Results 341 to 350 of 582
Thread Information
Users Browsing this Thread
There are currently 1 users browsing this thread. (0 members and 1 guests)
-
08-23-2013, 06:46 PM #341
August 23, 2013 | By Mark M. Jaycox
Three Illusory "Investigations" of the NSA Spying Are Unable to Succeed
https://www.eff.org/deeplinks/2013/0...unable-succeed
Since the revelations of confirmed National Security Agency spying in June, three different "investigations" have been announced. One by the Privacy and Civil Liberties Oversight Board (PCLOB), another by the Director of National Intelligence, Gen. James Clapper, and the third by the Senate Intelligence Committee, formally called the Senate Select Committee on Intelligence (SSCI).
All three investigations are insufficient, because they are unable to find out the full details needed to stop the government's abuse of Section 215 of the PATRIOT Act and Section 702 of the Foreign Intelligence Surveillance Act. The PCLOB can only request—not require—documents from the NSA and must rely on its goodwill, while the investigation led by Gen. Clapper is led by a man who not only lied to Congress, but also oversees the spying. And the Senate Intelligence Committee—which was originally designed to effectively oversee the intelligence community—has failed time and time again. What's needed is a new, independent, Congressional committee to fully delve into the spying.
The PCLOB: Powerless to Obtain Documents
The PCLOB was created after a recommendation from the 9/11 Commission to ensure civil liberties and privacy were included in the government's surveillance and spying policies and practices.
But it languished. From 2008 until May of this year, the board was without a Chair and unable to hire staff or perform any work. It was only after the June revelations that the President asked the board to begin an investigation into the unconstituional NSA spying. Yet even with the full board constituted, it is unable to fulfill its mission as it has no choice but to base its analysis on a steady diet of carefully crafted statements from the intelligence community.
As we explained, the board must rely on the goodwill of the NSA's director, Gen. Keith Alexander, and Gen. Clapper—two men who have repeatedly said the NSA doesn't collect information on Americans.
In order to conduct a full investigation, the PCLOB will need access to all relevant NSA, FBI, and DOJ files. But the PCLOB is unable to compel testimony or documents because Congress did not give it the same powers as a Congressional committee or independent agency. This is a major problem. If the NSA won't hand over documents to Congress, then it will certainly not give them to the PCLOB.
The Clapper Investigation: Overseen by a Man Accused of Lying to Congress
The second investigation was announced by President Obama in a Friday afternoon news conference. The President called for the creation of an "independent" task force with "outside experts" to make sure "there absolutely is no abuse in terms of how these surveillance technologies are used." Less than two days later, the White House followed up with a press release announcing the task force would be led by Gen. Clapper and would also report to him. What's even worse: the task force was not tasked with looking at any abuse. It was told to focus on how to "protect our national security and advance our foreign policy." And just this week, ABC News reported the task force will be full of thorough Washington insiders--not "outside experts." For instance, one has advocated the Department of Homeland Security be allowed to scan all Internet traffic going in and out of the US. And another, while a noted legal scholar on regulatory issues, has written a paper about government campaigns to infiltrate online groups and activists. In one good act, the White House selected Peter Swire to be on the task force. Swire is a professor at Georgia Tech and has served as the White House's first ever Chief Privacy Officer. Recently, he signed an amicus brief in a case against the NSA spying by the Electronic Privacy Information Center arguing that the NSA’s telephony metadata program is illegal under Section 215 of the PATRIOT Act. Despite this, and at the end of a day, a task force led by General Clapper full of insiders,—and not directed to look at the extensive abuse—will never get at the bottom of the unconstitutional spying.
The Senate Intelligence Committee Has Already Failed
The last "investigation" occurring is a "review" led by the Senate Intelligence Committee overseeing the intelligence community. But time and time again the committee has failed at providing any semblance of oversight. First, the chair and ranking member of the committee, Senators Dianne Feinstein (CA) and Saxby Chambliss (GA), respectively, are stalwart defenders of the NSA and its spying activities. They have both justified the spying, brushed aside any complaints, and denied any ideas of abuse by the NSA.
Besides defending the intelligence community, the committee leadership have utterly failed in oversight—the reason why the Senate Intelligence Committee was originally created by the Church Committee. As was revealed last week, Senator Feinstein was not shown or even told about the thousands of violations of the spying programs in NSA audits of the programs. This is in direct contradiction to her statements louting the "robust" oversight of the Intelligence Committee. Lastly, the committee is prone to secrets and hiding behind closed doors: this year, the Senate Intelligence Committee has met publicly only twice. What's clear is that the Intelligence Committee has been unable to carry out its oversight role and fresh eyes are needed to protect the American people from the abuses of the NSA.
