserve our God given freedoms and liberties. Time is short before all is lost.
If you can, please agree to your most generous contribution of $500, $250, $100, $50 or $35 today. Every dollar counts. With your support, we will immediately begin mobilizing millions of freedom loving Americans from all over the country to join our already filed lawsuits stop Obama’s spying on us and to preserve our freedoms! While others just talk, we have taken action to put an end to this illegal attempt by President Obama to take away our constitutional rights and to take total control over the lives of me, you and our loved ones.
 Thanks so much for your support. Time is short to save the nation from President Obama’s totalitarian takeover! Help us NOW to wage this legal revolution to save the nation before all is lost!
Thanks so much for your support. Time is short to save the nation from President Obama’s totalitarian takeover! Help us NOW to wage this legal revolution to save the nation before all is lost!
Please consider donating. Anything will help.
Sincerely,
Larry Klayman
Mr. Klayman was the legal counsel who successfully
defeated the legal recall of Sheriff Joe ArpaioJoin our efforts to Secure America's Borders and End Illegal Immigration by Joining ALIPAC's E-Mail Alerts network (CLICK HERE)
-
10-10-2013, 09:56 PM #395AprilGuest
Good to see!
-
10-11-2013, 07:39 PM #396Senior Member


- Join Date
- May 2007
- Location
- South West Florida (Behind friendly lines but still in Occupied Territory)
- Posts
- 117,088
WND EXCLUSIVEThink Obamacare website's a mess? Check this out
As a taxpayer, you've helped pay the $1.4 billion price tag for this digital lemon.
Hundreds of thousands of dollars worth of sensitive computers used to store vast amounts of data have been lost due to "fiery explosions, melted metal and broken circuits."
Delays, promised fixes, uncertainty ... the end is not in sight.
NSA data bank hit by mystery power surges
Experts warn loss to fires similar to what would happen in EMP strike
Published: 23 hours ago

WASHINGTON – The new $1.4 billion National Security Agency supercomputer facility in Utah has been wracked with unexplainable, repeated electrical surges and explosions that have destroyed hundreds of thousands of dollars worth of sensitive computers used to store the vast amounts of data it scoops up on foreign nationals and Americans.
In the past 13 months, there have been some 10 electrical meltdowns at the new 200-acre facility in Bluffdale, Utah, which has been unable to run all of its computers and servers.
The cooling operations apparently fail, resulting in the meltdowns.
But the failures for such a project are not ordinary. They have been described as “a flash of lightning inside a two-foot box,” one source said.
The failures have been described as fiery explosions, melted metal and broken circuits. While efforts are under way to fix the problems, there is no assurance at this point that the fixes will be sufficient, experts believe.
But the experts warn that the meltdowns and loss of data could be replicated many times over across the U.S. should the nation be hit by an electromagnetic pulse, or EMP, blast.
Maine state Rep. Andrea Boland said data centers and other critical components providing services to businesses and homes would be targets.
She introduced legislation in the Maine legislature that eventually was passed and signed into law for the state to begin protecting its electrical grid system from an EMP event.
“What ‘destroyed hundreds of thousands of dollars’ worth of machinery and delayed the center’s opening for a year’ is what would be delivered to us by a severe solar storm (100 percent probability) or man-made electromagnetic pulse (EMP), because, as in Utah, NERC and utility owners have ‘bypassed regular quality controls in design and construction,’ and left us the most vulnerable country in the world,” Boland said.

Read the documentation that’s sparking the worry about the EMP threat, in “A Nation Forsaken.”
“They know it, enemies know it, Congress knows it,” she said. “Maine is doing something about it.”
Boland’s reference to the NERC is the North American Electric Reliability Corporation. It oversees bulk power systems throughout the U.S.
However, NERC has opposed measures to harden the electrical grid and local utilities, prompting states such as Maine to begin to take action on their own. The federal government has been unresponsive to taking the initiative to harden facilities nationwide.
The opening of the new NSA data storage center has been delayed for another year while experts attempt to find the source of the power flashes.
The contractor that designed the data center’s system is the Pennsylvania-based Klingstubbins. While the firm claims to have “uncovered the issue” and are now “implementing a permanent fix,” the U.S. Army Corps of Engineers, which is overseeing the construction of the data center, said not so fast.
