Results 311 to 320 of 582
Thread Information
Users Browsing this Thread
There are currently 1 users browsing this thread. (0 members and 1 guests)
-
08-05-2013, 08:17 PM #311
Risk Assessment / Security & Hacktivism
Update: Does NSA know your Wi-Fi password? Android backups may give it to them
EFF technologist says "back up my data" exposes users' data to government spies.
http://arstechnica.com/security/2013...ve-it-to-them/
by Sean Gallagher - July 17 2013, 12:55pm EST
80
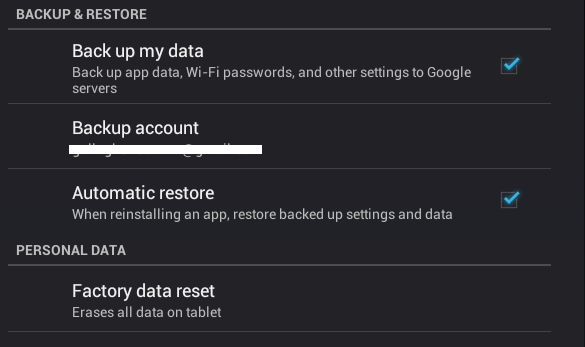 On by default on most newer Android devices, Google's Android backup stores your personal details in plaintext.
On by default on most newer Android devices, Google's Android backup stores your personal details in plaintext.
If you’re using Google’s “back up my data” feature for Android, the passwords to the Wi-Fi networks you access from your smartphone or tablet are available in plaintext to anyone with access to the data. And as a bug report submitted by an employee of the Electronic Frontier Foundation (EFF) on July 12 suggests, that leaves them wide open to harvesting by agencies like the NSA or the FBI.
“The ‘Back up my data’ option in Android is very convenient,” wrote Micah Lee, staff technologist at the EFF. “However, it means sending a lot of private information, including passwords, in plaintext to Google. This information is vulnerable to government requests for data.”
The Backup Manager app stores Android device settings in Google’s cloud, associated with the user account paired with the device; the Backup Manager interface is part of the core Android application API as well, so it can be used by other Android apps. Backup is turned on by default for Nexus devices and can push data such as MMS and SMS messages, browser bookmarks, call logs, and system settings—including Wi-Fi passwords—to Google’s cloud for retrieval in the event that a device is broken, lost, or stolen.
“Since backup and restore is such a useful feature, and since it's turned on by default,” wrote Lee, “it's likely that the vast majority of Android users are syncing this data with their Google accounts. Because Android is so popular, it's likely that Google has plaintext Wi-Fi passwords for the majority of password-protected Wi-Fi networks in the world.”
Most of those Wi-Fi networks have been mapped by Google as well. So it would be relatively trivial for an organization with access to backup data to match Wi-Fi network names and passwords with geolocation data. The result would be a partial map of where the targeted user has been as well as access to the networks his or her device has connected to in its travels.
Lee suggested that an easy fix to this privacy hole would be to encrypt the content of backups with a user’s Google credentials or a separate sync password. “I don't think it's rational to expect users to trust Google with their plaintext passwords when Google can be compelled to give this data to the US government when they request it,” he added.
Update: A Google spokesperson said in a conversation with Ars today that backup data is encrypted in transit from devices, and provided the following prepared statement from Google on the issue: “Our optional ‘Backup my data’ feature makes it easier to switch to a new Android device by using your Google Account and password to restore some of your previous settings. This helps you avoid the hassle of setting up a new device from scratch. At any point, you can disable this feature, which will cause data to be erased. This data is encrypted in transit, accessible only when the user has an authenticated connection to Google and stored at Google data centers, which have strong protections against digital and physical attacks.”
The spokesperson could not speak to how the data is encrypted in transit, or how the data was secured at rest.“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
-
08-07-2013, 11:53 AM #312
I did see this anywhere on the thread and I hope I didn't miss it.
Do you want to see how much privacy you really have. The conspicary folks that say facbook was government sponsored are coming to mind.
Go to the link below and Keep clicking on the picture.
This picture was taken with a camera 70,000 x 30,000 pixels (2100 MegaPixels).
It can identify a face in a multitude.
The cameras are not sold to the public and are being installed in strategic locations. (This one is in Canada)
Place the cursor in the multitude of people and left double click a couple times. It will continue to show the people much closer, when you double left click again. or click more if needed. Amazing!!