A New Church Committee
All three of these investigations are destined to fail. What's needed is a new, special, investigatory committee to look into the abuses of by the NSA, its use of spying powers, its legal justifications, and why the intelligence committees were unable to rein in the spying. In short, we need a contemporary Church Committee. It's time for Congress to reassert its oversight capacity. The American public must be provided more information about the NSA's unconstitutional actions and the NSA must be held accountable. Tell your Congressmen now to join the effort.“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
-
08-23-2013, 07:02 PM #342
NSA paid millions to cover Prism compliance costs for tech companies
• Top-secret files show first evidence of financial relationship
• Prism companies include Google and Yahoo, says NSA
• Costs were incurred after 2011 Fisa court ruling
- Ewen MacAskill in New York
- The Guardian, Thursday 22 August 2013
- Jump to comments (…)
 The material provides the first evidence of a financial relationship between the tech companies and the NSA.
The material provides the first evidence of a financial relationship between the tech companies and the NSA.
The National Security Agency paid millions of dollars to cover the costs of major internet companies involved in the Prism surveillance program after a court ruled that some of the agency's activities were unconstitutional, according to top-secret material passed to the Guardian.
The technology companies, which the NSA says includes Google, Yahoo, Microsoft and Facebook, incurred the costs to meet new certification demands in the wake of the ruling from the Foreign Intelligence Surveillance (Fisa) court.
The October 2011 judgment, which was declassified on Wednesday by the Obama administration, found that the NSA's inability to separate purely domestic communications from foreign traffic violated the fourth amendment.
While the ruling did not concern the Prism program directly, documents passed to the Guardian by whistleblower Edward Snowden describe the problems the decision created for the agency and the efforts required to bring operations into compliance. The material provides the first evidence of a financial relationship between the tech companies and the NSA.
The intelligence agency requires the Fisa court to sign annual "certifications" that provide the legal framework for surveillance operations. But in the wake of the court judgment these were only being renewed on a temporary basis while the agency worked on a solution to the processes that had been ruled illegal.
An NSA newsletter entry, marked top secret and dated December 2012, discloses the huge costs this entailed. "Last year's problems resulted in multiple extensions to the certifications' expiration dates which cost millions of dollars for Prism providers to implement each successive extension – costs covered by Special Source Operations," it says.
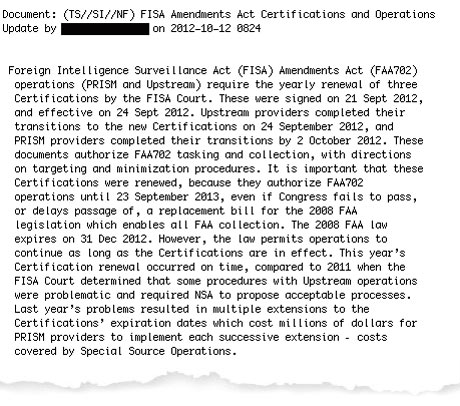 An NSA newsletter entry dated December 2012 disclosing the costs of new certification demands. Photograph: guardian.co.uk Special Source Operations, described by Snowden as the "crown jewel" of the NSA, handles all surveillance programs, such as Prism, that rely on "corporate partnerships" with telecoms and internet providers to access communications data.
An NSA newsletter entry dated December 2012 disclosing the costs of new certification demands. Photograph: guardian.co.uk Special Source Operations, described by Snowden as the "crown jewel" of the NSA, handles all surveillance programs, such as Prism, that rely on "corporate partnerships" with telecoms and internet providers to access communications data.
The disclosure that taxpayers' money was used to cover the companies' compliance costs raises new questions over the relationship between Silicon Valley and the NSA. Since the existence of the program was first revealed by the Guardian and the Washington Post on June 6, the companies have repeatedly denied all knowledge of it and insisted they only hand over user data in response to specific legal requests from the authorities.
An earlier newsletter, which is undated, states that the Prism providers were all given new certifications within days of the Fisa court ruling. "All Prism providers, except Yahoo and Google, were successfully transitioned to the new certifications. We expect Yahoo and Google to complete transitioning by Friday 6 October."
 An earlier undated newsletter after the Fisa court ruling on certifications. Photograph: guardian.co.uk The Guardian invited the companies to respond to the new material and asked each one specific questions about the scale of the costs they incurred, the form of the reimbursement and whether they had received any other payments from the NSA in relation to the Prism program.
An earlier undated newsletter after the Fisa court ruling on certifications. Photograph: guardian.co.uk The Guardian invited the companies to respond to the new material and asked each one specific questions about the scale of the costs they incurred, the form of the reimbursement and whether they had received any other payments from the NSA in relation to the Prism program.
A Yahoo spokesperson said: "Federal law requires the US government to reimburse providers for costs incurred to respond to compulsory legal process imposed by the government. We have requested reimbursement consistent with this law."