The Army Corps said that the meltdowns are “not sufficiently understood.”
An ACE report said that there is insufficient information on the design of the electrical system that could create new issues in changing circuit breaker settings. The report added that normal quality controls in design and construction had been bypassed to “fast track” construction.
The Utah data center is just one of a number of new NSA data centers being created across the nation to collect data under NSA’s massive surveillance program. The program was exposed earlier this year by former NSA contractor Edward Snowden, who has sought asylum in Russia.
The project requires a 65-megawatt center with a chiller plant, fire suppression systems, electrical generators and an uninterruptible power supply backup capacity.
Sixty-five megawatts of energy is enough to power a city of more than 20,000 people. Once in operation, it will be able to store exabytes or even zettabytes of data. A zettabyte is 100 million times larger than all the printed material in the Library of Congress.
Norbert Suter, ACE’s chief of construction operations, said that “final commissioning of the entire electrical system is still ongoing.”
“The corps is ensuring it functions as required and that it will be completely reliable prior to releasing the project to the customer,” in this case, NSA, he said.
Yet, Suter couldn’t say when the site would be turned over to NSA.
“During the testing and commissioning of the Utah data center, problems were discovered with certain parts of the electrical system,” Suter said. “Issues such as these can arise in any project, and are the reason the corps tests and reviews every aspect of any project prior to releasing it to the customer.”
Suter said that the cause of the electrical problems had been identified and that a team is currently working on it.
The team also had determined that there were ventilation problems. Such massive data centers require air management systems capable of cooling sensitive equipment to remove heat that is generated from their operation.
“An airflow issue was discovered with the generators and the contractor is correcting the problem,” Suter said.
However, he was unsure as to when the problems will be corrected.
http://www.wnd.com/2013/10/nsa-data-...-power-surges/Join our efforts to Secure America's Borders and End Illegal Immigration by Joining ALIPAC's E-Mail Alerts network (CLICK HERE)
-
10-12-2013, 09:40 AM #397
Google will soon put your face, name, and content in its ads
http://arstechnica.com/business/2013...nt-in-its-ads/
Your name is ____, and you endorse this Google message. Right?
by Casey Johnston - Oct 11 2013, 12:33pm EDT
157
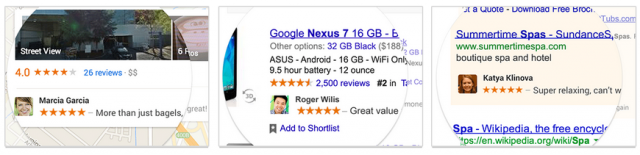 A sampling of what Google's shared endorsements will look like.
A sampling of what Google's shared endorsements will look like.
If you always wanted to see your shining face next to Google ads, your wish will soon be granted. Today Google announced plans to roll out “shared endorsements,” which will augment its own advertisements with information from users who rated, reviewed, or gave a +1 to the service or location in question.
The move echoes Facebook’s “sponsored stories,” where the social network started turning users’ likes or check-ins into ads on its site, all without asking permission or even notifying them. A public outcry, class-action lawsuit, $20 million settlement, and limitations on the use of users’ content followed.
Google revealed its shared endorsements scheme in a change to its terms of service. The updates state that going forward, friends, family, “and others” may see a user’s Google profile name, photo, and any endorsement they’ve created for a company alongside ads for that company. For instance, if Jon Brodkin gave the new Nickelback album 5 stars and said in a review that the band is “the voice of our generation,” the next time someone searches for that album, Brodkin’s rating and praise could appear alongside a sponsored placement.
Google specifies that the privacy scope of the content you share will affect how it is used in an endorsement. If Brodkin shares that favorable Nickelback review to only his Google+ circle of Friends, only they will see it. If he shares it publicly, which is the default sharing setting on Google content, anyone will see it.
Users are opted in to Google's new scheme by default. In the past, Google gave itself permission to use users’ +1s alongside advertisements unless the user specifically opted out. The new “shared endorsements” are an extension of that setting, wherein Google gives itself permission to take even more of a user’s content and place it alongside ads.