There were thousands of persons and yet one can spot and recognize any face.
Imagine what this means, both police and army have it.
http://www.gigapixel.com/image/gigapan-canucks-g7.htm
-
08-07-2013, 12:18 PM #313AprilGuest
WOW thanks NM!
-
08-07-2013, 12:20 PM #314AprilGuest
Obama cancels meeting with Putin over Snowden asylum tensions
Relationship between the two nations chills further as White House confirms president has pulled out of bilateral summit
- theguardian.com, Wednesday 7 August 2013 09.56 EDT

Obama with Vladimir Putin in Moscow in 2009. Photograph: Haraz N Ghanbari/AP
Barack Obama has pulled out of talks with Vladimir Putin that were due to be held in Russia next month, after Moscow granted asylum to the NSA whistleblower Edward Snowden.
The White House confirmed on Tuesday that it had decided to snub the Russian leader by pulling out of the planned bilateral summit in Moscow, but is expected to take part in the broader G20 meeting of international leaders in St Petersburg.
Its decision follows days of mounting rhetoric in Washington in response to Putin's decision to give temporary asylum to Snowden, who fled to Moscow after the Chinese government allowed him to leave Hong Kong rather than heed US calls for his arrest.
In a statement, the White House said that it had concluded there was "not enough recent progress in our bilateral agenda" to hold a US-Russia summit. It cited a lack of progress on arms control, trade, missile defence and human rights, and added: "Russia's disappointing decision to grant Edward Snowden temporary asylum was also a factor that we considered in assessing the current state of our bilateral relationship. Our cooperation on these issues remains a priority for the United States".A meeting between the defense secretary Chuck Hagel, the secretary of state John Kerry and their Russian counterparts will go ahead in Washington on Friday as planned.
In a separate announcement, the White House said Obama will visit Sweden instead, travelling to Stockholm the day before the St Petersburg summit. "Sweden is a close friend and partner to the United States," it said in a statement. "[It] plays a key leadership role on the international stage including in opening new trade and investment opportunities."
Speaking on Monday night, Obama said he was disappointed that Russia had allowed Swowden to stay instead of sending the former government contractor back to the US to face espionage charges.
In his first direct comments about Snowden since Russia's decision last week, the president said the situation reflected "underlying challenges" in dealing with Moscow. "There have been times where they slip back into cold war thinking and a cold war mentality," Obama said on NBC's Tonight Show.Snowden, an ex-NSA systems analyst, is accused of leaking details about highly secretive government surveillance programs. He spent several weeks in the transit zone of a Moscow airport before being granted asylum for a year.The White House has said Obama would attend the international summit in St Petersburg as it was important for the US to be represented at talks among global economic powers.
Obama also criticised a new Russian law cracking down on gay rights activism, saying he has "no patience for countries that try to treat gays and lesbians and transgendered persons in ways that intimidate them or are harmful to them".Russia has said it will enforce the law when it hosts the 2014 Winter Olympics in Sochi. Asked whether the law would affect the games, Obama said he believed Putin and Russia have "a big stake in making sure the Olympics work".
"I think they understand that for most of the countries that participate in the Olympics, we wouldn't tolerate gays and lesbians being treated differently," he said. Although the White House has chosen to focus on Snowden in recent days, Moscow's decision to grant him asylum is only the latest flashpoint in an increasingly strained relationship between the two countries.
Russia's refusal to join international condemnation of Syrian president Assad has been the most serious source of tension, hinting at the danger of Cold War-style proxy conflicts between the two nations and blocking US efforts to oust the Syrian leader.
The latest White House statement also cites arms control as a growing problem too. Obama's recent calls for fresh reductions in nuclear weapons fell on stony ground when he met Putin in a memorably chilly meeting on the sidelines of the G8 conference in Northern Ireland. Moscow worries US missile defence advances threaten to reduce the effectiveness of its nuclear deterrent.But hawks in Washington argue it is time for the White House to stop pretending it has a co-operative partner in the Kremlin and treat Russia as an adversary to be contained rather a country to be negotiated with.
"Now is the time to fundamentally rethink our relationship with Putin's Russia," said senator John McCain after Snowden was granted asylum. "We need to deal with the Russia that is, not the Russia we might wish for."