Asked about the reimbursement of costs relating to compliance with Fisa court certifications, Facebook responded by saying it had "never received any compensation in connection with responding to a government data request".
Google did not answer any of the specific questions put to it, and provided only a general statement denying it had joined Prism or any other surveillance program. It added: "We await the US government's response to our petition to publish more national security request data, which will show that our compliance with American national security laws falls far short of the wild claims still being made in the press today."
Microsoft declined to give a response on the record.
The responses further expose the gap between how the NSA describes the operation of its Prism collection program and what the companies themselves say.
Prism operates under section 702 of the Fisa Amendments Act, which authorises the NSA to target without a warrant the communications of foreign nationals believed to be not on US soil.
But Snowden's revelations have shown that US emails and calls are collected in large quantities in the course of these 702 operations, either deliberately because the individual has been in contact with a foreign intelligence target or inadvertently because the NSA is unable to separate out purely domestic communications.
Last week, the Washington Post revealed documents from Snowden that showed the NSA breached privacy rules thousands of times a year, in the face of repeated assurances from Barack Obama and other senior intelligence figures that there was no evidence of unauthorised surveillance of Americans.
The newly declassified court ruling, by then chief Fisa judge John Bates, also revealed serious issues with how the NSA handled the US communications it was sweeping up under its foreign intelligence authorisations.
The judgment revealed that the NSA was collecting up to 56,000 wholly US internet communications per year in the three years until the court intervened. Bates also rebuked the agency for misrepresenting the true scope of a major collection program for the third time in three years.
The NSA newsletters say the agency's response to the ruling was to work on a "conservative solution in which higher-risk collection would be sequestered". At the same time, one entry states, the NSA's general counsel was considering filing an appeal.
The Guardian informed the White House, the NSA and the office of the director of national intelligence that it planned to publish the documents and asked whether the spy agency routinely covered all the costs of the Prism providers and what the annual cost was to the US.
The NSA declined to comment beyond requesting the redaction of the name of an individual staffer in one of the documents.
UPDATE: After publication, Microsoft issued a statement to the Guardian on Friday afternoon.
A spokesperson for Microsoft, which seeks reimbursement from the government on a case-by-case basis, said: "Microsoft only complies with court orders because it is legally ordered to, not because it is reimbursed for the work. We could have a more informed discussion of these issues if providers could share additional information, including aggregate statistics on the number of any national security orders they may receive."“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
-
08-25-2013, 10:25 PM #343AprilGuest
NSA Spied on Wives and Spouses at Times
Saturday, 24 Aug 2013 06:49 PM
By Cathy Burke



The massive resources of the National Security Agency — the nation's beleaguered spy agency — have sometimes been put to use eavesdropping on agents' love interests, The Wall Street Journal reports.
The NSA even gave such intelligence collection a name — LOVEINT. One unnamed official told the Journal the practice was infrequent — averaging roughly one per year.
But officials told the Journal LOVEINT was the most willful misconduct by NSA workers.
Each instance of LOVEINT spying was against a spouse or partner, and involved overseas communications, the Journal reported. Each was met with "administrative action of discipline," the Journal reported.
Most were self-reported, including those reported during polygraph examinations.
In a statement, NSA said Friday there'd been “very rare” instances of willful violations of any kind in the past 10 years, and that none have violated key surveillance laws.
“NSA has zero tolerance for willful violations of the agency’s authorities” and responds “as appropriate," the statement said.
Democratic California Sen. Dianne Feinstein, who chairs the Senate intelligence committee, told the Journal the agency made Congress aware of "isolated cases" that took place about once a year over the last decade.
“Clearly, any case of noncompliance is unacceptable, but these small numbers of cases do not change my view that NSA takes significant care to prevent any abuses and that there is a substantial oversight system in place,” she said. “When errors are identified, they are reported and corrected.”
Media reports say more spying disclosures from former security contractor Edward Snowden are expected to be published by both The Guardian and The New York Times in the coming weeks, according to The Daily Mail.
http://www.newsmax.com/Newsfront/NSA...8/24/id/522074
-
08-26-2013, 03:58 PM #344Senior Member


- Join Date
- May 2007
- Location
- South West Florida (Behind friendly lines but still in Occupied Territory)
- Posts
- 117,088
Obama Picks Cass Sunstein, America’s Joseph Goebbles, to Serve on the NSA Oversight Panel
Posted on August 25, 2013
“It is the absolute right of the state to supervise the formation of public opinion.”
“We shall go down in history as the greatest statesmen of all time, or as the greatest criminals”
- Joseph Goebbles, Head of Hitler’s Ministry for Public Enlightenment and Propaganda
Only under the Obama Presidency, in which every appointment, minor or major, is handed only to the most corrupt, devious crony to be found, can a man like Cass Sunstein be appointed to serve on the NSA oversight panel. Cass is a noted propagandist, who has advocated that government agents should infiltrate groups and discussions that push “conspiracy theories” (read my article on how to know if you are a conspiracy theorist) in order to delegitimize them. But don’t take my word for it.