To opt out of being a shared endorsement, Google users must go to the “shared endorsement” settings page, which is currently not linked anywhere from either their Google+ account or privacy settings (the ads have yet to go into effect, so Google may be waiting to integrate the page until the feature is live). At the bottom of the page is a checkbox next to the phrase “Based upon my activity, Google may show my name and profile photo in shared endorsements that appear in ads.”
If a user previously opted out of Google using their +1s in ads, this box will appear unchecked. For anyone else, it will be checked by default.
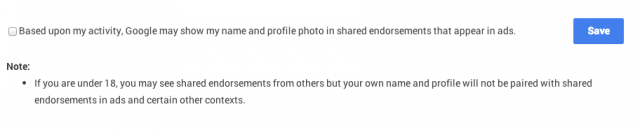 Enlarge / The opt-out checkbox, located here.
Enlarge / The opt-out checkbox, located here.
As the New York Times pointed out, Google would not specify whether advertisers will choose to have shared endorsements on their ads or not.
The handful of Google users’ reactions on Google’s profile on relevant posts range from neutral (because of the opt-out) to disappointed or indignant. “Very Facebookesque. Puts you off reviewing anything,” said Michael Sharp.
“Does the user get a cut of the ad value? ” said Matt Paonessa.
“For those disliking the idea of your reviews going (more) public, answer me, why else are you making reviews?” asked Petr Faitl.
Google is going about including its users in advertising in a slightly better way than Facebook did, making a semi-public announcement and providing a way to opt out. The real problem is that the majority of users simply don’t pay attention to these sorts of things.
Google is able to put changes to its services front and center if it chooses. It did so with the massive overhaul of its terms of service and privacy policy back in January 2012 by placing an alert both under the search box on its homepage and on search results pages. This shared endorsements change flies a bit further under the radar.
If you're uncomfortable with the idea of your content being used in advertisements, even if it’s just certain types—no one has time to go back through their profile and groom out posts set to public that weren’t expected to be used in ads—there is a window of opportunity to avoid it altogether. Google has already opened the opt-out page and will not roll out shared endorsements until November 11.
Update: Google has added a link to the terms of service changes on its home page, though not on the Google+ main page.
 “In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
-
10-13-2013, 04:54 PM #398AprilGuest
Court Allows NSA to Keep Collecting Phone Records

Print article Send a Tipfrom AP 12 Oct 2013 12 post a comment
(AP) Court allows NSA to keep collecting phone records
By KIMBERLY DOZIER
AP Intelligence Writer
WASHINGTON
The secret U.S. court that governs surveillance of terrorist and foreign espionage targets is authorizing the National Security Agency to keep collecting U.S. phone records.
The director of national intelligence, James R. Clapper, on Friday made public the continuation of the records collection, as part of the Obama administration's campaign to better explain how U.S. intelligence uses U.S. data. At one time Clapper himself told Congress his officers do not collect such data.
Leaks by former NSA systems analyst Edward Snowden revealed the bulk collection of millions of U.S. phone logs showing who Americans called and for how long. That prompted privacy activists and lawmakers to push for an ongoing review of the Foreign Intelligence Surveillance Act, which allows such data collection.
http://cdn.breitbart.com/Big-Governm...-phone-records
-
10-15-2013, 12:23 AM #399Senior Member


- Join Date
- May 2007
- Location
- South West Florida (Behind friendly lines but still in Occupied Territory)
- Posts
- 117,088
Dianne Feinstein Defends NSA Spying Because… Well, She Isn’t Sure
October 14, 2013 by Personal Liberty News Desk
Rolling coverage of the ongoing government shutdown has pushed news of the myriad scandals which plagued the Administration of Barack Obama just a month ago from the front page of the American news psyche. But an op-ed by Senator Dianne Feinstein (D-Calif.) in the Sunday edition of The Wall Street Journal makes clear that, while the government may be shut down, America’s leaders are intent on justifying the continuance of their transgressions against the American public.
In her piece, Feinstein, who chairs the Senate Intelligence Committee, set about telling Americans why the publically unpopular National Security Agency data collection efforts revealed by whistle-blower Edward Snowden are important in protecting the Nation against terror attacks.
Her attempt to justify the massive privacy intrusions carried out by the NSA can be broken down into a few sections which strike at what appear to be her two main points: The world is full of terrorists, and the NSA works.