As well as completing Nato missile defence programmes regardless of concerns in Moscow, McCain is calling for an expansion of the Magnitsky Act, which applies US sanctions on Russian officials alleged to have taken part in human rights violations.
But the Magnitsky Act has also infuriated the Kremlin, which regards Washington as applying double standards on human rights, so such responses risk fuelling a spiral of tit-for-tat in retaliations likely to hurt both countries.
http://www.theguardian.com/world/201...nceled-snowden
-
08-07-2013, 07:26 PM #315
If Bruce Schneier ran the NSA, he’d ask a basic question: “Does it do any good?”
Ars asks a tech and legal all-star team how to fix America's security state.
http://arstechnica.com/tech-policy/2...t-do-any-good/
by Cyrus Farivar - Aug 7 2013, 9:00am EDT
101
 An aerial view of the NSA.
An aerial view of the NSA.
nsa.gov
NSA leaks
- German justice minister proposes ban for US firms that don’t abide privacy laws
- Update: Researchers say Tor-targeted malware phoned home to NSA
- Other agencies gripe that NSA, FBI shut them out of data sharing
- The sneaky switch that set the stage for the NSA’s call records program
- Seven telcos named as providing fiber optic cable access to UK spies
View all… For the last two months, we’ve all watched the news about the National Security Agency and its friends over at the Foreign Intelligence Surveillance Court (FISC), which approves secret orders on behalf of the NSA and other spy agencies. But more often than not, a lot of these articles take the same basic structure: documents provided by NSA leaker Edward Snowden show X, and then privacy advocates and civil libertarians decry X for Y reason.
That now raises the question, what would these privacy advocates do if they were put in charge of the NSA and the FISC? Or more specifically, what changes would they immediately enact at those two opaque institutions?
Ars checked in with some of the best technical and legal minds that we know: Bruce Schneier, one of the world’s foremost cryptographers, and Jennifer Granick, an attorney and director of Civil Liberties at Stanford University’s Center for Internet and Society. For a historical perspective, we chatted with Gary Hart, a former United States senator from Colorado who served on the Church Committee in 1976. Its recommendations led to the creation of the Foreign Intelligence Surveillance Act (FISA) and the FISC. We also looked at recent public statements by the Electronic Frontier Foundation (EFF) and the American Civil Liberties Union (ACLU).
Schneier, who has previously criticized the Department of Homeland Security, proposed the most radical changes.
“There’s a fundamental problem in that the issues are not with the NSA but with oversight,” he told Ars. “[There’s no way to] counterbalance the way [the NSA] looks at the world. So when the NSA says we want to get information on every American’s phone call, no one is saying: ‘you can’t do that.’ Without that, you have an agency that’s gone rogue because there is no accountability, because there is nothing checking their power.”
The way Schneier sees it, in an attempt to keep the operational details of the targets secret, the NSA (and presumably other intelligence agencies, too) has also claimed that it also needs to keep secret the legal justification for what it’s doing. “That’s bullshit,” Schneier says.
The famed computer scientist wants to apply traditionally open and public scrutiny to how the NSA operates.
“How much does this stuff cost and does it do any good?” he said. “And if they can’t tell us that, they don’t get approved. Let’s say the NSA costs $100 million annually and that an FBI agent is $100,000 a year. Is this worth 1,000 FBI agents? Or half and half? Nowhere will you find that analysis.”
For the record: the size of the NSA’s budget is officially classified as secret, but estimates put it at least at $8 to $10 billion annually—but his point stands. It’s nearly impossible to judge the effectiveness of federal spending of an unknown sum, whose tactics, legal justifications, and most importantly, outcomes, are completely hidden from the public.
“We deliberately have given ourselves an inefficient form of government and an inefficient form of policing because we recognize the dangers in giving people so much power without any oversight or accountability,” he concluded.
Similarly, former Senator Gary Hart said that the intelligence apparatus has ballooned out of control in the United States in recent years.
“The use of outside consultants [and] private companies by these dozen and a half intelligence agencies is out of hand,” Hart said. “We don’t know how many companies there are, how many people they employ. We do know there are 1 million Americans with top-secret clearance, and that’s way too much.”
Indeed, the Wall Street Journal recently reported that “as of last October, nearly five million people held government security clearances. Of that, 1.4 million held top-secret clearances.”