The Washington Post wrote the following a couple of days ago:
The Obama administration is reportedly proposing Cass Sunstein as a member of a panel to review the surveillance practices of the National Security Agency (NSA), among other former White House and intelligence staffers. Sunstein was the head of the White House’s Office of Information and Regulatory Affairs until last year, when he returned to teaching at Harvard Law School.
While at Harvard in 2008, Sunstein co-authored a working paper that suggests government agents or their allies “cognitively infiltrate” conspiracy theorist groups by joining ”chat rooms, online social networks or even real-space groups” and influencing the conversation.
The paper also suggests that the government “formally hire credible private parties to engage in counterspeech.” That sounds an awful lot like the 50 Cent Party of online commentators who are paid per comment by the Chinese communist party to sway public opinion.
This is a great time to watch one of my favorite We are Change videos. The one where Luke Rudkowski corners Sunstein and he tries to squirm away. Enjoy!
What a guy. Just make Summers head of the Federal Reserve and get it over with already.
In Liberty,
Mike
Follow me on Twitter!
http://libertyblitzkrieg.com/2013/08...ersight-panel/
Join our efforts to Secure America's Borders and End Illegal Immigration by Joining ALIPAC's E-Mail Alerts network (CLICK HERE)
-
08-26-2013, 07:52 PM #345Senior Member


- Join Date
- May 2007
- Location
- South West Florida (Behind friendly lines but still in Occupied Territory)
- Posts
- 117,088
New Government Spying Allegations - Report: NSA Bugged U.N, Headquaters In NYC
Where does this end? Is this just another phoney scandal?
http://patriotaction.net/video/video...sg_share_videoJoin our efforts to Secure America's Borders and End Illegal Immigration by Joining ALIPAC's E-Mail Alerts network (CLICK HERE)
-
08-28-2013, 11:47 PM #346AprilGuest
Lets face it EVERYTHING is bugged.....we are the Truman show.

-
09-01-2013, 01:46 PM #347
What’s the NSA picking out of your phone calls? Just ‘unvolunteered truths’
http://www.digitaltrends.com/mobile/...teered-truths/
By Andrew Couts — August 31, 2013

“The first program executed under Section 215 of the Patriot Act authorizes the collection of telephone metadata only,” said National Security Agency Director General Keith Alexander before House Intelligence Committed on June 18. Called for a rare public hearing on the NSA’s activities, Alexander uttered this statement just a week after the first of an ongoing set of top-secret leaks from former contractor Edward J. Snowden.
“As you’ve heard before, the metadata is only the telephone numbers, and contact, the time and date of the call, and the duration of that call,” Alexander continued. “This authority does not, therefore, allow the government to listen in on anyone’s telephone calls, even that of a terrorist.”
Predictive analytics is about revealing “unvolunteered truths” about people.
This is one of the prevailing storylines of the NSA and its defenders: The phone data collected, via Verizon, on virtually every man, woman, and phone-using child in the United States is nothing to fret about. As James Cole, the U.S. Deputy Attorney General put it during the same hearing, this metadata is exactly what “you show to many, many people within the phone company on a regular basis.” And yet, it is this same phone data that the NSA describes as crucial to its counterterrorism efforts. Let’s put aside for a moment the question of whether this dragnet data collection should happen, and ask a crucial question now that we know that it is: How is it possible that our phone metadata can be both innocuous and key to preventing, say, a group or individual from releasing poisonous gas in the New York City subway system?
A detailed answer to that question is classified. But based on what we know about the techniques available, an educated look at the possibilities points us in one direction: Predictive analytics.
Predictive analytics 101
Put entirely too simply, predictive analytics is a way of using “Big Data” techniques to predict possible outcomes, from results of presidential elections to the behavior of individual people. Depending on the application, predictive analytic data often includes demographic information, family and marital status, purchasing history, past weather patterns, business transaction histories, social media activity, website clicks, and, of course, telephone metadata, all of which help shape the map of an possible underlying reality.
“It’s about creating the ability to not only predict the future, but to influence it,” says Dr. Eric Siegel, author and founder of the Predictive Analytics World conferences. Further, he explains, it’s about revealing “unvolunteered truths” about people.
We know the NSA uses a variety of Big Data techniques and technologies, some of which the agency itself developed. The question then is: How are they using computer-assisted prediction?