Here are some key points of Feinstein’s argument in her piece “The NSA’s Watchfulness Protects America: If today’s call-records program had been in place in before 9/11, the terrorist attacks likely would have been prevented.”
Feinstein’s ThesisMy answer: The program—which collects phone numbers and the duration and times of calls, but not the content of any conversations, names or locations—is necessary and must be preserved if we are to prevent terrorist attacks.Terror!
Feinstein argues that intrusive government surveillance could have averted the 9/11 terror attacks. She also notes other attacks that the government claims to have thwarted with its data collection efforts in the years since 9/11.In the summer of 2001, the CIA’s then-director, George Tenet, painted a dire picture for members of the Senate Intelligence Committee when he testified about the terrorist threat posed by al Qaeda. As Mr. Tenet later told the 9/11 Commission, “the system was blinking red” and by late July of that year, it could not “get any worse.”But, as one Gawker writer points out, “Huh. So… the CIA did issue dire warnings prior to 9/11, although the NSA’s program was not in place at that time. This directly contradicts Feinstein’s point about the necessity of the NSA’s phone spying. Paging the editing department.”
A similar level of concern emerged in July 2013, when the Senate Intelligence Committee was briefed on the al Qaeda threat that led the State Department to close an unprecedented 19 American diplomatic facilities across Africa and the Middle East.
The NSA Says The Program WorksWorking in combination, the call-records database and other NSA programs have aided efforts by U.S. intelligence agencies to disrupt terrorism in the U.S. approximately a dozen times in recent years, according to the NSA. This summer, the agency disclosed that 54 terrorist events have been interrupted—including plots stopped and arrests made for support to terrorism. Thirteen events were in the U.S. homeland and nine involved U.S. persons or facilities overseas. Twenty-five were in Europe, five in Africa and 11 in Asia.In other words, “who’s watching the watchers” doesn’t apply here. The NSA says it works, so it must work.
These figures show that the NSA programs are a key component of our counterterrorism efforts at home and abroad because they develop intelligence for our allies about terrorists operating within their borders.
Oh Yeah, and… Terror!!!The U.S. must remain vigilant against terrorist attacks against the homeland. Al Qaeda in the Arabian Peninsula (AQAP), considered the world’s most capable and dangerous terrorist organization, is determined to attack the United States. As we have seen since the “underwear bomber” attempted to blow up an airliner over Detroit on Christmas Day 2009, AQAP has developed nonmetallic bombs that can elude airport screeners, and the organization’s expert bomb maker, Ibrahim al-Asiri, remains at large.Evil doers with nonmetallic bombs, therefore spying on all Americans warranted.
A Couple of Things Left Unmentioned in Feinstein’s NSA Defense
- The Boston Marathon Bombing
- The Attacks On the U.S. Consulate in Benghazi, Libya
Filed Under: Liberty News, Staff Reports
http://personalliberty.com/2013/10/1...she-isnt-sure/
Join our efforts to Secure America's Borders and End Illegal Immigration by Joining ALIPAC's E-Mail Alerts network (CLICK HERE)
-
10-15-2013, 03:52 AM #400Senior Member


- Join Date
- May 2007
- Location
- South West Florida (Behind friendly lines but still in Occupied Territory)
- Posts
- 117,088
Patriot Act Author Calls For Clapper's Prosecution And Rein In NSA Abuses
 Submitted by Tyler Durden on 10/12/2013 19:58 -0400
Submitted by Tyler Durden on 10/12/2013 19:58 -0400
Submitted by Michael Krieger of Liberty Blitzkrieg blog,
In an interesting twist of irony, one of the Congressman most instrumental in the destruction of civil liberties in these United States due to his authorship of the Patriot Act, Jim Sensenbrenner (R-Wisc.), is now leading the charge to rein in NSA abuses. His disgust with the NSA became clear back in early June when he wrote an impassioned letter to Attorney General Eric Holder criticizing the illegal NSA activity happening behind the scenes. The key point here is that Mr. Sensenbrenner strongly believes that these guys are misinterpreting the legislation he wrote to justify everything they are doing. As such, he and others are proposing legislation to make it crystal clear what is and what is not appropriate surveillance.