A black box
While Schneier had the broadest and most sweeping proposed changes, the other tech and legal experts that we spoke with focused more specifically on individual legal reforms, and they tended to agree on a few broad suggestions: halt untargeted blanket surveillance, restore a pre-2008 version of the Foreign Intelligence Surveillance Act (FISA) that required a probable cause-driven warrant to conduct foreign surveillance, and create additional FISC reforms such that its proceedings are more open and have more avenues for pushback.
Jennifer Granick was the first to admit that it’s difficult to know what reforms are necessary, because as Schneier pointed out, it’s impossible to know what precisely is being undertaken by the NSA and other intelligence agencies.
“We’re responding to a black box,” she said. “We don’t know the full story of what they’re doing. We don’t know the full story of how useful or not useful the various tools are. We don’t know what they do with the information. We’re responding to these fragmented amounts of information.”
Granick, like the EFF and ACLU, called for an immediate cessation to the bulk collection of all Americans’ records.
As the EFF writes:The starting point for NSA reform would be a definitive statement that court orders for bulk collection of information are not allowed and indeed are illegal. At all times, a specific person or specific identifier (like a phone number or e-mail address) or a reasonable, small, and well-cabined category (like a group on the terrorist list or member of a foreign spy service) must be specified in the context of an investigation. And a category like: “all records of all Verizon customers,” is neither reasonable, small, nor well-cabined.Similarly, the ACLU’s Jameel Jaffer testified before the Senate Judiciary Committee (PDF) on July 31, 2013:But the Fourth Amendment is triggered by the collection of information, not simply by the querying of it. The NSA cannot insulate this program from Fourth Amendment scrutiny simply by promising that Americans’ private information will be safe in its hands. The Fourth Amendment exists to prevent the government from acquiring Americans’ private papers and communications in the first place.Bringing back 2008
Because the metadata program vacuums up sensitive information about associational and expressive activity, it is also unconstitutional under the First Amendment. The Supreme Court has recognized that the government’s surveillance and investigatory activities have an acute potential to stifle association and expression protected by the First Amendment.
In 2008, Congress passed the FISA Amendment Acts, which loosened the restrictions as to who could be surveilled. As Jaffer recently told the Senate:Until Congress enacted the FISA Amendments Act, FISA generally prohibited the government from conducting electronic surveillance without first obtaining an individualized and particularized order from the FISA court. In order to obtain a court order, the government was required to show that there was probable cause to believe that its surveillance target was an agent of a foreign government or terrorist group. It was also generally required to identify the facilities to be monitored. The FISA Amendments Act allows the government to conduct electronic surveillance without indicating to the FISA Court whom it intends to target or which facilities it intends to monitor, and without making any showing to the court—or even making an internal executive determination— that the target is a foreign agent or engaged in terrorism. The target could be a human rights activist, a media organization, a geographic region, or even a country.Granick also argues that it sets a bad precedent for other countries, particularly those authoritarian regimes that we frown upon.
“We don’t want to give comfort to those nations that want to have free range [over their people's] data—we should have a warrant requirement and that should not be contingent on whether the person is a US person or not,” she said.
“Open and adversarial proceedings”
Finally, these legal experts would love to see a narrowing of what the FISC can and can’t do. Granick said that she’d like to see FISC’s scope narrowed so all it could do would be to “approve secret targets.”
“It cannot make secret interpretations of statute, and it cannot interpret what the 4th Amendment is or should be,” she said. “We should have an open and democratic process and not a secret court. I think that the court should not be playing the role of making legal decisions in any case. All they’re doing is approving secret targets. There’s a lesser role for an independent [ombudsman] or defendant’s advocate.”
That "lesser role" that she’s referring to is a position that former Sen. Gary Hart (D-CO) and others have suggested, which would make the FISC process more adversarial. At present, when the government comes to the FISC and asks to target a particular person—often times, getting help from the court’s staff to make it more palatable to the judge—there is no advocate for the target, which has led to a near-100 percent target approval rate. Hart has called for the creation of a “citizen’s ombudsman,” who would have adequate security clearance.
“But that individual would make the counter argument so the court would not just [have the government’s argument to consider], but the [ombudsman] would be calling into question what the government was putting forward,” he said.