What kinds of PA are other industries using
The public may have first become aware of predictive analytics in 2012, thanks to an article in The New York Times Magazine by Charles Duhigg. You may remember its bombshell anecdote: A father, having discovered coupons from Target offering discounts on baby gear sent to his young daughter, became outraged at the big box retailer for apparently trying to coerce the teenager into having sex. In fact, Target’s in-house data analysts had devised an algorithm that deduced whether particular customers were pregnant based on seemingly random changes in their purchasing habits.
The man later apologized to a Target manager; his daughter, he had since discovered, was due a few months later.
 Dr. Eric Siegel, founder of Predictive Analytics World conferences
Dr. Eric Siegel, founder of Predictive Analytics World conferences
This is, to date, the most visceral story we have about the powers of predictive analytics to derive facts about the world through data points and algorithms. But the fruits of predictive analytics are all around us, in less creepy forms: Netflix’s video recommendations, email spam filters, and Google Now, the technology giant’s virtual “personal assistant” for mobile devices, are all prime examples of predictive analytics at work. Rather than accurately predicting your due date, Google Now simply suggests a less congested route to your office.
In his aptly titled new book, Predictive Analytics: The Power to Predict Who Will Click, Buy, Lie or Die, Siegel lays out multiple poignant examples of how predictive analytics is predicting more than just which customers to send ads.
Hewlett-Packard, for instance, has developed a “Flight Risk” score for its employees that “foretells whether you’re likely to leave your job,” writes Siegel. Credit card companies accurately decipher which of us will make late payments. Parole boards figure out which inmates are most likely to commit another crime upon release. Cell phone companies figure out who and when to serve offers for discounted phones. The U.S. military uncovers which soldiers can handle the highly demanding life in the Special Forces. Life insurance providers predict when people will die. The list goes on – and is getting bigger by the day.
Future crime
In recent years, predictive analytics has entered a new realm: Policing. The highest-profile example of so-called “predictive policing” began in Santa Cruz, California, in 2011. Santa Clara University professor George Mohler generated predictions of crime “hot spots” based on historical crime data dating back to 2006, as well as new data added to the system every day. The result of that experiment is a propriety software called PredPol, created in 2012 by Mohler and P. Jeffrey Brantingham of UCLA, which has since been adopted by an increasing number of police departments around the country, including the Los Angeles Police Department.
While the term “predictive policing” inevitably conjures scenes from Minority Report, the reality has far more in common with the Waze traffic app than a dystopian future envisioned by three sun-deprived creatures in a vat of KY Jelly. In other words, PredPol does not let officers predict who will commit a crime, but where a crime will likely happen, regardless of who commits it.
PredPol is designed to be “completely blind to people,” says Zach Friend, a Santa Cruz district supervisor and police consultant, who spearheaded the development of PredPol. “The only four inputs into the system are date, time, crime type, and location.”

Police have long used “hot spot” mapping tools, which rely upon historical crime data to help departments pinpoint problem areas. PredPol is the next evolution in hot spot policing. Think of it as a traditional hot spot map that’s updating in real time and deploying officers to specific locations at specific times where and when a specific crime is deemed likely.
Crime data can often be sent to patrol cars as it comes in from victims, giving officers a birds eye view of the surrounding criminal landscape, as it evolves minute by minute.
Powerful though predictive policing may be, the limitation imposed on the types of data used in crime prediction is a key component to preventing PredPol from edging into dangerous territory, says Friend.
“I wouldn’t want to say that ‘Andrew’ is going to be [committing a specific crime],” says Friend. “That’s the Minority Report stuff. What we wanted instead is, ‘This location, this [latitude and longitude], 500-foot by 500-foot, has the highest probability of a burglary occurring during this shift. That’s all we wanted to do.”



The result of this tactic is a clear and continuous drop in crime. Santa Cruz saw burglaries drop by 19 percent in 2012, compared to the same period in 2011. And Los Angeles saw a 12 percent crime reduction soon after adopting PredPol. For all of 2012, overall crime in L.A. dropped by 1.4 percent, and violent crime dropped 8.2 percent.
While PredPol may be committed to limiting its system to time and location predictions, other data scientists have begun to take the technology a step further. According to Bloomberg News, Jim Adler, a former chief privacy officer for data broker Intelius, has created a computer model that can “accurately” predict whether an individual will commit a felony. Adler’s software initially made such predictions using a small number of telling data points, including gender, eye and skin color, traffic citations, criminal history, and “whether the individual has tattoos,” according to Bloomberg.
Predictions and the NSA
The rise of PredPol and other predictive policing efforts opens a window into what kinds of predictive tools the NSA may have at its disposal, and possibly how the spy agency uses those tools. For example, during the wars in Iraq and Afghanistan, the NSA utilized predictive models and other Big Data tools created by Silicon Valley company Palantir, to help connect the dots between known terrorists. According to government officials, Palantir’s technology even helped the military foil suicide bomber and roadside bomber attacks. Similar tools from Palantir are now used by the NSA, FBI, and CIA, which provided monetary backing to the company.