Not only that, he is also calling for the prosecution of James Clapper the current Director of National Intelligence, who perjured himself in front of Congress earlier this year. Mr. Sensnbrenner said:
Oversight only works when the agency that oversight is directed at tells the truth, and having Mr Clapper say he gave the least untruthful answer should, in my opinion, have resulted in a firing and a prosecution.
This guy means business. More from the Guardian:
The conservative Republican who co-authored America’s Patriot Act is preparing to unveil bipartisan legislation that would dramatically curtail the domestic surveillance powers it gives to intelligence agencies.
Congressman Jim Sensenbrenner, who worked with president George W Bush to give more power to US intelligence agencies after the September 11 terrorist attacks, said the intelligence community had misused those powers by collecting telephone records on all Americans, and claimed it was time “to put their metadata program out of business”.
His imminent bill in the House of Representatives is expected to be matched by a similar proposal from Senate judiciary committee chair Patrick Leahy, a Democrat. It pulls together existing congressional efforts to reform the National Security Agency in the wake of disclosures by whistleblower Edward Snowden.
It seeks to limit the collection of phone records to known terrorist suspects; to end “secret laws” by making courts disclose surveillance policies; to create a special court advocate to represent privacy interests; and to allow companies to disclose how many requests for users’ information they receive from the USA. The bill also tightens up language governing overseas surveillance to remove a loophole which it has been abused to target internet and email activities of Americans.
In July, a temporary measure to defund the NSA bulk collection programme was narrowly defeated in a 217 to 205 vote in the House, but Sensenbrenner said the appetite for greater privacy protections had only grown since.
Instead, the main opposition to Sensenbrenner and Leahy’s twin-pronged effort is likely to come from the chair of the Senate intelligence committee, Dianne Feinstein, who is supportive of the NSA but who has proposed separate legislation focusing on greater transparency and checks rather than an outright ban on bulk collection.
Of course Feinstein is going to push to block real NSA restrictions, she is one of the most authoritarian members of Congress, not to mention married to a gigantic crony capitalist, fraud artist.
Sensenbrenner also called for the prosecution of Obama’s director of national intelligence, James Clapper, who admitted misleading the Senate intelligence committee about the extent of bulk collection of telephone records.
“Oversight only works when the agency that oversight is directed at tells the truth, and having Mr Clapper say he gave the least untruthful answer should, in my opinion, have resulted in a firing and a prosecution,” said the congressman.
Sensenbrenner also called for the prosecution of Obama’s director of national intelligence, James Clapper, who admitted misleading the Senate intelligence committee about the extent of bulk collection of telephone records.
“Oversight only works when the agency that oversight is directed at tells the truth, and having Mr Clapper say he gave the least untruthful answer should, in my opinion, have resulted in a firing and a prosecution,” said the congressman.
The main thrust of the bill would tighten section 215 of the Patriot Act to limit the collection of business records such as telephone metadata, to instances where the NSA was able to convince courts set up under the Foreign Intelligence Surveillance Act (Fisa) that the target was “an agent of a foreign power”, was “subject of an investigation” or thought to be “in contact with an agent of a foreign power”.
“We had thought that the 2006 amendment, by putting the word ‘relevant’ in, was narrowing what the NSA could collect. Instead, the NSA convinced the Fisa court that the relevance clause was an expansive rather than contractive standard, and that’s what brought about the metadata collection, which amounts to trillions of phone calls.”
“The haystack approach missed the Boston marathon bombing, and that was after the Russians told us the Tsarnaev brothers were bad guys,” added Sensenbrenner.
Since we know that the NSA hasn’t actually stopped any terrorist attacks, it’s even more disturbing to realize that they couldn’t even stop the only one (Boston) that did happen. What are these guys even doing?
Full article here.
http://www.zerohedge.com/news/2013-1...ign-nsa-abusesJoin our efforts to Secure America's Borders and End Illegal Immigration by Joining ALIPAC's E-Mail Alerts network (CLICK HERE)


 27Likes
27Likes LinkBack URL
LinkBack URL About LinkBacks
About LinkBacks
 Reply With Quote
Reply With Quote






VIDEO: 120 Illegal Aliens Arrested on Houston Streets in One Day
11-03-2025, 08:10 PM in illegal immigration News Stories & Reports