Granick said that such an ombudsman position would not be necessary if all FISA did was approve secret targets—leaving the legal justification to other open courts.
The ACLU has agreed generally with these recommendations. As Jaffer testified:Congress should ensure that the government’s surveillance activities are subject to meaningful judicial review. It should clarify by statute the circumstances in which individuals can challenge government surveillance in ordinary federal courts. It should provide for open and adversarial proceedings in the FISC when the government’s surveillance applications raise novel issues of statutory or constitutional interpretation. It should also pass legislation to ensure that the state secrets privilege is not used to place the government’s surveillance activities beyond the reach of the courts.
Reader comments 101“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
-
08-08-2013, 10:32 PM #316
Pentagon considers employees unhappy with US policies a security threat
http://rt.com/usa/pentagon-threat-insider-program-232/
Published time: August 08, 2013 16:34 Get short URL

Tags
Intelligence, Military, Politics, Security, USA, WikiLeaks
The Pentagon is warning its employees to be on the look-out for colleagues who demonstrate an “unhappiness with US foreign policy,” visit family abroad and have financial problems – traits that classify someone as an “insider threat”.
Afraid that its federal employees could follow the footsteps of Army Private first class Bradley Manning, the Defense Department is taking long strides to find potential information leakers. As part of its “Insider Threat” program, which requires government workers to monitor and spy on each other, the Defense Information Systems Agency (DISA) has required staffers to sit through an online presentation that outlines traits qualifying someone as a “high threat”.
DISA defines insider risks as “threats from people who have access to the organization’s information systems and may cause loss of physical inventory, data, and other security risks,” the Huffington Post reports.

To help federal employees identify “high risk” individuals, the DISA created a “CyberAwareness Challenge”, which was posted in Oct. 2012 – one month before the Insider Threat policy was completed. One section of the security challenge requires employees to identify the threat levels of hypothetical individuals that they may encounter in their offices.
An example of a “high threat” individual is an Indian woman named Hema, who travels to India twice a year to visit family and who “speaks openly of unhappiness with US foreign policy.” This woman demonstrates an “adequate work quality” and had her car repossessed while at work.
“Based on her statements, this employee demonstrates divided loyalty,” the program explains. “Paired with her financial difficulties and foreign travel, she is a high threat.”

The training program encourages Pentagon staffers to “catch me if you can”, referring to individuals whose traits deem them more likely to leak sensitive information or put the country at risk.
Pentagon spokesman Lt. Col. Damien Pickart defended the program to the Huffington Post, arguing that it is valid “based on past examples of personnel who engaged in spying or treasonous acts.”
But Steven Aftergood, an expert on government secrecy at the Federation of American Scientists, said the training was “ignorant and clumsy”, since it scrutinizes individuals simply for expressing their right to free speech about US foreign policy, which not everyone agrees with completely.

"The item 'speaks openly of unhappiness with U.S. foreign policy' simply does not belong on the list," Aftergood said. "It is not a threat indicator. It could apply to most members of Congress, if not to most Americans. By presenting the matter this way, the slide suggests that overt dissent is a security concern. That is an error."
The Insider Threat program was first authorized in Oct. 2011, after Pfc. Bradley Manning sent classified information to the anti-secrecy website WikiLeaks. Manning is currently facing a maximum prison sentence of 90 years for releasing hundreds of thousands of documents, including field reports and logs from the Afghan and Iraq wars.
In an attempt to prevent information leaks, the DISA’s Insider Threat program urges government workers to spy on each other, facing hefty penalties if they fail to alert their superiors of a potential security breach. Threat indicators include stress, relationship issues, financial problems, odd work hours and random traveling. And an Indian woman like Hema, who visits her family twice a year, couldn’t make her car payments, and disagrees with the Obama administration’s foreign policy, is considered an example of a “high threat” individual that the Pentagon considers a danger to the United States.
 “In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
-
08-09-2013, 12:31 PM #317
Silent Circle Preemptively Shuts Down Encrypted Email Service To Prevent NSA Spying
http://techcrunch.com/2013/08/08/sil...nt-nsa-spying/
Josh Constine
posted yesterday
Comments

“We knew USG would come after us”. That’s why Silent Circle CEO Michael Janke tells TechCrunch his company shut down its Silent Mail encrypted email service. It hadn’t been told to provide data to the government, but after Lavabit shut down today rather than be “complicit” with NSA spying, Silent Circle told customers it has killed off Silent Mail rather than risk their privacy.