Some of the most powerful Big Data weapons were developed by the NSA itself. Chief among these is a system called Accumulo (pdf), which enables the NSA to map trillions of “nodes” (data points) and “edges” (connections between two or more data points), to create a discernable picture of the world’s communications using telephone metadata and internet traffic data collected under its now-controversial PRISM program.
According to a former international law enforcement agent, who requested anonymity due to ongoing professional obligations, the NSA can likely pinpoint suspicious communications activity using a predictive model, based on call records and Internet activity. The predictions may include deriving name, age, and gender data, or plotting likely future locations of individual people.

“Predictive analysis can often provide an idea of a subject’s age and gender based solely on call frequency and duration,” says the former agent. “Call duration and call frequency can be indicators of the significance of the callers to each other.”
In the same vein, geographic location data can be used “to make inferences about how criminal organizations operate,” says the agent. The same goes for terrorist groups, and the information can be used to deduce who is, and is not, working together on a potential plot, and where these actors might meet.
“Predictive analysis might indicate when it’s likely someone will show up at a particular locations,” says the agent. “Similarly, if a model gives a high probability that two individuals will meet in a time window and that window elapses, it can be an indication something has changed in their relationship. That might just be a flat tire, or it might be a falling-out.”
This information may be more valuable than direct surveillance – it’s spying 2.0
The inferences that can be obtained from predictive analytics don’t stop at who knows whom, however. According to Siegel, metadata, when fed into a well-tuned predictive model, can reveal more about a person and their intentions than a particular email or telephone conversation can. That is to say, predictive analytics allows the NSA or law enforcement agencies to derive actionable intelligence about targets that those targets have not disclosed, as well as information that may be more valuable than direct surveillance – it’s spying 2.0. “All these metadata things are the nuts and bolts – the sort of syntactic things known [about a person] that are often extremely revealing, not to mention a lot easier to deal with than the content, such as the typed message of an email or spoken words during a phone call,” says Siegel.
Siegel points out that, in any particular case, what a target says online or over the phone may prove to be “the most important of all [for an investigation], but are also not necessarily going to trump the metadata. And the metadata itself is going to make a huge difference.”
Metadata is so revealing because it is “easy to aggregate and analyze” in its raw form, according to Princeton Computer Science Prof. Edward Felten, in a recent court filing (pdf) written on behalf of the American Civil Liberties Union, which is suing (pdf) top Obama administration officials over the NSA’s collection of telephone metadata. Speech and the meaning of emails are, by contrast, much more difficult for computers to decipher, explains Felter. Add to that the significant increase in computing power and the plummeting cost of storage, and it’s possible for the NSA to easily garner “sensitive details about our everyday lives.”
 The NSA’s call metadata collection includes information on millions of Americans
The NSA’s call metadata collection includes information on millions of Americans
“Sophisticated computing tools permit the analysis of large datasets to identify embedded patterns and relationships, including personal details, habits, and behaviors,” writes Felten. “As a result, individual pieces of data that previously carried less potential to expose private information may now, in the aggregate, reveal sensitive details about our everyday lives – details that we had no intent or expectation of sharing.”
Compare this to the contents of a telephone call, which requires far more legwork to shape into a usable form. To analyze phone calls, “the government would first have to transcribe the calls and then determine which parts of the conversation are interesting and relevant,” explains Felten. “Assuming that a call is transcribed correctly, the government must still try to determine the meaning of the conversation: When a surveillance target is recorded saying ‘the package will be delivered next week,’ are they talking about an order they placed from an online retailer, a shipment of drugs being sent through the mail, or a terrorist attack? Parsing and interpreting such information, even when performed manually, is exceptionally difficult.”
To illustrate the powers of predictive analytics further, Felten lays out the following hypothetical:
“A young woman calls her gynecologist; then immediately calls her mother; then a man who, during the past few months, she had repeatedly spoken to on the telephone after 11pm; followed by a call to a family planning center that also offers abortions. A likely storyline emerges that would not be as evident by examining the record of a single telephone call.”
 NSA’s National Security Operations Center (NSOC), considered the center of the agency’s surveillance efforts
NSA’s National Security Operations Center (NSOC), considered the center of the agency’s surveillance efforts
Expand the telephone metadata collect over a period of months or years, and “many of these kinds of patterns will emerge once the collected phone records are subjected to even the most basic analytic techniques,” writes Felten. One can easily imagine how these techniques could be used to root out terrorists – or abused to spy on innocent people.
While we do not know the extent to which the NSA employs predictive modeling, officials have confirmed that it uses analytics for purposes similar to those outlined by Felter. As David Hurry, chief researcher for the NSA’s computer scientist division, told InformationWeek in 2012, “By bringing data sets together, it’s allowed us to see things in the data that we didn’t necessarily see from looking at the data from one point or another.”
Limitations of prediction
As powerful a tool as predictive analytics may be, its proprietors are quick to point out that it is not a silver bullet or a magic crystal ball.
“Generally, it’s not about accurate predictions,” says Siegel. “It’s about predicting significantly better than guessing. And that’s true for most applications, including law enforcement applications.”
Due to the limitations of predictive analytics, experts believe the NSA likely uses this Big Data technique as a jumping off point, or to enhance other parts of ongoing investigations.
“In my experience predictive modeling alone is not used to try to identify suspects or persons of interest,” says our unnamed source. “I can’t say that it has never been used that way. I have, however, used predictive modeling techniques in the course of medium- and long-term investigations opened for other reasons.”

Dean Abbott, founder of Abbott Analytics, says that the telephone metadata collected by the NSA may be “particularly useful in connecting high-risk individuals with others whom the NSA may not know beforehand are connected to the person of interest.” He adds, however, that predictive tools are likely only helpful when combined with a variety of other intelligence.
“These networks are usually best used as lead-generation engines,” writes Abbott on the Predictive Analytics World blog. Used this way, Abbott explains, predictive analytics and link analysis, such as the connections revealed through Accumulo, are “tremendously powerful” tools.
Drawing the line
Limited though predictive analytics may be, experts believe the potential for the technique to transform the nature of privacy and civil liberties is potent.
It is “fairly easy to predict” whether a criminal will repeat his pattern of crime, says John Elder, CEO of Elder Research Inc., the largest dedicated data analytics company in the U.S.. “Now, do you do like that Tom Cruise movie where you intercept somebody before they do the crime? That’s probably going too far in terms of allowing humans to take responsibility for their own actions.”
Big Data systems can also be tailored with privacy concerns built in. Accumulo, for example, has complex tagging system, known as Column Visibility, which the NSA built in to limit, at every level, which analysts can see what types of data through the use of security labels. It is likely that this aspect of Accumulo is what the NSA means when it refers to built-in civil liberty and privacy protections.
“Individual pieces of data … may now, in the aggregate, reveal sensitive details about our everyday lives.”
Some legal experts believe predictive modeling will force us to overhaul our privacy laws. In an expansive analysis of the legal implications of predictive policing published in 2004, University of the District of Columbia Assistant Professor of Law Andrew G. Ferguson, concludes that predictive analytics will change the ways in which police, such as the FBI or LAPD, apply the Fourth Amendment’s guarantee that law enforcement authorities must have “probable cause” before engaging in a search and/or seizure. “… Predictive policing forecasts will end up being seen as a ‘plus factor’ to find reasonable suspicion,” writes Ferguson. “However, the use of predictive policing forecasts alone will not constitute sufficient information to justify reasonable suspicion or probable cause for a Fourth Amendment seizure.”
In other words, by Ferguson’s assessment, predictive modeling may be used to unearth our innermost secrets – but the courts likely won’t let police search us on that intelligence alone.
For now, the debate over the NSA’s surveillance remains firmly focused on the collection of the data, not the ways in which it is likely used to derive more intelligence. In July, the U.S. House of Representatives narrowly defeated a bill that would have largely cut off the NSA’s ability to collect telephone metadata not directly connected to an ongoing investigation. And now, following recent revelations that the NSA violated privacy protection rules thousands of times in 2012, legislators are ramping up efforts to push back against the NSA with at least three new bills.
While we may see limitations on data collection by the NSA, the use of predictive analytics to help weed out criminals and terrorists – or even just to sell us diapers and cell phones – isn’t going anywhere, says Siegel.
“The power of predictive analytics should not be underestimated in the same way that the power of a knife should not be,” he says. “A knife could be used for good or for evil. I think outlawing knives entirely is not on the table.”“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
-
09-01-2013, 11:17 PM #348AprilGuest
Add to that the significant increase in computing power and the plummeting cost of storage, and it’s possible for the NSA to easily garner “sensitive details about our everyday lives.”
Which they have no right to, we are no longer living in the land of the free, it is the land of the stalked.....it is outrageous and nothing significant is being done to stop it IMO.
-
09-03-2013, 01:39 AM #349Senior Member


- Join Date
- May 2007
- Location
- South West Florida (Behind friendly lines but still in Occupied Territory)
- Posts
- 117,088
Join our efforts to Secure America's Borders and End Illegal Immigration by Joining ALIPAC's E-Mail Alerts network (CLICK HERE)
-
09-04-2013, 10:56 AM #350AprilGuest
Drug Agents Using Vast AT&T Database of Phone Records
Monday, 02 Sep 2013 05:00 PM


For at least six years, federal drug and other agents have had near-immediate access to billions of phone call records dating back decades in a collaboration with AT&T that officials have taken pains to keep secret, newly released documents show.