The Silent Circle blog posts explains “We see the writing the wall, and we have decided that it is best for us to shut down Silent Mail now.” It’s especially damning considering Silent Circle’s co-founder and president is Phil Zimmermann, the inventor of widely-used email encryption program Pretty Good Privacy.
Silent Circle reportedly had revenue increase 400% month-over-month in July after corporate enterprise customers switched to its services in hopes of avoiding surveillance. The company giddily told Forbes it planned to nearly double staff and significantly increase revenue this year in part thanks to the NSA’s practices coming to light. In light of those comments, today’s news about shutting down Silent Mail seems a bit sobering.
 Silent Circle’s other secure services including Silent Phone and Silent Text will continue to operate as they do all the encryption on the client side within users’ devices. But it explained that “Email that uses standard Internet protocols cannot have the same security guarantees that real-time communications has.” With too many opportunities for information and metadata leaks in the SMTP, POP3, and IMAP email protocols, the company believes there was no way to live up to its promise of total privacy.
Silent Circle’s other secure services including Silent Phone and Silent Text will continue to operate as they do all the encryption on the client side within users’ devices. But it explained that “Email that uses standard Internet protocols cannot have the same security guarantees that real-time communications has.” With too many opportunities for information and metadata leaks in the SMTP, POP3, and IMAP email protocols, the company believes there was no way to live up to its promise of total privacy.
In a statement to TechCrunch about whether the shut down was only because Silent Circle felt email was insecure, CEO Michael Janke tells us“It goes deeper than that. There are some very high profile people on Silent Circle- and I mean very targeted people- as well as heads of state, human rights groups, reporters, special operations units from many countries. We wanted to be proactive because we knew USG would come after us due to the sheer amount of people who use us- let alone the “highly targeted high profile people”. They are completely secure and clean on Silent Phone, Silent Text and Silent Eyes, but email is broken because govt can force us to turn over what we have. So to protect everyone and to drive them to use the other three peer to peer products- we made the decision to do this before men on [SIC] suits show up. Now- they are completely shut down- nothing they can get from us or try and force from us- we literally have nothing anywhere.”Silent Circle says it had been considering a more conservative slow shut-down of Silent Mail or ceasing to take on new customers, but was inspired to shut down by Lavabit.
That company was reportedly PRISM whistleblower Edward Snowden’s email provider, likely because of its claims of high security. But Lavabit was told by the government to turn over user data, and received a gag order preventing it from publicizing details of the situation. Today Lavabit owner Ladar Levison posted a note to the company’s site saying “I have been forced to make a difficult decision: to become complicit in crimes against the American people or walk away from nearly ten years of hard work by shutting down Lavabit.” He chose the latter.
The move has bolstered critics who are becoming increasingly vocal about how the U.S. government’s surveillance efforts are jeopardizing American technology businesses. They fear international customers may take their cloud business elsewhere in an attempt to avoid the NSA. Jennifer Granick, the Director of Civil Liberties at the Stanford Center for Internet and Society, wrote that ”the U.S. government, in its rush to spy on everybody, may end up killing our most productive industry. Lavabit may just be the canary in the coal mine.”
Now it seems that the negative impact won’t just be in the form of lost customers or businesses shut down upon receiving data demands. The destruction could reach as far as companies unwilling to even risk compromising their values. At this point, the nation’s best hope for reform of spying practices might be making a case that it hurts the economy.
Additional reporting by Gregory Ferenstein
Surveillance Magazine profiles the men and women setting the agenda for the security industry
Names: Mike Janke and Phil Zimmermann.
Company: Silent Circle.
Silent Circle is a mobile encryption pioneer, headquartered in Washington DC, and co-founded by Mike Janke, former Navy SEAL and best-selling author, and Phil Zimmermann, the inventor of PGP and one of the Top 50 Tech Visionaries and 2012 inductee into the Internet Hall of Fame.
Silent Circle provides an encrypted communications service (voice, video and text) that allows registered users to speak or send messages without fear of being intercepted. More and more relevant in the fall-out from PRISM of course, where the issue now is mobile privacy not just security, whether in business conversations (guarding against industrial espionage or the loss of valuable IP for example) or in our own personal lives.