The program, previously reported by ABC News and The New York Times, is called the Hemisphere Project. It's paid for by the U.S. Drug Enforcement Administration and the Office of National Drug Control Policy, and it allows investigators armed with subpoenas to quickly mine the company's vast database to help track down drug traffickers or other suspects who switch cellphones to avoid detection.
The details of the Hemisphere Project come amid a national debate about the federal government's access to phone records, particularly the bulk collection of phone records for national security purposes. Hemisphere, however, takes a different approach from that of the National Security Agency, which maintains a database of call records handed over by phone companies as authorized by the USA Patriot Act.
"Subpoenaing drug dealers' phone records is a bread-and-butter tactic in the course of criminal investigations," Justice Department spokesman Brian Fallon said in an email. "The records are maintained at all times by the phone company, not the government. This program simply streamlines the process of serving the subpoena to the phone company so law enforcement can quickly keep up with drug dealers when they switch phone numbers to try to avoid detection."
The Associated Press independently obtained a series of slides detailing Hemisphere. They show the database includes not just records of AT&T customers, but of any call that passes through an AT&T switch.
The federal government pays the salaries of four AT&T employees who work in three federal anti-drug offices around the country to expedite subpoena requests, an Obama administration official told the AP on Monday. The official spoke on the condition of anonymity because he or she was not authorized to discuss the program, and said that two of the AT&T employees are based at the High Intensity Drug Trafficking Area office in Atlanta, one at the HIDTA office in Houston, and one at the office in Los Angeles.
The Hemisphere database includes records that date back to 1987, the official said, but typical narcotics investigations focus on records no older than 18 months.
To keep the program secret, investigators who request searches of the database are instructed to "never refer to Hemisphere in any official document," one of the slides noted. Agents are told that when they obtain information through a Hemisphere program subpoena, they should "wall off" the program by filing a duplicative subpoena directly to target's phone company or by simply writing that the information was obtained through an AT&T subpoena.
It wasn't immediately clear what percentage of U.S. calls are routed through AT&T switches and thus have records captured in Hemisphere. One slide says the program includes records "for a tremendous amount of international numbers that place calls through or roam on the AT&T network."
"While we cannot comment on any particular matter, we, like all other companies, must respond to valid subpoenas issued by law enforcement," AT&T spokesman Mark Siegel said in an email.
According to the slides, the program is useful for investigators trying to track down drug traffickers or other criminals who frequently change phones or use multiple phones. If agents become aware of a phone number previously used by a suspect, they can write an administrative subpoena, with no judicial oversight required, for records about that number.
Hemisphere analysts can track the number's call history or other characteristics and compare it to the history and characteristics of phones still in use — thus winnowing down a list of possible current phone numbers for the suspect, along with their location.
"Hemisphere results can be returned via email within an hour of the subpoenaed request and include (call detail records) that are less than one hour old at the time of the search," one slide said.
Marc Rotenberg, executive director of the Electronic Privacy Information Center, said the program raises several privacy concerns, including that if a query returns call records that are similar to, but not, those of the suspect, agents could be reviewing call records of people who haven't done anything wrong.
"One of the points that occurred to me immediately is the very strong suspicion that there's been very little judicial oversight of this program," Rotenberg said. "The obvious question is: Who is determining whether these authorities have been properly used?"
A Washington state peace activist named Drew Hendricks provided the slides to the AP on Monday. He said he obtained them in response to a series of public records requests he filed with West Coast police agencies, initially seeking information about a law enforcement conference that had been held in Spokane.
In the Northwest, the DEA and Department of Homeland Security make most of the Hemisphere requests through administrative subpoenas, one slide noted. Since late last year, AT&T has also accepted requests by court orders from local police agencies in Washington state.
As of June, Hemisphere had processed 679 requests from the Northwest High Intensity Drug Trafficking Area. And since 2007, the Los Angeles Hemisphere program had processed more than 4,400 requests.
In connection with the controversy over the NSA's sweeping up of call records, some lawmakers have suggested that phone companies store the records instead, and allow federal agents or analysts to request specific data when necessary.
"This way each query would require a specific government warrant before the FISA Court, and Americans would have more confidence that their privacy is being protected, while achieving the same national security results," Rep. Adam Schiff, D-Calif., said in a July 31 statement.
http://www.newsmax.com/Newsfront/AT-...9/02/id/523413


 27Likes
27Likes LinkBack URL
LinkBack URL About LinkBacks
About LinkBacks




 Reply With Quote
Reply With Quote


Volunteer ALIPAC Data Divers Needed
02-10-2026, 10:29 PM in General Discussion