Mike Janke
Former Navy SEAL sniper, best-selling author, privacy advocate, Special Operations communications expert, and founder/past CEO of SOC, a global defense & logistics firm. As a Privacy advocate, Mike works to bring secure communications to Human Rights Groups, deployed Military, Oppressed Citizens and international businesses around the world.
 Phil Zimmermann
Phil Zimmermann
Phil is the creator of PGP, the most widely used email encryption software in the world, and the Zfone/ZRTP secure VoIP standard. PC World named him one of the Top 50 Tech Visionaries of the last 50 years. He has received Privacy International’s Louis Brandeis Award, CPSR’s Norbert Weiner Award, the EFF Pioneer Award, the Chrysler Award for Innovation in Design, and inducted into the Internet Hall of Fame.
 Press Kit
Press Kit
More Articles
Videos
Press Releases
- June 25, 2013 - <acronym title="Google Page Ranking"><acronym title="Google Page Ranking"><acronym title="Google Page Ranking">PR</acronym></acronym></acronym> Newswire
- June 11, 2013 - <acronym title="Google Page Ranking"><acronym title="Google Page Ranking"><acronym title="Google Page Ranking">PR</acronym></acronym></acronym> Newswire
“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
-
08-09-2013, 03:34 PM #318
 Electronic Frontier Foundation
Electronic Frontier Foundation
Defending your rights in the digital world
Search form
Search
August 9, 2013 | By Morgan Weiland
Why Sen. Feinstein Is Wrong About Who’s a “Real Reporter”
During the Senate Judiciary Committee’s August 1 mark-up of the shield law bill aimed at protecting journalists’ sources, Sen. Dianne Feinstein (D-CA) reportedly objected to the definition of journalist provided in the bill as introduced, seeking to restrict the definition’s scope to apply only to “real reporters.” To achieve her misguided goal, Sen. Feinstein has put forward an amendment to S. 987 that would greatly exacerbate the problems with the definition of who’s a journalist that existed in the bill as introduced.
Her amendment, to be submitted for Sen. Dick Durbin (D-Il.) as well, not only retains the problematic requirement that a person “regularly” engage in journalism to enjoy shield law protections, but moreover adds new requirements that would make it especially difficult for self-publishers such as independent bloggers and citizen journalists to be protected under the law. Indeed, her new requirements for being either salaried or at least affiliated with a news “entity” seem to purposefully target these self-publishers.
These problems are rooted in the vagueness of many key terms in her definition of journalist. Indeed, most essential terms are not defined. While vagueness provides an interpretative battleground, self-publishing bloggers and citizen journalists are disadvantaged in this fight.
Three Roads to “Journalist” that All Go Nowhere
Feinstein’s amendment effectively advances a traditional vision of journalism through the three definitions of journalist that it provides, each of which requires that a person be affiliated with a journalistic “entity” or institution (including news websites and other digital news services, and other periodicals distributed digitally).
Specifically, the amendment requires that a journalist meet one of the following definitions:
- working as a “salaried employee, independent contractor, or agent of an entity that disseminates news or information;”
- either (a) meeting the prior definition “for any continuous three-month period within the two years prior to the relevant date” or (b) having “substantially contributed, as an author, editor, photographer, or producer, to a significant number of articles, stories, programs, or publications by an entity . . . within two years prior to the relevant date;” or
- working as a student journalist “participating in a journalistic publication at an institution of higher education.” (emphases added)1
There are problems with each of these three definitions. First, as we pointed out in our critique of the House’s bill, requiring that an individual is “salaried” is problematic because many people do journalism but do not do it as their primary source of income. Further, it is entirely unclear who or what an “agent” or “entity” is.
Second, for an individual to fall under the second, seemingly looser criteria, that individual must have distributed the news “by means of an entity.” (emphasis added)2 While this definition may cover freelancers, it is again unclear what it means to have “substantially contributed” to a “significant” amount of work of an “entity.” Indeed, for both the first and second definitions, essential terms are not defined—vagueness that, as we’ll see later, ultimately hurts independent bloggers and citizen journalists.
While the amendment’s inclusion of student journalists is laudable, it does nothing for those students who do not work for a “journalistic publication” at their college or university—or for those students the moment they graduate.
Still Requiring that Journalists “Regularly” Engage in Journalism
Additionally, Sen. Feinstein’s amendment retains the original Senate shield bill’s problematic requirement that individuals “regularly” do journalism to count as a journalist. Specifically, the amendment requires either:
- that individuals “engage[] in . . . the regular gathering, preparation, collection, photographing, recording, writing, editing, reporting or publishing on” matters of public interest; or
- that individuals “regularly conducted interviews, reviewed documents, captured images of events, or directly observed events.” (emphases added)3
As in the original Senate bill, the amendment fails to define what “regularly” means, vagueness that cuts against non-institutional journalists.
Vague Language Is Bad for Independent Bloggers, Citizen Journalists
Sen. Feinstein’s amendment is riddled with vague language, failing to define key terms including “agent,” entity,” “substantially contributed,” and “regularly”—on which the definition of who’s a journalist turns. Non-traditional journalists are at a disadvantage when the interpretative waters are muddy. Why? Because such vagueness invites interpretations that exclude those who are on the margins of status quo journalism, and who are often in a more vulnerable position and unable to hire legal counsel to sort through the law’s ambiguities. As a result, independent bloggers and citizen journalists would likely be interpreted out of Feinstein’s definition of journalist.
The very fact that developing a crisp, clear definition of journalist is difficult should signal to Congress that it might not be equipped to wade into the uncharted waters of deciding who is a journalist. But it’s a problem that Congress can easily avoid by linking shield law protections to the act of journalism, not the definition of who is journalist.“In questions of power…let no more be heard of confidence in man, but bind him down from mischief by the chains of the Constitution.” –Thomas Jefferson
-
08-11-2013, 07:40 PM #319AprilGuest
-
08-11-2013, 07:42 PM #320AprilGuest
WikiLeaks founder: Obama surveillance changes vindicate Edward Snowden
By Keith Laing - 08/10/13 10:40 AM ET
The founder of the WikiLeaks website said on Saturday that President Obama’s announcement of changes to the National Security Agency’s (NSA) surveillance program this week vindicated Edward Snowden’s release of information about the program.
“Today the President of the United States validated Edward Snowden’s role as a whistleblower by announcing plans to reform America’s global surveillance program,” WikiLeaks Founder Julian Assange said in a statement. “But rather than thank Edward Snowden, the president laughably attempted to criticize him while claiming that there was a plan all along, ‘before Edward Snowden,’” Assange continued. “The simple fact is that without Snowden’s disclosures, no one would know about the programs and no reforms could take place.”
Assange compared Snowden to former solider Bradley Manning, who was convicted of releasing classified information about the Iraq War, and Daniel Ellsberg, who released the Pentagon Papers during the Vietnam War in the 1970s.
“As Thomas Jefferson so eloquently once stated, ‘All tyranny needs to gain a foothold is for people of good conscience to remain silent,’” Assange said. “Luckily for the citizens of the world, Edward Snowden is one of those ‘people of good conscience’ who did not ‘remain silent,’ just as Pfc Bradley Manning and Daniel Ellsberg refused to remain silent.”
Obama said on Friday that he was planning to ask Congress to narrow and improve oversight of Section 215 of the Patriot Act, which allows the government to collect phone records, in response to criticism of the NSA’s surveillance programs. Obama also said he would ask Congress to carve out a role for civil libertarians in courts that give government agencies the warrants to grab data from private citizens and companies.
Assange accused the Department of Justice of “betraying two key principles that President Obama championed when he ran for office -- transparency and protection for whistleblowers.
“During his 2008 campaign, the president supported whistleblowers, claiming their ‘acts of courage and patriotism, which can sometimes save lives and often save taxpayer dollars, should be encouraged rather than stifled,’” Assange said. “Yet his administration has prosecuted twice as many whistleblowers than all other administrations combined.”
Obama said pointedly during a news conference on Friday that he did not think Snowden was a “patriot.”
http://thehill.com/blogs/blog-briefi...edward-snowden


 27Likes
27Likes LinkBack URL
LinkBack URL About LinkBacks
About LinkBacks




 Reply With Quote
Reply With Quote


Volunteer ALIPAC Data Divers Needed
02-10-2026, 10:29 PM in General Discussion